Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Discover how MOSIP's tools, components, and architecture come together.
The guiding foundation.
MOSIP is designed, developed, and implemented based on core principles that drive its effectiveness and adaptability. These principles ensure that MOSIP remains open, secure, interoperable, scalable, and inclusive, allowing it to meet the needs of diverse users and support the creation of accessible, digital identity systems globally.
Modular: Identity systems that serve unique needs with mutually exclusive technology bundles. Rather than a stand-alone solution offered to every adopting nation, MOSIP technology allows user countries to build custom workflows. Each functionality is built with independent microservices to provide flexibility and control.\
Open Source: Trusted & transparent technology, adhering to global standards. An open-source code repository, available on GitHub, encourages contributions from user communities and offers governments control over their ID systems. MOSIP also works with the Institute of Electrical and Electronics Engineers (IEEE), governments, and a commercial ecosystem to arrive at common Open Standards and Protocols. This makes MOSIP easy to integrate, interoperable, cost- and time-efficient.\
Vendor-Neutral: Offering the ability to integrate with a wide range of compliant technologies. In the setting up of a foundational digital ID system, it is critical that the platform, biometric devices, and system integrators, are able to integrate and function smoothly. Vendor-neutrality, maintained through the MOSIP Partner Programme and the establishment of the MOSIP Marketplace offers countries the ability to choose and change their technology solutions at any time and save precious time and financial resources.\
Private and Secure: Ensuring every individual is in control of their data. MOSIP is designed to keep data security and privacy in mind, ensuring that data is protected in flight and rest. Cryptographic encryption and zero knowledge architecture ensure that no sensitive data is stored on the MOSIP system. Governments of adopting nations have sovereign control over their ID systems, and data sharing only happens with the individual’s consent.\
Scalable: Designed to accommodate growth and changing needs. The platform is designed to be scalable, accommodating the growth of users and services. It can cater to large populations, support various regions, and integrate with multiple systems securely, without compromising performance. Its modular architecture allows it to easily expand and adapt to new requirements, making it suitable for both small-scale deployments and national level rollouts. This scalability ensures that MOSIP can serve diverse countries and populations with varying technological and infrastructural capabilities.\
Human-Centric: Technology for all. We aim to develop technology that can cater to diverse and varying requirements around the world, yet being human-centric. The team at MOSIP constantly strives to learn from on-ground experiences in adopting nations, to understand their context-specific requirements and provide adaptable solutions.\
Inclusive: Technology that leaves no one behind. With the mission of empowering lives all over the world, MOSIP continues to take steps toward being an inclusive platform. Ongoing collaborations with global universities, research organizations, and strong on-ground teams have sharpened our focus on developing technology that is unrestricted by gender, race, and economic status. Additionally, technology features allow residents to access their digital identities even in remote areas with low connectivity. Please refer here for more details.
Empowering users through transparent licensing.
The documentation is licensed under a Creative Commons Attribution 4.0 International License.
All MOSIP's core repositories are licensed under the terms of Mozilla Public License 2.0.
All trademarks are the property of their respective holders. Other products and company names mentioned herein may be trademarks and/or service marks of their respective owners..
The Future of Digital Identity: Secure, Scalable and Open-Source.
Modular Open-Source Identity Platform (MOSIP) is an open-source, open standards-based designed to help countries build and manage their national ID systems. Anchored at the , MOSIP enables governments to conceive, develop, implement, and own secure and scalable digital identity solutions.
Built with an API-first approach, MOSIP provides features, covering , , and . The platform is designed to foster global Digital Public Goods (DPGs) in digital identification and governance. By leveraging open-source technologies, MOSIP ensures scalability, security, and privacy, adhering to best industry practices.
MOSIP’s modular and adaptable architecture gives adopting countries full ownership and flexibility to customize the system to their needs. As a transparent and human-centric initiative, MOSIP encourages global collaboration, welcoming contributions from developers, technology partners, and research institutions worldwide.
Our global team of experts and advisors supports countries throughout the adoption and implementation of their digital ID systems, ensuring that they function as a common governance infrastructure for inclusive and secure digital transformation.
👉
At MOSIP, our mission is to empower governments worldwide to build and own secure, inclusive, and scalable digital identity systems. As an open-source, modular platform, MOSIP provides a strong foundation for nations to establish their digital public infrastructure, ensuring privacy, security, and interoperability.
Our key objectives include:
Enabling countries to develop secure, citizen-centric ID systems by providing a robust and fully functional framework.
Offering flexibility and customization so that nations can tailor the platform to their specific needs.
Ensuring privacy, security, and confidentiality of individuals’ data, following global best practices.
Upholding transparency, security, and human-centric technology to foster trust and reliability.
Supporting global collaboration through open-source contributions, partnerships, and an ecosystem of technology providers, researchers, and developers.
Providing a scalable and accessible solution that serves populations from a few thousand to several hundred million.
By fostering an open and collaborative ecosystem of technology partners, researchers, and developers, MOSIP enables nations to build robust, adaptable, and future-ready identity solutions tailored to their unique needs.
👉
1. Modular
MOSIP’s mutually exclusive technology bundles allow adopting nations to build custom workflows instead of relying on a fixed system. Each functionality is designed as an independent microservice, ensuring flexibility and control over digital ID implementation.
2. Open Source
We are committed to developing trusted and transparent technology while contributing to global standards. Our open-source code repository is available entirely on , encouraging contributions from user communities and providing governments with full control over their ID systems. MOSIP actively collaborates with IEEE, governments, and industry partners to establish common Open Standards and Protocols, making MOSIP easy to integrate, interoperable, cost-effective, and time-efficient.
3. Vendor-Neutral
We offer governments the ability to integrate with a wide range of compliant technology partners. A foundational digital ID system requires smooth integration of platforms, biometric devices, and system integrators. MOSIP ensures vendor neutrality through the MOSIP Partner Programme and , allowing countries to choose and update their technology solutions freely, saving both time and financial resources.
4. Secure and Private Design
We believe every individual should be in control of their own data. MOSIP ensures data security and privacy, with cryptographic encryption and zero-knowledge architecture safeguarding information both in transit and at rest. Governments retain sovereign control over their ID systems, and data sharing occurs only with the individual’s consent. Learn more about our security and privacy principles .
5. Cost-Effective
MOSIP provides a zero-cost platform for adoption and licensing, enabling governments and organizations to build a foundational digital ID system under Mozilla’s Public License 2.0. The automation of processes within MOSIP minimizes implementation costs, allowing countries to test and establish effective digital infrastructure efficiently.
6. Human-Centric
We aim to develop technology that can cater to diverse and varying requirements around the world. The expert team at MOSIP constantly strives to learn from on-ground experiences in adopting nations, to understand their context-specific requirements and provide unique and adaptable solutions.
7. Inclusive
MOSIP is committed to inclusivity, ensuring technology remains accessible to all, regardless of gender, race, or economic status. Our ongoing collaborations with universities, research institutions, and field teams help refine our technology for unrestricted accessibility. Innovations like Inji, a digital wallet mobile app, empower residents to access their digital identities even in remote, low-connectivity areas.
To know more, click .
Understanding MOSIP’s Role in Foundational ID Systems.
A Foundational Identity System provides individuals with a unique identifier issued by the government, enabling identity assertion and verification across multiple services. Unlike functional IDs, which are designed for specific use cases such as healthcare, finance, and social services, foundational IDs serve as a universal framework that various sectors can leverage.
MOSIP empowers governments to build secure, interoperable, and inclusive foundational ID systems. With robust privacy protections and modular architecture, MOSIP ensures individuals have control over their personal information while enabling seamless access to public and private services.
Below is a diagram illustrating the relationship between Foundational IDs and Functional IDs.
Foundational ID systems provide individuals with a unique, government-recognized identifier for identity verification. They help de-duplicate records, authenticate individuals, and verify identity attributes.
Functional IDs are sector-specific and designed for specific use cases such as healthcare, finance, social protection, education, and voting. These IDs can leverage the foundational ID system to ensure accuracy, efficiency, and seamless service access.
This structure helps create a secure and interoperable identity ecosystem for both public and private services.
is a secure, scalable, and open-source framework designed to help governments and organizations build foundational identity systems. It offers a flexible and configurable approach, allowing countries to tailor their national ID systems to meet specific requirements while ensuring privacy, security, and interoperability.
The below image illustrates MOSIP as a modular, open-source identity platform designed for secure and scalable digital identity systems. It highlights key features such as interoperability, open standards, security, and privacy, ensuring seamless integration without vendor lock-in.
Additionally, it showcases MOSIP’s core functionalities, including ID issuance, identity verification, and lifecycle management, making it a flexible solution for national ID implementations.
The image below highlights MOSIP’s security and privacy principles, emphasizing its "Security by Design" and "Privacy by Intent" approach.
These principles align with MOSIP’s Privacy and Security framework.
For more details, please refer to section. To learn more about MOSIP’s Principles, .
The image below illustrates the various MOSIP Modules:
Pre-Registration – Enables users to provide basic demographic data and book appointments for registration.
Registration – Facilitates registration of an individual, for availing a Unique Identification Number (UIN) by providing demographic and biometric data (fingerprint, iris, and face photograph) in online/offline mode.
Registration Processor – Generates a Unique Identification Number (UIN) post a regulated process and enriches data.
ID Authentication – Provides demographic and biometric authentication services, including Yes/No and E-KYC services, enabling access to a myriad of rights and services.
Resident Services – Allows residents to update and monitor usage of their IDs, giving individuals control over their own identity.
Partner Management – For onboarding, managing, and integrating external partners (relying parties) within the MOSIP ecosystem.
To learn more about the MOSIP modules, please refer .
MOSIP collaborates with ecosystem partners to develop tailored identity solutions for each country.
The diagram below illustrates the MOSIP Ecosystem, highlighting how various components integrate with the MOSIP Platform to deliver a comprehensive ID solution.
To learn more about the MOSIP Ecosystem, please refer .
The diagram illustrates MOSIP’s Key Offerings in ID Lifecycle Management and ID Authentication, highlighting two main processes:
1. ID Registration Process
Step 1: Online Pre-Registration – A resident submits demographic details online.
Step 2: Biometric Enrollment – The resident visits a registration center for biometric data collection.
Step 3: ID Issuance – After successful validations and processing, the resident receives a Unique Identification Number (UIN).
2. ID Authentication Process
An ID holder requests authentication to access services.
Authentication is performed via an authentication partner equipped with biometric or digital verification tools.
The MOSIP Authentication System validates the identity, providing eKYC or token-based responses for service access.
These offerings enable secure, scalable, and modular identity management and authentication solutions.
Countries can leverage MOSIP as the base identity platform and configure, customize, and extend it to build systems just the way needed.
The image below depicts how MOSIP provides the base layer to build a national ID platform.
Technology that leaves no one behind.
With the mission of empowering lives all over the world, MOSIP continues to take steps towards being an inclusive platform. Ongoing collaborations with global universities, research organizations, and strong on-ground teams have sharpened our focus on developing technology that is unrestricted by gender, race, and economic status. Additionally, technology features allow individuals to access services with digital identities through multiple channels, and even in remote areas with low connectivity, ensuring no one is left behind.
Some mechanisms through which the MOSIP platform supports inclusivity is illustrated below:
Introducer Support For The Undocumented
The Introducer concept in MOSIP allows individuals without formal identity documents to be enrolled into the digital identity system. A trusted and verified Introducer, such as a community leader or an authorized individual, vouches for the person’s identity. This ensures that marginalized populations, including refugees, nomadic groups, and those lacking paperwork, can still obtain a digital identity. By enabling inclusion through trust-based verification, the Introducer mechanism helps governments provide identity access to all, promoting social and financial inclusion.
Multi-Language Support for Linguistically Diverse Communities
Multi-language support in MOSIP enhances inclusivity by ensuring individuals can interact with digital identity systems in their native or preferred languages. This helps bridge linguistic barriers, making identity services accessible to diverse populations, including those with limited literacy in dominant languages. By supporting localization, MOSIP enables governments to customize the platform to suit national needs, fostering greater adoption, trust, and usability. This approach aligns with the goal of creating inclusive and equitable digital identity ecosystems worldwide.
Biometric Exception Handling for Individuals with Difficult-to-Capture Biometrics
MOSIP’s biometric exception handling ensures that individuals with difficult-to-capture biometrics, such as worn fingerprints or missing biometrics like finger or eyes, are not excluded from digital identity systems. When biometrics cannot be collected, MOSIP provides alternative methods, such as marking the biometric modality as an exception and capturing a photograph as evidence, thereby allowing inclusive identity registration for all. This approach ensures that elderly individuals, manual laborers, and persons with disabilities can still obtain a secure and verifiable identity, reinforcing inclusivity and accessibility in digital identity.
Enabling In-Home registration with Android Registration Client
The (ARC) enhances inclusivity by enabling in-home registration for individuals who are unable to visit physical registration centers. This portable solution ensures that residents, especially in remote locations, can access identity registration services at their convenience. By providing mobility for registration agents and allowing remote registrations, ARC significantly expands coverage and accessibility, ensuring that even those in underserved or hard-to-reach areas are included in national identity systems.
Ensuring Gender Inclusivity with MOSIP's GenderMag Collaboration
MOSIP’s collaboration with ensures inclusivity by integrating gender-sensitive design principles into the User Interface (UI) and Design. This approach helps identify and address barriers that may disproportionately affect users based on gender, ensuring that the digital identity platform is accessible and effective for all users, regardless of gender. This approach emphasizes on creating interfaces that are intuitive and equitable, thus ensuring an inclusive user experience for diverse populations.
Multi-Modal Verification with Inji and eSignet
MOSIP ensures inclusivity by offering multiple verification modalities through and . These solutions provide secure and convenient citizen verification across various channels, including online/offline, self-service/assisted modes, and accessible even with smartphones, feature phones, or no phones. This flexibility allows individuals from diverse backgrounds, including those with limited access to technology or support, to easily access and benefit from the services.
Through its inclusive mechanisms, MOSIP continues to push boundaries in providing accessible and equitable digital identity solutions. By focusing on universal access and adaptability, MOSIP ensures that everyone—regardless of their background, location, or physical limitations—can benefit from the services enabled by the platform. These efforts reflect MOSIP's commitment to creating a more inclusive and sustainable digital future for all.
MOSIP's fundamental architecture and design incorporate the highest levels of privacy and security.
Key security features:
Encryption of data in-flight or rest. (See )
Integration with trusted applications only.
Fraud avoidance - association of authentication only with specific transactions.
Misuse prevention - user can lock or unlock their authentication.
Virtual ID and Tokens to prevent identity theft.
All data sent out of MOSIP will be digitally signed.
All incoming data will be signed by the respective entity.
Any data sent to a relying party will be encrypted.
Protection against internal attacks with every record in DB protected with integrity.
Centralized key management.
All API's are protected with OAUTH 2.0.
Key privacy features:
Minimal data with selective disclosure on a need-to-know basis.
Sensitive data protected (not stored or logged in clear form).
Consent support – the user decides who can receive what credentials & what attributes.
No search on the database (You can find a record only if you know the ID).
Clear segregation of Biometric & Demographic data.
De-centralised ID usage and data (cannot profile based on usage).
Users are not limited to one permenant ID - Virtual ID.
All relying party gets a privacy enabled tokens to prevent profiling across transactions. Permenant ID is never shared.
Supports Wallet based decentralized ID issuance and usage.
Face data is not sent to ABIS for deduplication.





The ID Issuance component in MOSIP encompasses the set of modules responsible for the creation and assignment of unique identities to individuals. It orchestrates the end-to-end process, starting from the collection of demographic and biometric data, through validation and processing, to the final generation of a unique identity number (UIN). The sub-modules under ID Issuance include:
Pre-registration: Enables individuals to submit demographic details online in advance, expediting the in-person registration process.
Registration Client: Facilitates the collection of demographic and biometric data at registration centers, providing an intuitive interface for operators.
Android Registration Client: A mobile application version of the Registration Client, allowing for data collection in remote or field locations using Android devices.
Registration Processor: Validates and processes registration data, ensuring its integrity before moving to the next stage.
id-repository: Manages the storage and retrieval of identity data, ensuring secure and efficient access to demographic and biometric information.
Together, these modules ensure a secure, efficient, and streamlined approach to issuing unique identities within MOSIP. For more details on each module, refer to their respective overview pages.
This page lists the standards and specifications published by MOSIP which are mentioned below:
Build, integrate, and enhance solutions.
Empowering Trusted Digital Identity with Secure and Seamless Credential Verification.
In today's fast-paced, interconnected world, ensuring seamless access to essential services—such as healthcare, financial inclusion, global mobility, and social support has never been more critical. The need for trusted identity authentication and secure data exchange is at the heart of accessing these services.
To address this, Inji offers a transformative solution – enabling the secure issuance, digitalization, storage, exchange, and seamless verification of trusted data as verifiable credentials, through a comprehensive set of tools.
Inji, meaning "knowing" or "recognizance" in Korean, is evolving into a comprehensive digital credential stack with a strong focus on user empowerment. Inji simplifies the management and verification of credentials by providing secure solutions that work across multiple interfaces. It aims to streamline creating, sharing, and verifying all types of digital and physical credentials.
Enabling Secure, Inclusive, and Seamless Digital Identity Verification.
In today’s digital-first world, most services are transitioning online, making a secure and trusted digital identity more important than ever. A secure and trusted digital identity is crucial to facilitate personalized access to these online services.
eSignet strives to provide a user-friendly and effective method for individuals to authenticate themselves and utilize online services while also having the option to share their profile information. Moreover, eSignet supports multiple modes of identity verification to ensure inclusivity and broaden access, thereby reducing potential digital barriers.
Additionally, eSignet offers a seamless and straightforward solution for incorporating an existing trusted identity database into the digital realm. By enabling digital identities and providing identity verification and service access, eSignet delivers a sophisticated and user-friendly experience.
Explore more about Inji.

This document provides a comprehensive analysis of security implementations across multiple levels. Additionally, it clearly delineates the boundaries of responsibility between MOSIP and the countries implementing the system.
Within this document, we have categorized security practices into 'Internal Practices' and 'Operational Protection'.
Internal security practices are integrated into the MOSIP development lifecycle to build security within the system from the ground up. These include rigorous threat modeling, secure coding practices, comprehensive code reviews, and continuous vulnerability assessments to ensure that potential risks are identified and mitigated early. By embedding these security measures during development MOSIP fosters a proactive security culture that not only minimizes vulnerabilities but also supports a robust defense strategy throughout the system's lifecycle.
On the other hand, operational security practices include firewall rules, intrusion detection systems, continuous monitoring, and incident response strategies. These measures focus on maintaining the security and integrity of the system during its operational phase, addressing runtime threats and ensuring compliance with best practices. Operational practices are outside of MOSIP development stage and to be taken up by the implementing countries.
Internal security practices encompass measures such as security requirement elicitation, design, adherence to the MOSIP Principles, Platform development, static and dynamic code analysis, dependency scanning, code signing, and vulnerability management. These practices ensure that potential threats are identified and mitigated early in the development lifecycle.
MOSIP's fundamental architecture and design incorporate high levels of privacy and security.
(Table to be updated soon)
This section details the measures taken during the development, testing, and release phases to ensure maximum security. Multiple checks are enforced at each stage through the use of various tools, tests, and scans. Key practices include:
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a cornerstone of our security strategy. Tools like SonarCloud are used to perform in-depth code analysis during the development phase, identifying vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure coding practices. SAST provides developers with real-time feedback, enabling them to address security flaws early, thereby reducing the cost and effort of remediation later in the software lifecycle. These tools integrate seamlessly into our CI/CD pipelines, ensuring that security is addressed continuously and early. Dependency scanning tools like Dependabot, CodeQL, and others further enhance this layer of protection by monitoring and updating vulnerable dependencies.
Sonar Cloud - Development Phase - SonarCloud is integrated with Github actions, offering developers actionable insights directly within the workflow. By highlighting security hotspots and technical debt, it enables teams to prioritize and address critical issues efficiently.
MOSIP Sonar cloud Link : https://sonarcloud.io/organizations/mosip/projects
CodeQL (Java and Python) - Development Phase - CodeQL performs semantic code analysis, enabling the detection of complex vulnerabilities
Github Dependabot (Vulnerability assessment and Version upgrade suggestions) - Development Phase - Dependabot simplifies the process of updating dependencies by creating pull requests with the necessary upgrades reducing manual effort and ensuring the codebase remains secure against known vulnerabilities. Its integration into GitHub workflows ensures timely updates and fosters a proactive approach to dependency management.
Open source compliance scanning - Ensures that all open-source components in use comply with licensing requirements and security best practices. This scanning helps in identifying potential legal or security risks associated with third-party libraries. Automated tools are used to track, analyze, and flag issues related to incompatible or outdated licenses, ensuring smooth and compliant project operations.
Github scan - Provides robust scanning capabilities integrated directly into GitHub repositories. It includes features such as secret scanning, dependency graph analysis, and vulnerability alerts, helping developers proactively detect and fix security issues within their workflows.
Data Breach Detector - It is a prodcution grade tool/script which goes through the DB and utilizes Deduce library to find out anomalies in various places such as names, address or numbers in plaintext etc.
Dynamic Application Security Testing (DAST)
DAST focuses on identifying security vulnerabilities in a running application by simulating real-world attack scenarios. Unlike SAST, which examines static code, DAST tests live applications, analyzing responses to detect flaws such as authentication issues, session management vulnerabilities, and exposure of sensitive data. Tools like Burp Suite Professional and ZED Attack Proxy (ZAP) are leveraged to conduct automated and manual penetration tests. These tools allow testers to evaluate application behavior under various conditions, ensuring robust protection against runtime threats. By integrating DAST into the release process, vulnerabilities can be identified and mitigated before applications are deployed into production.
Burp Suite Professional : This tool is used for automated and manual penetration testing . It provides features such as intercepting proxy, web vulnerability scanner, and advanced debugging capabilities. Burp Suite enables testers to identify vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure session management. It also supports extensions for customized scanning and integrates seamlessly into security workflows.
ZED Attack Proxy: This tool is used for finding vulnerabilities in web applications during the development and testing phases.
Release Practices
Release practices are essential for ensuring the security, authenticity, and traceability of software releases. Here is an overview of the components used in MOSIP releases.
Image Signing: ASC (ASCII-armored PGP) signing is typically used to ensure the authenticity and integrity of software artifacts, including Docker images, by attaching a digital signature. When signing software images, MOSIP uses the private key to sign the image, and users can verify the signature using the corresponding public key.
JAR (Java Archive) Signing is the practice of signing Java archive files to ensure that the contents of the JAR haven't been tampered with and to provide a way to verify the source of the file. This is currently not implemented in MOSIP.
These recommendations provide a robust framework to ensure the security and integrity of production systems for MOSIP implementing countries, helping to mitigate risks and enhance overall cybersecurity posture.
SBI Compliant Devices: Ensure that all devices used in the production environment are compliant with the latest Secure Biometric Interface (SBI) standards to ensure a highest level of security.
Trusted Platform Module: A Trusted Platform Module (TPM) is a specialized chip on a local machines that stores cryptographic keys specific to the host system for hardware authentication. The private key is maintained inside the chip and can't be extracted out. By leveraging this security feature every individual machine would be uniquely registered and identified by the MOSIP server component with it's TPM public key.
Compliance Tool Kit: MOSIP Provides Compliance Tool Kit (CTK) to help the device vendors to check if their products comply with SBI specifications.
Access and Audit Logs: Enables detailed access and audit logging for all critical systems and services in the production environment.
Patch Management (Host/Machines): Implement a robust patch management policy to ensure that all production systems are up-to-date with the latest security patches.
Safe Data Centers: Ensure that data centers housing production systems are designed and operated with a focus on security, availability and operational safety.
International standards: Stay compliant on international standards such as ISO/IEC 27001, NIST Cybersecurity Framework, and relevant national regulations. Better to validate the compliance using third party assessments.
Ensuring Data Protection: Enforce robust data protection measures to safeguard sensitive information at rest and in transit.
Consent-Based Data Handling: Ensure that data is only collected, processed, and stored with the explicit consent of the individuals it pertains to, in accordance with privacy laws and regulations.
Regular Security Audits: Perform regular security audits to assess the effectiveness of security measures and identify potential vulnerabilities in production systems.
Principle of Least Privilege: Ensure that users and systems are granted only the minimum level of access necessary to perform their tasks, reducing the risk of accidental or malicious misuse.
Rate Limiting: Implement rate limiting to protect services from abuse, such as brute force attacks or denial-of-service (DoS) attempts.
The Android Registration Client is a tablet application that serves as a portable version of the existing desktop Registration Client. It has been developed to support accessibility on all Android devices. The creation of the Android Registration Client was driven by the need to meet the mobility requirements of countries adopting MOSIP.
The primary objective of the tablet version is to facilitate the registration process for residents, especially those who are unable to physically visit registration centers. It also serves remote locations where setting up registration centers is not feasible. To address this challenge, the Android Registration Client was created, enabling operators and supervisors to easily reach remote areas and maximize resident registrations across the country.
To read through the comprehensive list of configurable properties for the Android Registration Client, refer Android Registration Client Configuration Guide.
For more details on UI specifications for the Android Registration Client, refer here.
The Android Registration Client is compatible with the following MOSIP platform versions:
1.1.5.x
LTS 1.2.0 and above
Seamless Integration with MOSIP: Explore Our Sandbox Environments.
Are you interested in integrating with MOSIP as a partner? We invite you to connect with us by completing the form. This will assist us in facilitating a seamless integration with our designated sandbox environments.
Please find below the two sandbox environments available for your use.
Collab is our development integration environment that has QA-tested dockers deployed. Our partners and contributors can use this to build on the platform or integrate with the QA-certified version of the latest platform code.
Regular nightly builds from engineering are deployed here and this environment is used for continuous development.
The link to access the Collab environment is available here.
Looking to collaborate with us? Click here to get started with the Collab environment!
Synergy is our stable environment where the latest released version of the MOSIP platform and applications are deployed for partners to integrate and test.
The link to access the Synergy environment is available here.
The Identity Verification category in MOSIP encompasses modules responsible for authenticating and verifying the identity of individuals using various mechanisms. Below are the modules under this category, each with a brief description and a link to their respective overview pages:
ID Authentication Services: Provides APIs for authenticating individuals based on their identity data, including demographic and biometric information.
ID Authentication (IDA): IDA module in MOSIP is an independent service that enables seamless identity verification using data from any system. Multiple IDA modules can run from a single issuer, providing services like authentication, OTP generation, and internal processes.
Effortlessly deploy and configure with comprehensive guides , repositories and more.
Effortlessly deploy and configure with comprehensive guides , repositories and more.
Identity Management refers to the processes and technologies used to create, maintain, and manage digital identities. In MOSIP, it ensures secure and efficient handling of individual identity data throughout its lifecycle.
Resident Services: Provides APIs for managing resident data, including creation, updates, and retrieval of demographic and biometric information.
Resident Portal: A reference UI for residents to easily access and manage their identity data.
ID Schema: Defines the structure and format of identity data, ensuring consistency and interoperability across the system.
Identifiers: Manages the generation, assignment, and lifecycle of unique identifiers for individuals within the MOSIP ecosystem.
Smart, Secure and Self-service for every resident.
Managing identities seamlessly.
Identity Lifecycle Management refers to issuing and managing user identities in a given system. An individual can visit a registration centre to get a new ID or update their ID details. A registration officer would typically capture the individual’s demographic (name, date of birth, gender, etc.) and biometric (face, iris, and fingerprint image) details.
The lifecycle of an identity involves multiple events, categorized into different stages, each managed within specific system modules. The following sections outline these key lifecycle events, detailing their roles and functions categorized under relevant modules. Browse the cards below to explore the various applications and services that support Identity Lifecycle Management.
Ensuring secure and interoperable digital identity through global standards.
At MOSIP (Modular Open Source Identity Platform), we are committed to building a secure, interoperable, and privacy-centric identity system for nations worldwide. MOSIP adheres to internationally recognized standards in biometric authentication, security, cryptography, privacy, and interoperability to ensure the highest levels of security, efficiency, and compliance.
By following these global standards, MOSIP ensures that our identity platform is: ✅ Secure – Protecting citizens’ data from cyber threats. ✅ Privacy-First – Upholding the highest standards of data protection. ✅ Scalable & Future-Ready – Enabling nations to build robust digital identity programs. ✅ Interoperable – Seamlessly integrating with digital identity solutions worldwide.
To ensure seamless biometric interoperability and security, MOSIP follows:
ISO/IEC 19794 – Standardized biometric data formats for fingerprints, iris, and facial recognition.
(Common Biometric Exchange Formats Framework) – Facilitates interoperability and efficient biometric data exchange.
IEEE P3167 (DRAFT) – Strengthening the trustworthiness of biometric devices and their captured data while ensuring overall data security.
To guarantee robust data security and encryption, MOSIP aligns with:
NIST Cybersecurity Framework – Provides guidelines for IT security evaluation and risk management.
RSA, EC, JSE – Implements industry-standard cryptographic algorithms for secure encryption and data integrity.
To enable effortless integration with national and global identity ecosystems, MOSIP adopts:
OAuth 2.0 / OpenID Connect – Providing secure and scalable authentication mechanisms.
REST, OpenAPI Standards – Ensuring standardized communication across different platforms.
JMS (Java Message Service) & WebSub – Facilitating real-time messaging and event-driven architecture.
Claim 169 – A globally registered specification under the , developed by It allows demographic and biometric data (like a low-res face image) to be embedded in a digitally signed QR code, enabling reliable offline identity verification. to know more.
Modular, Secure, and Scalable: The Architectural Foundation of MOSIP.
MOSIP is built on a modular, microservices-based architecture. Its modularity enables seamless adoption even in complex scenarios. Most are designed as robust foundational infrastructure components, making them suitable for integration into various projects.
MOSIP is designed with the following architectural principles. These architecture principles are core to the development of the system's features and have a great influence on how and why specific software design patterns are used within.
Data Privacy
No Vendor Lock-in
Open Standards
Async/ Offline First
Commodity Computing
Fault tolerant
Manageable
Secure By Default
The diagram below provides an architectural overview, visually representing the components of the MOSIP Identity framework and its associated technology stack.
The High Level Reference Functional Architecture serves as a blueprint outlining the system's high-level functioning and interactions, providing a structured framework.
To know how MOSIP can be deployed, refer to . The different installation models are detailed in the section.
The table below outlines the frameworks, tools, and technologies employed by the Android Registration Client.
Android SDK Versions :
Target SDK Version : 31
Compile SDK Version : 31
3.10.4
Flutter transforms the development process. Build, test, and deploy beautiful mobile, web, desktop, and embedded experiences from a single codebase.
3.0.3






Welcome to the Pre-registration Collab Guide! This guide will equip you to seamlessly access the Pre-registration demo application, explore, integrate, and effectively demonstrate its capabilities.
The Pre-registration module within MOSIP is designed keeping residents in mind, offering a user-friendly pre-registration process. This module boasts of a wide range of functionalities, starting with the collection of demographic data along with easy uploading of essential supporting documents, such as proof of address and birth certificates, besides facilitating appointment booking, modifications, and notification alerts to mention a few.
With this Pre-registration Client Demo Setup, you're one step closer to showcasing the power of MOSIP's pre-registration capabilities.
So let's get started!
Accessing the Pre-registration portal in the Collab environment does not require any complex setup.
All you need is a 10-digit Mobile Number or a valid email ID and you are good to go!
Visit the following URL to access the Pre-registration portal in the Collab environment: Pre-registration portal
Login to the portal with a mobile number or valid email ID. Refer to below for details.
Mobile Number:
If you choose to login using your mobile number, you will be required to enter any 10-digit mobile number, for example - “1234567890”.
Click on the captcha tick box to proceed to the next step.
Email ID:
Alternatively, you can choose to log in with your email ID.
For the Collab environment, real email ID OTP verification is performed.
Enter a valid email ID and an OTP will be sent to your email address. You can then enter the OTP received on the provided email ID to verify yourself and log in to the portal.
To access all the features of the Pre-registration portal and explore the pre-registration process in MOSIP, refer to our end user guide.
Note: Please use 111111 as the OTP, for any OTP-based feature in the Collab environment.
Watch this informative video here for a visual walkthrough of the features.
For more information about Pre-registration, click here.
By following these instructions, you will be equipped to seamlessly set up the pre-registration portal and effectively use all the features and book an appointment.
If you require any assistance or encounter any issues during the testing and integration process, kindly reach out to us through the support mechanism provided below.
Navigate to Community.
Provide a detailed description of the support you require or provide detailed information about the issue you have encountered, including steps to reproduce, error messages, logs, and any other relevant details.
Thank you. We wish you a pleasant experience!
Following are the metrics that are collected in the client application using the micrometer library:
JVM Memory Metrics
JVM Thread Metrics
JVM GC Metrics
JVM Heap Pressure Metrics
Processor Metrics
Class Loader Metrics
Disk Metrics
Packet Metrics based on client and server status
All the metrics collected are appended to metrics.log file. Rolling policy of the metrics.log is defined in registration-services logback.xml.
Below are the challenges faced in exporting the collected metrics from client application to the server for further analysis:
Unreliable network conditions on field.
Metrics files are mostly large files, and cannot afford retries on failed attempts.
Required HTTP based metrics export.
To overcome the above challenges, Registration Client is built with tus-java-client (version: 0.4.3) . Tusd server URL and the upload chunk-size are made configurable in the client application.
mosip.registration.tus.server.url: This is the server URL config which specifies to which URL the metrics files are to be uploaded.
mosip.registration.tus.server.upload.chunksize: This config defines the chunk size, which means, how much size of the file is to be uploaded at once. By default, this is given as 1024, which means 1KB
Note:
The Tus protocol is designed to enable resumable uploads of large files over HTTP, which can be useful for web applications that need to handle file uploads in unreliable network conditions or with large files that might take a long time to upload. For more information on TUS, refer here.
Tusd is a popular implementation of the Tus protocol that can be used as a standalone server. It is a part of the MOSIP deployment.
Each metric json logged into metrics.log file is tagged with machine name. Refer the below log lines with the machine names.
{"@timestamp":"2023-03-12T15:00:10.654+05:30","@version":"1","message":"{\"@timestamp\":\"2023-03-12T09:30:10.654Z\",\"name\":\"jvm.threads.states\",\"type\":\"gauge\",\"machine\":\"c1ml54597\",\"state\":\"waiting\",\"value\":8,\"unit\":\"threads\"}","logger_name":"io.mosip.registration.config.LoggingJsonMeterRegistry","thread_name":"logging-metrics-publisher","level":"INFO","level_value":20000}
{"@timestamp":"2023-03-12T15:00:10.654+05:30","@version":"1","message":"{\"@timestamp\":\"2023-03-12T09:30:10.654Z\",\"name\":\"jvm.threads.states\",\"type\":\"gauge\",\"machine\":\c1ml54597\",\"state\":\"timed-waiting\",\"value\":20,\"unit\":\"threads\"}","logger_name":"io.mosip.registration.config.LoggingJsonMeterRegistry","thread_name":"logging-metrics-publisher","level":"INFO","level_value":20000}
{"@timestamp":"2023-03-12T15:00:10.654+05:30","@version":"1","message":"{\"@timestamp\":\"2023-03-12T09:30:10.654Z\",\"name\":\"jvm.threads.states\",\"type\":\"gauge\",\"machine\":\"c1ml54597\",\"state\":\"blocked\",\"value\":0,\"unit\":\"threads\"}","logger_name":"io.mosip.registration.config.LoggingJsonMeterRegistry","thread_name":"logging-metrics-publisher","level":"INFO","level_value":20000}
{"@timestamp":"2023-03-12T15:00:10.654+05:30","@version":"1","message":"{\"@timestamp\":\"2023-03-12T09:30:10.654Z\",\"name\":\"jvm.threads.states\",\"type\":\"gauge\",\"machine\":\"c1ml54597\",\"state\":\"terminated\",\"value\":0,\"unit\":\"threads\"}","logger_name":"io.mosip.registration.config.LoggingJsonMeterRegistry","thread_name":"logging-metrics-publisher","level":"INFO","level_value":20000}
{"@timestamp":"2023-03-12T15:00:10.654+05:30","@version":"1","message":"{\"@timestamp\":\"2023-03-12T09:30:10.654Z\",\"name\":\"jvm.threads.states\",\"type\":\"gauge\",\"machine\":\"c1ml54597\",\"state\":\"new\",\"value\":0,\"unit\":\"threads\"}","logger_name":"io.mosip.registration.config.LoggingJsonMeterRegistry","thread_name":"logging-metrics-publisher","level":"INFO","level_value":20000}A job is scheduled to upload collected metrics to server from the client application.
Job runs with a fixed delay of 15 minutes.
Resumable file URLs are stored under .metrics folder of registration client. Once the complete file is uploaded to server, the metrics file is deleted locally.
Android Registration Client (ARC) is a tablet application that serves as portable version of the existing desktop Registration Client. It can be accessed through Android devices and also meets mobility requirements of countries adopting MOSIP Identity.
The primary objective of the tablet version is to facilitate the registration process for residents who are not able to physically visit Registration centers and also serve remote locations where setting up Registration centers is not feasible. To address this challenge, the ARC was developed enabling Operators / Supervisors to easily access the remote areas and maximize resident registrations across the country.
This guide serves as a tool to demonstrate the impressive capabilities of MOSIP's system. Additionally, the primary user of this guide will be the Operator / Supervisor trying to register individuals for generating UIN.
Let's embark on this journey together to explore the potential of ARC.
Reliable and consistent Internet connectivity
Tablets running Android version 10 to 13
Tablets with a minimum of 4 GB RAM
The tablets should be capable of capturing fingerprints, IRIS, and face (photo) biometrics. Additionally, they should also have the ability to scan documents. However, if the tablets do not support these capabilities, MOCK SBI can be used as an alternative.
The following details are required to access ARC in the Collab environment:
UIN or a VID
Machine details
To obtain your UIN credentials for the Collab environment follow the below steps:
The provision of a Unique Identification Number (UIN) as a demonstration credential will enable you to have a firsthand experience of the ARC's capabilities and explore its various features.
Please fill out the form with the correct details and submit the form. Upon receiving the form, we will generate a demo credential for you. We will also register you as an Operator on Keycloak and map your device to the center to which your credential is required to be mapped.
Mentioned below are the steps to download, install, and use ARC.
Step 1: Download and install the APK on an Android tablet. Visit the Android Registration Client to access ARC in the Collab environment.
Step 2: Install ARC and launch it.
Step 3: Login as an Operator with the credentials received and wait for synchronization to complete.
Step 4: Refer to our comprehensive User Guide document to learn how to register and use ARC.
Note: Please be advised that if the Android Registration Client is uninstalled and then re-installed, the aforementioned steps will need to be repeated from the start.
To know more about features of the Android Registration Client, click here.
To learn more about the ARC configurations, click here.
If you require any assistance or encounter any issues during the testing and integration process, kindly reach out to us through the support provided below.
Navigate to Community.
Provide a detailed description about the support you require or provide complete information about the issue you have encountered, including steps to reproduce, error messages, logs and any other required details.
Thank you. Wishing you a pleasant experience!
In the context of MOSIP, identifiers are alphanumeric digital handles for identities in the system. While a person's identity is represented as a collection of biographic and biometric attributes that can uniquely identify the person, the identity is referred to using identifiers.
Unique Identification Number (UIN), as the name suggests, is a unique number assigned to a resident. UIN never changes and is non-revocable. UIN is randomized such that one should not be able to derive any Personal Identifiable Information (PII) from the number itself.
The rules that govern generation of a UIN are listed here.
The VID / Virtual ID is an alias identifier that can be used for authentication transactions. The key characteristic of such an identifier is that it expires. This allows for free disclosure and usage of this identifier in various contexts. It is privacy friendly in a way such that it can be revoked, configured for one time usage and is not linkable. Since these are used for authentication transactions, such identifiers are to be known to the user only or generated with their participation.
The Application ID (AID) refers to the unique identifier given to a resident during any ID lifecycle event, such as ID Issuance, ID Update, or Lost ID retrieval, at the registration center. It serves as a distinguishing factor for each specific event and can later be utilized by the resident to check the progress or status of the event. Previously, in MOSIP, the Application ID was referred to as the RID (Registration ID) and/or PRID (Pre-registration ID).
The PRID is a specialized RID used in the pre-registration system.
The Token identifier/PSUT is a system provided customer reference number for relying parties to uniquely identify the users in their system. The token identifier is an alias meant for the partner/relying party typically unique (Configured through PMS policy, in case uniqueness is not the need then partner policy can be set to provide random number) to them. This identifier is included in the response of the authentication transactions. One key differentiator is that the PSUT is not accepted as an identifier for authentication transactions. This ensures that the partner who has the PSUT can not reauthneticate.
This guide contains all the information required for successful deployment and running of Resident Portal. It includes information about the Database and template scripts, seed data, roles, OIDC client setup, etc.
Resident Service DB Scripts to be run: DB scripts
The master-data templates required for the Resident portal are added to the template and template type DML excel files in mosip/mosip-data repository. These scripts need to be applied to the corresponding table.
mosip-resident-client needs to have below roles in keycloak:
RESIDENT
SUBSCRIBE_AUTH_TYPE_STATUS_UPDATE_ACK_GENERAL
SUBSCRIBE_AUTHENTICATION_TRANSACTION_STATUS_GENERAL
SUBSCRIBE_CREDENTIAL_STATUS_UPDATE_GENERAL
SUBSCRIBE_REGISTRATION_PROCESSOR_WORKFLOW_COMPLETED_EVENT_GENERAL
CREDENTIAL_REQUEST
Here is the document which explains how resident-oidc partner is onboarded through partner-onboarder after deployment.
For more details on how to configure the Resident OIDC client, refer here.
UIN / VID are system-generated unique identifiers provided to Residents. Residents are allowed to authenticate themselves using either UIN / VID.
What if residents are given the flexibility to create their handle (username) and use their unique handle to authenticate?
Handles can include resident's phone number, e-mail ID, or any linked functional ID / sectoral ID.
The handle can also be a custom username created through the resident portal.
Note: A recyclable ID, such as a mobile number, cannot be used as a handle. Handles must be unique and persistent to ensure reliable identification and authentication. Since mobile numbers and similar IDs can be reassigned or changed over time, they do not meet the criteria for a secure handle. Instead, handles should be chosen from identifiers that remain constant for the user, minimizing the risk of identity conflicts or unauthorized access.
Countries that have an established user base can now register users onto a relying portal using their distinctive identifiers referred to as handles. These handles are tailored to meet the specific requirements of each country, enabling users to easily access digital services and receive prompt benefits from both the government and private sector. This approach eliminates the need for users to remember a new or system generated IDs.
The implementation of custom handles involves below steps:
Mark the fields that can be used as user handles. A new attribute is introduced in identity schema, handle which accepts boolean value. More than one field in the identity schema can be marked as handle.
With phone as an example:
{"fieldCategory": "phone number", "format": "none", "type": "string", "fieldType": "default", "requiredOn" : "", **"handle" : true**},
When the user registers, collected user data should contain selectedHandles, as more than one field can be marked as handle, user can choose amongst the handle fields to use. User can also choose all of them. Client UI’s collecting user data during registration can decide to provide this option to the user or it can also set selected handles to default values as decided by the country. selectedHandles is also a field in schema, identity.
"selectedHandles" : {"fieldCategory": "none","format": "none","type": "array","items" : { "type" : "string" },"fieldType": "default" }
When the collected identity object is sent to the ID repository, it validates the data and accepts the handle provided it is unique amongst the registered handles.
Note: If duplicated, a request to register the user is rejected.
Once identity is successfully processed and stored in an ID-repository, identity credentials are issued to IDA to store user credentials for each ID (UIN & VID) as well for each selected handle.
ID-repository can be configured to disable issuance of user credential to IDA for both UIN or VID using below properties.
mosip.idrepo.identity.disable-uin-based-credential-request=true
If the system is configured to use more than one functional ID as a handle and if two different functional ID systems followed the same format /pattern to generate an ID, handles collision may occur.
Collision between two different functional IDs will result in denying the creation / updating of a handle for a resident.
Solution: Every handle stored is postfixed with handle type and the handle type is chosen based on the handle field ID in the identity schema. On every authenticate request, IDA will expect handle postfixed with handle_type as input.
Property mentioned below is introduced in ID repository to postfix handle type on every creation of identity.
mosip.identity.fieldid.handle-postfix.mapping={'phone':'@phone'}
Property mentioned below is introduced in Id-authentication-default.properties file to validate the handle value based on the postfix provided in the inidivdualId input.
mosip.ida.handle-types.regex={ '@phone' : '^\\+91[1-9][0-9]{7,9}@phone$' }
Implementing custom handles provides a user-friendly approach to user authentication without burdening end users with the need to remember additional or system generated complex IDs.
The security of user data is given the highest priority in MOSIP. Data is protected in flight and rest using strong cryptographic techniques. All operations on decrypted data are done in memory.
Various flows with encryption are illustrated below. Refer to Keys for all references of the type 'Kx' and 'KPx'.
The below diagram represents a registration data flow system for biometric authentication and identity management.
Biometric Capture:
A biometric device captures and signs biometric data before sending it to the Registration Client (PK2). Then registration client verifies the signature
Registration & Encryption:
The Registration Client, running on the operator’s system, receives biometric data and securely encrypts it into packets.
The client always refers to Keycloak for authentication, ensuring that only authorized operators can access the system.
Registration Client signs the packet using the TPM key of the machine (K10) and encrypts the packet using MOSIP public key specific to (the registration centre, machine id) combination (K11).
Data Processing & Storage:
The encrypted packets are transmitted to the Registration Processor, which processes and signs the data.
The processed data is then stored in the Object Store and ID Repository for further use.
Secure Storage of Biometric Data:
ID Repository encrypts biometrics, demographics, and documents and stores them in the Object Store. (K7.1,K7.2,K7.3)
Hashed UIN Storage:
The UINs are hashed, encrypted, and stored in uin the table of mosip_idrepo DB. (K7.4)
Data Sharing & Policy Enforcement:
When encrypted biometric data needs to be shared, it is sent to ABIS for authentication.
The system consults the Partner/Policy Management System to verify partner details and enforce data-sharing policies.
Only partners who have registered and authenticated via Keycloak can access the Partner Management System, where they must subscribe to specific policies to receive data.
Demographic Data Storage:
Encrypted demographic data is stored in the Registration Processor Database. (K11)
Credential Issuance:
Encrypted resident data is shared with credential requestors and printers based on the subscribed policies. (K12)
Operator Authentication:
The Registration Client checks Keycloak to ensure that only authenticated operators can perform registrations.
Policy Validation for Data Transfer:
Before transferring encrypted data to ABIS, partners, or credential requestors, the system refers to the Partner/Policy Management System to validate policies.
11. Partner & Policy Control:
The Partner Management System is controlled by Keycloak, ensuring that only registered partners with valid credentials can subscribe to and enforce policies for data access. (11,12,13)
Data shared with all partners like ABIS, Print, Adjudication, IDA, etc. is encrypted using partners' public key. Note that IDA is also a partner, however, a special partner in the sense that data is additionally zero-knowledge encrypted before sending to IDA (see the section below).
The ID Authentication module (IDA) is independent and may be hosted by several providers. IDA hosts all the biometric templates and demographic data. Unique additional protection is provided here to make sure that mass decryption of user data is very difficult to achieve. The data can only be decrypted if the user's UIN is provided. Here is the encryption scheme:
Generate master symmetric encryption key K9.
Generate a 10,000 symmetric keys pool (ZKn). Encrypt each ZKn with K9 and store it in DB. (K12)
Randomly select one key from ZKn, and decrypt using K9.
Derive new key ZKn' = ZKn + UIN/VID/APPID.
Encrypt biometric templates and demographics.
BIO = encrypt(bio/demo with ZKn').
Encrypt ZKn (this is done to share ZKn with IDA).
ZKn-IDA = encrypt(ZKn with K22)
Share the following with IDA:
ZKn-IDA
BIO
Random index (0 - 9999)
SHA-256 hash of UIN/VID/APPID
Share data in step 7 via standard Datashare encryption (which encrypts entire data with PK8).
Generate master symmetric encryption key K18.
Decrypt data in Step 8 above using PK8.
Decrypt ZKn-IDA with K22 to get ZKn.
Encrypt ZKn with K18 and store it at a random index.
Bio-data is stored as is.
L1 devices contain FTM to encrypt (DE1, K21) and sign (FK1) biometrics at the source and send them to the authentication client.
The authentication client further encrypts the auth request with the IDA-PARTNER public key.
IDA decrypts zero-knowledge data as given in Step 4 and then performs a demographic and/or biometric authentication.
The match result is returned to the Auth client. In the case of KYC, the KYC attributes are encrypted with the Partner's public key (as in Datashare).
Resident services are self-service tools utilized by residents through an online portal. The is a web-based user interface application that offers services related to the residents' Unique Identification Number (UIN). Through this portal, residents can perform various operations related to their UIN or VID and can also raise any concerns they may have.
The relationship of Resident services with other services is listed below.
Audit Manager: Resident services sends all the audit logs to the Audit Manager.
Digital card service: Resident services use this service to download the PDF of the UIN card or VID card.
Credential Request Generator Service: This service is used to share credentials with various partners, such as print, authentication, and digital card partners.
ID Repository Identity Service: Resident services use this service to retrieve a credential's identity information and lock/unlock authentication types.
ID Repository VID service: This service is used to generate/revoke various types of VIDs.
ID Authentication: This service is used by Resident services to authenticate users.
MOSIP e-Signet: This is used to authenticate and authorize the users in the event of login using UIN/ VID.
Resident UI: This is the interface through which users can interact with the Resident Services.
WebSub: This is used to get asynchronous notifications from IDA for acknowledgment purposes.
Registration Processor: This is used to sync and upload packets for features about changes in identity data.
Packet Manager: Resident services use this service to create packets.
Partner Management Service: Resident services use this service to get information about various partners and policies.
Keycloak: Resident services use this to authenticate to access the MOSIP internal APIs. The Resident Services communicates with endpoints of other MOSIP modules via a token obtained from Keycloak.
Master data service: Resident services invoke the Master Data services to get various templates and machine details.
Notification service: Resident services use this service to send various notifications through email or SMS.
Key Manager: Resident services use Key Manager to encrypt or decrypt the data used across features.
The design of the Resident portal embodies the following principles:
One-stop solution: The Resident portal is designed to have components that aim to solve all the queries, issues, or discrepancies of the residents and act as a one-stop solution for all the requirements.
Self-Sovereign: Once the ID is issued by an authority, the user/resident/citizen chooses to control and manage their data in their choice of devices.
Inclusive: The Resident portal aims to be available in all browsers while also catering to the needs of visually impaired, dyslexic, and color-blind folks.
Presence assurance: This web-based UI application would put in all its efforts to ensure easy access to all the residents with high availability.
Works Remote: The Resident portal should be able to share credentials when data needs to be shared remotely without physical presence.
Trusted: The identity verification process on the device should be trusted so that it can be used in service delivery without any concerns.
Grievance redressal: The Resident portal ensures that in case of any concerns or grievances, the issue is raised and resolved through the portal itself.
Explore features of the Resident Portal.
The key features provided on the Resident portal are mentioned below.
View My History: This feature enables the Resident to view the history of transactions associated with their UIN.
Manage My VID: Residents can create, delete, and download VID cards based on requirements.
Secure My ID: Residents can lock or unlock their authentication modalities such as fingerprint authentication, iris authentication, email OTP authentication, SMS OTP authentication, thumbprint authentication, and face authentication.
Track My Requests: This feature enables the Residents to enter an Event ID associated with the logged-in user’s UIN to track the status of the event.
Get Personalized Card: The residents can download a personalized card which essentially means that they can choose the attributes that they would want to be added to their cards.
Share My Data: This feature enables Residents to choose the data that they want to share with a MOSIP-registered partner.
Update My Data: This feature enables the Resident to update their identity data, address, email ID, phone number, and notification language preference.
Logout: Once the Resident is done with the activities that he wanted to perform, he can end the active session by logging out from the portal.
About Registration Centers: Residents can get a list of Registration Centers near them or Registration Centers based on the location hierarchy.
List of supporting documents: Residents can get the list of all the supporting documents as Proof of Identity, Proof of Address, Proof of Relationship, etc.
Using this feature, the Resident can download their password-protected UIN card if the UIN card is ready or they can view the status of their Application ID (AID) if the UIN card is still in progress.
Using this feature, the Resident can verify if the email ID/ Phone number given during registration is correct or not. This will be done by verifying the OTP sent over the registered email ID/ Phone number.
Using this feature, the Resident can book an appointment to visit the Registration center.
Multi-lingual support: Residents can view and use the Resident Portal in multiple languages including RTL languages.
Get Notifications (email and bell notifications): Residents will be getting bell-icon notifications for the asynchronous events if they have an active session i.e. they have logged into the Resident Portal.
View profile details of the logged-in user (name, photo, and last login details): The Resident will be able to view the name, and photo of the logged-in user. They will also be able to see the last login details of the Resident.
Responsive UI support: Support for the application to work seamlessly on various resolutions.
Below is an image summarizing the features provided in the Resident portal.



The Registration Client is a thick Java-based client where the resident's demographic and biometric details are captured along with the supporting documents in online or offline mode. Data is captured in the form of registration packets and is cryptographically secured to ensure that there is no tampering. The captured information is packaged and sent to the server for further processing.
MOSIP provides a reference implementation of a Java-based Registration Client. The code, and build files for the Registration Client are available in the Registration Client repo.
Registration Client is featured to allow an operator to choose the operation language. The option to select their preferred language is provided on the login screen.
Data collection during registration client supports more than one language at a time.
Before starting any registration process, the operator can choose the languages amongst the configured ones.
To know more about setting up the reference registration client, refer to the Registration Client Installation Guide.
To know more about the features present in the Registration Client, refer to the Registration Client User Guide.
The Registration Client can be operated by an operator who can be either a Supervisor or an Officer. They can login to the client application and perform various activities. The Supervisor and the Officer can perform tasks like Onboarding, Synchronize Data, Upgrade software, Export packets, Upload packets, View Re-registration packets, Correction process, Exception authentication, etc. In addition to this, the Supervisor has exclusive authority to Approve/reject registrations.
To know more about the onboarding process of an operator, refer to Operator onboarding.
The relationship of the Registration Client with other services is explained here. NOTE: The numbers do not signify a sequence of operations or control flow.
Registration Client connects to the Upgrade Server to check on upgrades and patch downloads.
All the masterdata and configurations are downloaded from SyncData-service.
Registration Client always connects to external biometric devices through SBI.
Registration Client scans the document proofs from any document scanner.
Acknowledgment receipt print request is raised to any connected printers.
Packets ready to be uploaded meta-info are synced to the Sync Status service. Also, the status of already uploaded packets is synced back to the registration Client.
All the synced packets are uploaded to the Packet Receiver service one by one.
The image below shows the setup of the Registration Client Host machine.
Registration Client comprises JavaFX UI, Registration-services libraries, and any third-party biometric-SDK.
SBI is allowed to run on loopback IP and should listen on any port within the 4501-4600 range. More than one SBI can run on the host machine. Registration Client scans the allowed port range to identify the available SBI.
Registration Client connects to the local Derby database. This is used to store all the data synced.
All the completed registration packets are stored under the packetstore directory.
.mosipkeys directory is used to store sensitive files. db.conf under this directory stores encrypted DB passwords. This is created at the start of the registration client for the first time.
TPM - is the hardware security module used to get machine identifier, secure DB password, and prove the client authenticity on auth requests and packets created in the host machine.
The registration packets and synced data are stored in the client machine.
Most of the synced data are stored in the Derby DB. Derby DB is encrypted with the bootpassword.
Derby DB boot password is encrypted with the machine TPM key and stored under .mosipkeys/db.conf.
Synced UI-SPEC/script files are saved in plain text under the registration client working directory. During sync, SPEC/script file hash is stored in derby and then the files are saved in the current working directory. Every time the file is accessed by the client performs the hash check.
Synced pre-registration packets are encrypted with a TPM key and stored under the configured directory.
The directory to store the registration packets and related registration acknowledgments is configurable.
The registration packet is a signed and encrypted ZIP.
Registration acknowledgment is also signed and encrypted with a TPM key.
The Registration Client runs background tasks to keep data synchronized with the Registration Processor. It continuously updates the server with newly created packets and syncs additional metadata to improve packet recovery in case of a client failure.
Another background task handles packet uploads. If supervisor approval is required ('y'), approved packets are uploaded in batches. If approval is not required ('n'), packets are uploaded during the next scheduled job. With this feature, the registration client has fully capable auto upload.
You can configure these settings in the Scheduled Jobs and Batch Configuration sections.
Registration Client can be customized as per a country's requirements. For details related to Registration Client configurations, refer to Registration Client configuration.
The blueprint of registration forms to be displayed in the registration client is created as json called UI-SPEC.
Every process ( NEW / LOST / UPDATE UIN / CORRECTION ) has its own UI-SPEC json.
Kernel-masterdata-service exposes APIs to create and publish UI-SPEC.
Published UI-SPEC json are versioned.
Only published UI-SPEC is synced into registration-client.
UI-SPEC json files are tamper proof, the client checks the stored file hash every time it tries to load the registration UI.
UI-SPEC json will fail to load if tampered.
Default UI Specifications loaded with Sandbox installation is available here
To know more about the developer setup, read the Registration Client Developers Guide.
Blueprint for Scalable and Interoperable Identity Systems.
This reference blueprint provides a comprehensive vision for designing and implementing a Digital ID-led DPI infrastructure. It outlines how foundational identity systems can be leveraged alongside key DPI components, enabling various use cases across both the public and private sectors. The blueprint is structured in layers of technology, governance, and service delivery, ensuring scalability, inclusivity, and compliance with legal frameworks.
Below is an explanation of its core components and their roles within the ecosystem.
1. Unique Digital Identity
At the core of the system is the Unique Digital Identity, which establishes a singular, definitive identity for every individual. This digital identity forms the backbone of all operations, ensuring secure identification and verification across diverse domains.
2. ID Project Custodian
The ID Project Custodian, whether a designated authority, ministry, or department, oversees this infrastructure. This custodian is crucial for maintaining governance, regulatory compliance, and operational efficiency, ensuring that all identity services align with national policies and frameworks.
3. Infrastructure Layer
Supporting the ecosystem is a robust Infrastructure Layer, consisting of cloud infrastructure and connectivity. The cloud ensures scalability, resilience, and the ability to manage large volumes of identity data. The connectivity layer ensures the system's accessibility, making it functional in both urban and remote areas.
4. Foundational ID Platform
At the heart of the blueprint is the Foundational ID Platform, a centralized framework for issuing and managing foundational IDs. This platform underpins all identity-related services, ensuring secure identity handling and enabling core functions like registration, lifecycle management, verification, authentication, and e-KYC (Electronic Know Your Customer). These services are essential for building trusted interactions across all sectors.
5. Core & Augmented Services
Now that we have established the core layers to anchor trust, we can expand functionality through augmented services, such as eSignature capabilities. These enable secure digital transactions and help governments transition from traditional in-person signatures. These added features enhance the system's utility, which is especially crucial for enabling paperless workflows.
6. Accessibility and Inclusivity
To ensure widespread adoption and accessibility, the system features a Multi-Channel Access Layer that enables interaction through web, mobile (Apps, USSD), and physical interfaces(QR). This design ensures inclusivity by accommodating individuals with diverse backgrounds and varying levels of technological proficiency, to interact with the system effortlessly.
7. Consent Management, Data Exchange and Payments
In addition to its core and augmented services, consent management and data exchange capabilities are crucial for advancing digitization and digital development. These capabilities facilitate the regulated sharing of information across both public and private platforms. Moreover, the integration of payment systems adds significant value to Government-to-People (G2P) use cases. Additionally, data exchange can be further enhanced through the use of Verifiable Credentials.
8. Use Cases and Benefits Delivery
This blueprint is designed to act as a catalyst for seamless service delivery and impactful use cases across both the private and public sectors. It is essential to involve the private sector in the digitization process, as it plays a key role in enabling services such as banking, e-commerce, and telecommunications, thereby streamlining operations. In the public sector, this blueprint enhances service delivery in areas like social welfare, healthcare, taxation, and education, contributing to better governance and increased citizen engagement. By adopting an overall ID-led approach, it not only accelerates the adoption of digital identity but also ensures improved governance, streamlined operations, and enhanced citizen participation.
9. Legal and Regulatory Framework
Finally, the framework operates within a robust legal and regulatory environment, complying with key legislation such as the Data Protection Act, the Cybersecurity Act, and the Electronic Transactions Act. These laws safeguard data privacy and security, ensuring that the system operates transparently, trustworthy, and in full legal compliance.
This guide details the configuration updates required in MOSIP to enable CRVS-initiated birth and death registration requests. It covers ID schema changes to add key fields, updates to authentication policies, property files, and identity mapping, along with new Camel routes and workflow settings. These changes ensure the proper handling and processing of vital events within the MOSIP ecosystem.
Before initiating an infant birth registration request from the CRVS system, updating the ID schema in MOSIP to include the necessary fields required for capturing introducer information is essential.
The following fields should be added to support the processing of infant birth registration requests:
introducerInfoToken (Optional)
Description: A user information token representing the individual reporting the infant's birth to CRVS.
Before initiating a death registration request from the CRVS system, updating the ID schema in MOSIP to include the necessary fields required for capturing information related to the deceased and informant is essential.
The following fields should be added to support the processing of death registration requests:
deceasedDeclarationDate (Optional)
Description: The date on which the individual was declared deceased.
declaredAsDeceased (Mandatory)
Description: A flag indicating that the individual has been officially declared deceased.
typeOfDeath (Optional)
Description: Specifies the nature of the death, such as natural or jurisdictional.
deceasedInformer (Optional)
Description: A user information token representing the individual reporting the death to CRVS.
After updating the ID schema with the necessary fields for birth/death registration, corresponding changes must be applied to the default authentication policy. This step ensures that the new fields are correctly reflected in the ID authentication module particularly required when the authentication process involves the national ID of a deceased individual.
To include the new attributes in the authentication policy:
Update the existing policy_file_id by appending the newly added fields.
Execute the upgrade script to apply the changes.
Below is a sample SQL script for updating default-authpolicy to include the field declaredAsDeceased:
UPDATE pms.auth_policy SET policy_group_id='mpolicygroup-default-auth', "name"='mpolicy-default-auth', descr='mpolicy-default-auth', policy_file_id='{"shareableAttributes":[{"attributeName":"fullName","source":[{"attribute":"fullName"}],"encrypted":true},{"attributeName":"dateOfBirth","source":[{"attribute":"dateOfBirth"}],"encrypted":true},{"attributeName":"gender","source":[{"attribute":"gender"}],"encrypted":true},{"attributeName":"phone","source":[{"attribute":"phone"}],"encrypted":true},{"attributeName":"email","source":[{"attribute":"email"}],"encrypted":true},{"attributeName":"addressLine1","source":[{"attribute":"addressLine1"}],"encrypted":true},{"attributeName":"addressLine2","source":[{"attribute":"addressLine2"}],"encrypted":true},{"attributeName":"addressLine3","source":[{"attribute":"addressLine3"}],"encrypted":true},{"attributeName":"region","source":[{"attribute":"region"}],"encrypted":true},{"attributeName":"province","source":[{"attribute":"province"}],"encrypted":true},{"attributeName":"city","source":[{"attribute":"city"}],"encrypted":true},{"attributeName":"postalCode","source":[{"attribute":"postalCode"}],"encrypted":true},{"attributeName":"zone","source":[{"attribute":"zone"}],"encrypted":true},{"attributeName":"preferredLang","source":[{"attribute":"preferredLang"}],"encrypted":false},{"attributeName":"individualBiometrics","group":"CBEFF","source":[{"attribute":"individualBiometrics"}],"encrypted":true,"format":"extraction"},{"attributeName":"declaredAsDeceased","source":[{"attribute":"declaredAsDeceased"}],"encrypted":true}],"dataSharePolicies":{"typeOfShare":"Data Share","validForInMinutes":"30","transactionsAllowed":"2","encryptionType":"Partner Based","shareDomain":"datashare.datashare","source":"ID Repository"}}' , policy_type='DataShare', "version"='1', policy_schema='https://schemas.mosip.io/v1/auth-policy', valid_from_date='2025-03-17 11:53:55.388', valid_to_date='2025-04-28 09:37:00.000', is_active=true, cr_by='admin', cr_dtimes='2025-03-17 11:53:55.388', upd_by='admin', upd_dtimes='now()', is_deleted=false, del_dtimes=NULL WHERE id='mpolicy-default-auth';The following property files have been updated with the mentioned properties to support the new functionality:
mosip.kernel.idobjectvalidator.mandatory-attributes.reg-processor.crvs_new
Mandatory attributes for infant birth registration flow.
mosip.kernel.idobjectvalidator.mandatory-attributes.reg-processor.crvs_death
Mandatory attributes for death registration flow.
provider.packetreader.crvs1
Packet reader for the source with the name CRVS1. This property should be updated if the source name is changed.
provider.packetwriter.crvs1
Packet writer for the source with the name CRVS1. This property should be updated if the source name is changed.
deceasedDeclarationDate
declaredAsDeceased
typeOfDeath
registration-processor-camel-routes-crvs_death-default.xml New Camel route for death registration packet processing.
registration-processor-camel-routes-infant-crvs_new-default.xml New Camel route for infant birth registration packet processing.
registration.processor.additional-process.category-mapping
Mapping of the additional process to the internal process.
registration.processor.vid-support-for-update
Enables VID support for updates.
mosip.regproc.workflow-manager.instance.api-id
Unique ID for the workflow instance API.
mosip.regproc.workflow-manager.instance.version
A version of the workflow instance API.
registration.processor.notification.additional-process.category-mapping
Mapping of the additional process to the internal process for notification.
For more details on ID schema and configurations please refer here.
IDA (ID Authentication) module in MOSIP is an independent service that enables seamless identity verification using data from any system. Multiple IDA modules can run from a single issuer, providing services like authentication, OTP generation, and internal processes.
MOSIP recommends using eSignet for authentication, which leverages the IDA module to ensure secure and unified identity verification. eSignet simplifies the process by streamlining authentication across services, ensuring compliance with MOSIP’s security protocols. This enables both governmental and private entities to securely authenticate residents without needing multiple solutions.
Read more about eSignet and its capabilities here. The typical authentication flow is illustrated below:
The following types of authentication are offered by MOSIP's ID Authentication (IDA) module and are utilized through eSignet for ID verification by external parties:
MOSIP offers a yes/no API that can be used for the verification of attributes supplied along with authentication factors. The API verifies the identifier and the provided demographic attributes and also validates other authentication factors such as the OTP or biometrics and responds with a yes or a no. Successful verification of the data results in a yes. This kind of API can be typically used to support the verification of a limited set of demographic data about the person or for simple presence verification when biometrics are used.
MOSIP additionally offers a KYC API, which can be used to get an authorized set of attributes for the resident in the response of the API. This API is intended for use by authorized relying parties to perform KYC requests. The authentication includes an identifier along with authentication factors such as OTP and biometrics. The information returned is governed by a policy. Different relying parties can be provided with different KYC data based on their needs. The policy helps implement selective disclosure as part of the KYC data. The data thus returned is digitally signed by the server and can be used by the relying party with confidence.
The authentication APIs support multiple factors. These can be:
Biometric: Finger, face, iris
Demographic: Name, date of birth, age, gender, etc.
OTP: One-Time Password Based on the level of assurance needed for the transaction, the relying party can decide which factors are sufficient for identity verification.
Password-based authentication.
Biometric authentication is performed using third-party matcher SDK that performs 1:1 matches on a given modality. Each biometric modality is treated as an independent factor in authentication.
All authentications in MOSIP operate on a 1:1 matching principle. This requires the authentication request to include an identifier for the individual, along with authentication factors to verify the identity. MOSIP supports multiple identifiers for each person, which enhances privacy and prevents profiling. The individual can be authenticated using their UIN or alternate identifiers like VIDs. When a VID is used, additional checks ensure it hasn't expired or been revoked. The expiration of a VID is governed by the policy set during its creation.
To understand VIDs and their characteristics, read more about VID.
In certain contexts, identity verification can be performed anonymously for one-time use. However, when identity verification is tied to transactions requiring identity assurance, it becomes necessary to link the user's identity to the transaction. This is done by providing relying parties with a "sticky" token identifier, which can serve as a reference ID for the individual in their system. When authentication is successful, the APIs return a token. Depending on the relying party’s policies, the token may be random or "sticky." The relying party is expected to store this token for future reference, customer identification, and audit or redressal purposes.
Learn more about the Token ID.
Read more about parties and policies.
MOSIP has a provision for specifying the user consent associated with an authentication transaction. This can be stored for audit purposes and the authentication flow can be extended to verify the consent if needed.
MOSIP has a provision to help protect against the misuse of identity. For any report of lost identity or detection of fraudulent activity by fraud, the module can require the temporary suspension of authentication activities on a user. This is enabled by the hotlisting feature. The authentication service checks if the identifier used is hotlisted and if so, the authentication process is aborted and fails. The hotlisting service can be used by helpdesk and fraud solutions to list and delist the identifiers that need to be blocked temporarily.
Demographic data normalization is the process of applying rules for formatting of the demographic data (such as the address) into a common format before demographic data matching is verified during the demographic authentication in IDA. For example, for address lines, the '1st Street' can be replaced with '1 st' and 'C/o' can be removed from both the input and database data before the match is verified. These rules will be different for different languages, and may be configured/implemented differently.
The ID-Authentication Demographic data normalization mentioned here is specific to the Demo-SDK reference implementation of the Kernel Demographic API. It takes the below configuration to apply the name and address normalization rules.
For any other custom implementation of the normalization, the Demo-SDK needs to be implemented accordingly.
The below configuration is used to define the separator for normalizing regex (pattern) and the replacement word. The default is set to '='.
ida.norm.sep==
The format for configuring the name/address normalization rules for any language is given below:
ida.demo.<name/address/common>.normalization.regex.<languageCode/any>[<sequential index starting from 0>]=<reqular expression>${ida.norm.sep}<replacement string>
* name/address/common - type of normalization, common applies to both name and address
* languageCode - this is the code for languages like hin, eng, any('any' applies to any language)If replacement string is not specified, the regular expression will be replaced with empty string.
Note: It is recommended that the sequence is not broken in the middle otherwise all normalization properties will not be read for the particular type.
ida.demo.address.normalization.regex.eng[0]=[CcSsDdWwHh]/[Oo]
ida.demo.address.normalization.regex.eng[1]=(M|m|D|d)(rs?)(.)
ida.demo.address.normalization.regex.eng[2]=(N|n)(O|o)(\\.)?
ida.demo.address.normalization.regex.eng[3]=[aA][pP][aA][rR][tT][mM][eE][nN][tT]${ida.norm.sep}apt
ida.demo.address.normalization.regex.eng[4]=[sS][tT][rR][eE][eE][tT]${ida.norm.sep}st
ida.demo.address.normalization.regex.eng[5]=[rR][oO][aA][dD]${ida.norm.sep}rd
ida.demo.address.normalization.regex.eng[6]=[mM][aA][iI][nN]${ida.norm.sep}mn
ida.demo.address.normalization.regex.eng[7]=[cC][rR][oO][sS][sS]${ida.norm.sep}crs
ida.demo.address.normalization.regex.eng[8]=[oO][pP][pP][oO][sS][iI][tT][eE]${ida.norm.sep}opp
ida.demo.address.normalization.regex.eng[9]=[mM][aA][rR][kK][eE][tT]${ida.norm.sep}mkt
ida.demo.address.normalization.regex.eng[10]=1[sS][tT]${ida.norm.sep}1
ida.demo.address.normalization.regex.eng[11]=1[tT][hH]${ida.norm.sep}1
ida.demo.address.normalization.regex.eng[12]=2[nN][dD]${ida.norm.sep}2
ida.demo.address.normalization.regex.eng[13]=2[tT][hH]${ida.norm.sep}2
ida.demo.address.normalization.regex.eng[14]=3[rR][dD]${ida.norm.sep}3
ida.demo.address.normalization.regex.eng[15]=3[tT][hH]${ida.norm.sep}3
ida.demo.address.normalization.regex.eng[16]=4[tT][hH]${ida.norm.sep}4
ida.demo.address.normalization.regex.eng[17]=5[tT][hH]${ida.norm.sep}5
ida.demo.address.normalization.regex.eng[18]=6[tT][hH]${ida.norm.sep}6
ida.demo.address.normalization.regex.eng[19]=7[tT][hH]${ida.norm.sep}7
ida.demo.address.normalization.regex.eng[20]=8[tT][hH]${ida.norm.sep}8
ida.demo.address.normalization.regex.eng[21]=9[tT][hH]${ida.norm.sep}9
ida.demo.address.normalization.regex.eng[22]=0[tT][hH]${ida.norm.sep}0
# Note: the common normalization attributes will be replaced at the end.
# Special characters are removed : . , - * ( ) [ ] ` ' / \ # "
# Replace special char with space. Trailing space is removed from property. As a workaround first replacing with " ." then removing the "."
ida.demo.common.normalization.regex.any[0]=[\\.|,|\\-|\\*|\\(|\\)|\\[|\\]|`|\\'|/|\\|#|\"]${ida.norm.sep} .
# Trailing space is removed from property. As a workaround first replacing with " ." then removing the "."
ida.demo.common.normalization.regex.any[1]=\\s+${ida.norm.sep} .
ida.demo.common.normalization.regex.any[2]=\\.${ida.norm.sep}For non-english languages, the non-english words needs to be converted into UTF-16 and then copied to the configuration. For example, convert the Unicode characters to UTF-16.
Before conversion: ida.demo.address.normalization.regex.hin[0]=पहली${ida.norm.sep}पहला
After conversion: ida.demo.address.normalization.regex.hin[0]=\u092a\u0939\u0932\u0940${ida.norm.sep}\u092a\u0939\u0932\u093e
This repository contains the UI code for the Resident portal. To know more about the features and functions present on the portal, refer here.
Install node.js- To build the angular code using angular cli that runs on node, recommended Node: 14.17.3, Package Manager: npm 6.14.13
Install angular cli – To install angular cli for building the code into deployable artifacts. Follow the following steps to install angular cli on your system.
npm install -g @angular/cli (to install angular cli)
ng --version (to verify angular is installed in the system) We recommend Angular CLI: 7.2.1
Check out the source code from GIT – To download the source code from git, follow the steps below to download the source code on your local system.
git clone https://github.com/mosip/resident-ui.git (to clone the source code repository from git)
Build the code
Follow the steps below to build the source code on your system.
Navigate to the resident-ui directory inside the cloned repository.
Run the command ng build "--prod" "--base-href" "." "--output-path=dist" in that directory to build the code.
Build Docker image
Follow the steps below to build the docker image on your system.
docker build -t name . (replace name with the name of the image you want, "." signifies the current directory from where the docker file has to be read.)
Example: docker build -t residentui .
Run the Docker image
Follow the steps to build a docker image on your system.
docker run –d –p 80:80 --name container-name image-name (to run the docker image created with the previous step,-d signifies to run the container in detached mode, -p signifies the port mapping left side of the":" is the external port that will be exposed to the outside world and the right side is the internal port of the container that is mapped with the external port. Replace container-name with the name of your choice for the container, replace image-name with the name of the image specified in the previous step)
Example: docker run -d -p 8080:8080 --name nginx residentui
Now you can access the user interface over the internet via a browser.
Example: http://localhost:8080/#/dashboard
Build & deploy the code locally
Follow the steps below to build the source code on your system.
Navigate to the resident-ui directory inside the cloned repository. Then, run the following command in that directory:
npm install
ng serve
Now, you can access the user interface via the browser.
Example: http://localhost:4200
UI specs of resident module are used to configure the form fields across Resident Portal. UI specs are saved as a JSON file with a list of fields. Each field has a set of attributes/ properties that can be configured which affects the look and feel along with the functionality of the field.
Below is the list of all the properties available for each field in the Resident Portal UI specs:
id
The id property is the unique id provided to a field to uniquely identify it. The id can be alpha-numeric without any spaces between them.
"id":"zone"
description
This is a non-mandatory property used to describe the field.
"description": "zone"
labelName
This property defines label name for the field. This property has sub-attributes as the language code (eng, fra, ara) to store data in different languages based on the country's configuration.
"labelName": { <br>"eng": "Zone", <br>"ara": "منطقة", <br>"fra": "Zone"}
controlType
This property defines the kind of UI component to be used to capture data in UI. Currently the values that can be used are: <br/> • textbox (creates multiple textboxes for each field to capture input in all the languages configured for the setup)<br/>• dropdown <br/>• fileupload <br/> • date (creates a date picker)<br/> • ageDate (creates a date picker along with number toggle to provide age directly)<br/> • checkbox (creates a toggle checkbox for the field which can be checked or unchecked)<br/> • button (creates dropdown options as buttons, which user can select easily)
inputRequired
This property decides if the field is to be displayed in the UI form or not. It is useful for some internal fields which do not need any input from the user.
required
This is a mandatory property which decides if the field is a required form field or not. If true, user must provide some value for the field.
type
This property defines the data type of the value corresponding to this field. The data types supported are “number”, “string” and “simpleType”.<br/> The type “simpleType” means that language specific value will be saved along with the language code.
fieldType
This property is relevant when control type is “dropdown” or “button”. It defines if the field is of type “default” or “dynamic”. <br/>If it is “dynamic” then all the options for the dropdown are populated from the “master.dynamic_field” table otherwise they are populated from corresponding table example “master.gender”
subType
This is relevant for 2 cases:<br/>1. When control type is “dropdown”/ “button” and the type is “dynamic” then “subtype” can be used to populate the options for the field with the data available in “master.dynamic_field” table.<br/>2. When the control type is “fileupload”, then the property ”subtype” is used to map the field to a “code” in the “master.doc_category” table.
validators
This property enables us to add the list of language specific validators for the field. <br/>* Each validator can have the below fields,<br/>“langCode”,<br/>“type”,<br/>“validator”,<br/>“arguments”,<br/>“errorMessageCode”<br/><br/>* The “type” defines the validation engine type.<br/>* The “validator” gives the pattern/ methodName/ scriptName/ expression<br/>* The “arguments” array to is used to hold parameter or dependent field ids required for validation<br/>* The “errorMessageCode” can be given to add custom error message which will be shown to the user when the validation fails. The error message corresponding to this code will be picked from language specific i18n translation files. In case “errorMessageCode” is not given then generic error message will be displayed to the user when validation fails. <br/><br/>Currently, regex is supported by MOSIP.<br/>If “langCode” is not added then same “validator” is used for all languages of the field.
<br>"validators": [{ <br>"langCode": "eng", <br>"type": "regex", <br>"validator": "^(?=.{0,50}$).*", <br>"arguments": [], <br>"errorMessageCode": "UI_1000"<br>},{ <br>"langCode": "ara", <br>"type": "regex", <br>"validator": "^[A-Z]+$", <br>"arguments": []<br>},{ <br>"langCode": "fra", <br>"type": "regex",<br>"validator": "^[A-Z]+$", <br>"arguments": []<br>}]
locationHierarchyLevel
This attribute is mandatory for the location dropdown fields. <br/>The value will be as per corresponding location hierarchy level from the master.loc_hierarchy_list table.
{<br>"id":"region",<br>"controlType":"dropdown",<br>"fieldType":"default",<br>"type":"simpleType",<br>"parentLocCode":"MOR",<br>"locationHierarchyLevel":1<br>..}
parentLocCode
This attribute is to be used only for location dropdown fields and it is optional. <br/>The corresponding location dropdown will be pre populated in UI based on the value in “parentLocCode”. <br/>If this attribute is NOT mentioned in UI specs, then the dropdown will be populated based on selection in its parent dropdown, as before. <br/>For the first dropdown, in case this attribute is not mentioned in UI specs then the value from “mosip.country.code” configuration will be used for backward compatibility.
{<br>"id":"region",<br>"controlType":"dropdown",<br>"fieldType":"default",<br>"type":"simpleType",<br>"parentLocCode":"MOR",<br>"locationHierarchyLevel":1<br>..}
alignmentGroup
* This property is used to group the fields on the screen. <br>* If it is skipped, then all the fields will appear in same sequence (horizontally layout) as they appear in UI specs. <br>* If you want the first and fifth field to be in same row in the screen, you can add this attribute with same group name. <br>* The UI is responsive so it will accommodate as many fields in one row as they will fit comfortably.
containerStyle
This is used to optionally apply some CSS styles to the UI field container.
"containerStyle": {<br>"width": "600px",<br>"margin-right": "10px"<br>}
Registration Processor (Regproc) is a backend processing engine to enable ID Lifecycle management. The diagram below shows the Registration Processor along with the other modules that contribute to issuing a Unique Identification Number(UIN) for an individual. Internally, Regproc follows the SEDA architecture where data flows via multiple stages till the UIN is issued.
The relationship of Regproc with other services is explained here. NOTE: The numbers do not signify a sequence of operations or control flow
Registration packets are uploaded by the Registration Client to the Packet Receiver.
After packet validation is done Regproc notifies the pre-registration application using the datasync service.
The quality of biometrics is checked using an external biometric SDK. This is done in Regproc's Quality Classifier stage.
The above data is shared by providing a URL that partners use to fetch data. This URL is obtained from the Datashare service.
Regproc's ABIS Middleware stage communicates with ABIS via Activemq. The ABIS performs deduplication and sends back the result to the Queue.
Regproc stores and updates applicant demographic and biometric information in the ID Repository. Also, activate or deactivate the applicant's UIN.
Regproc calls IDA Internal Authentication Service to authenticate Applicant(for update flow), introducer, operator, and supervisor(when bio auth mode is used to create packet).
After the UIN is processed the Printing Stage calls Credential Service to create credentials for print. This credential will be pushed to websub and the Printing systems will consume the same.
The Notification Service is used to send email/sms notifications to the applicant after the request processing is completed on the server.
Regproc connects to the external "Manual Adjudication System" via a queue. Regproc sends applicant information required for adjudication in the queue and the external adjudication system consumes it. The data is shared from mosip to an external adjudication system based on policy.
Regproc calls Key Manager for decrypting packets and encrypting information.
Regproc uses Masterdata Service to validate the center, machine, user, etc.
Regproc connects to Virus Scanner for scanning packets in the Packet Receiver Stage and Packet Uploader Stage
Each Stage in regproc calls Packet Manager to read information from the packet.
The Registration Processor contains several stages and services.
The registration packet flows through the various stages depending on the type of flow. See Registration Flows and Stage Sequence.
Note: The Print Stage has been renamed as the Credential Requestor Stage. For further information, please click here.
Refer to repo.
Refer to Configuration Guide.
To know more about the developer setup, read the Registration Processor Developers Guide.
Refer to API Documentation.
Pre-registration module enables a resident to:
enter demographic data and upload supporting documents,
book an appointment for one or many users for registration by choosing a suitable registration center and a convenient time slot,
receive appointment notifications,
reschedule and cancel appointments.
Once the resident completes the above process, their data is downloaded at the respective registration centers before their appointment, thus, saving enrollment time. The module supports multiple languages.
MOSIP provides backend APIs for this module along with a reference implementation of .
User provides consent
The user provides demographic information
User uploads supporting documents (Proof of Address, Birth certificate, etc.)
A pre-registration request ID known as is generated and provided to the user.
Note: The AID was formerly called PRID in the pre-registration context.
The user selects a registration center based on postal code, geo-location, etc.
The available slots are displayed
An option to cancel and re-book the appointment is made available
An acknowledgment is sent via email/SMS
The user can print the acknowledgment containing AID and QR code.
This QR code can be scanned at the in-person registration centers.
The user provides the AID/ QR code at the registration center.
The registration form gets pre-filled with the pre-registration data.
The relationship of the pre-registration module with other services is explained here.
Fetch details with the help of Syncdata service.
Fetch a new OTP for the user on the login page.
Log all events.
Pre-Registration interacts with Keycloak via . The Pre-Reg module communicates with endpoints of other MOSIP modules. However, to access these endpoints, a token is required. This token is obtained from Keycloak.
The database used by pre-reg.
Generate a new AID for the application.
Send OTP in the email/SMS to the user.
Registration Processor uses reverse sync to mark the pre-reg application as consumed.
Registration clients use the to get the pre-reg application details for a given registration center, booking date, and AID.
Request data from the MasterData service to get data for dropdowns, locations, consent forms etc.
Pre-registration module consists of the following services:
For more details, refer to the .
MOSIP provides a reference implementation of the pre-registration portal that may be customized as per country needs. The sample implementation is available at the . For getting started with the pre-registration, refer to the
To access the build and read through the deployment instructions, refer to the .
For details related to Pre-registration configurations, refer to .
To know more about the developer setup, read the .
Refer to .
.
The ".well-known" folder is a convention used in web development to provide a standardized location for certain files or resources that need to be publicly accessible and discoverable. It typically resides at the root level of a website or web server. The purpose of this folder is to make it easy for web clients (browsers, applications, or services) to find important files or resources related to web services and security.
MOSIP can use the ".well-known" directory to serve the following purposes:
Standardization: To provide a standardized location for specific public files and resources related to web services and security. It makes it easier for developers and web clients using MOSIP to know where to look for important information.
Security: Security-related files and resources can be placed in the ".well-known" directory, such as the public certificate for encryption and signature verification can be placed here.
Interoperability: By following the ".well-known" convention, web developers using MOSIP can ensure interoperability with various web standards and protocols. For example, MOISP shares the context file which contains the structure of its Verifiable Credentials.
Ease of Configuration: Web servers can be configured to serve files from the ".well-known" directory without needing custom configurations for each specific resource. This simplifies the server setup and maintenance process.
Transparency: For matters related to security policies and contact information, such as in the "security.txt" file, placing them in a well-known location makes it transparent and easily accessible to anyone interested in the website's security practices.
MOSIP's ".well-know" directory contains three files,
controller.json
mosip-context.json
public-key.json
The "controller.json" file is used in MOSIP to share the details of the public key using which a MOSIP-issued verifiable credential can be asserted.
The "mosip-context.json" file contains the schema of the subject in the MOSIP-issued verifiable credential.
The "public-key.json" file contains the public key using which the signature of the MOSIP-issued verifiable credential can be asserted.
The Resident Portal Guide for Collab Environment provides a comprehensive introduction to the services available on Resident Portal, as well as a guide on how to navigate its features.
Resident Portal is a user-friendly web-based platform designed to assist residents in accessing services related to their Unique Identification Number (UIN). This portal allows residents with a UIN to conveniently manage their UIN, protect their identity, track requests, and obtain personalized cards. For a more detailed overview of the features offered, please visit .
This Resident Portal Demo Setup guide serves as a tool to demonstrate the impressive capabilities of MOSIP's system. Let's embark on this journey together to explore the potential of Resident Portal.
Please note that for developers setting up Resident Portal locally, refer to the .
Accessing Resident Portal in Collab environment does not require any complex setup.
All you need is a UIN or a VID and you are good to go!
To get your UIN credentials for Collab environment follow the below steps:
The provision of a UIN (Unique Identification Number) as a demo credential will enable you to have a firsthand experience of the Resident Portal's capabilities and explore its various features.
Now you can self generate your own UIN Credential using the .
Click on the Get UIN button located at the top-right corner of the page. This will open the , Alternatively, you can simply click on this to self register. You need to duly fill the self registration form.
On successful registration the UIN is sent to you over the email you used for registration, For more details you follow the .
Note: Please use 111111 as the OTP, for any OTP-based feature in the Collab environment.
Step 1: Access Resident Portal
Visit the following URL to access Resident Portal in Collab environment:
Step 2: Login
The recommended method for accessing the Resident Portal in the Collab environment is to use a valid UIN (Unique Identification Number), which can be obtained by completing the form provided. This is one of the options available for logging in and accessing UIN-related services on the Resident Portal.
There are multiple methods for logging in to access UIN services on the Resident Portal:
Login with Inji: To download and use the Inji application, click .
Login with Biometrics: To set up a biometrics device on your system, click .
Login with OTP (One-Time Password): Enter UIN/VID received from our end and use 111111 as OTP, for login to Resident Portal in Collab environment.
Step 3: Explore the features of Resident Portal
To access registration related information, click .
Go to Get Information section.
Click Registration Centers to get the list of Registration Centers near you or to look for Registration Centers based on location hierarchy.
Click Supporting Documents to get the list of documents that Resident Portal supports.
To download the UIN card or to know the status of your AID, click .
Next, go to Get My UIN section.
To book an appointment for a new enrolment, click .
Go to Book an Appointment section.
Explore the steps of Pre-registration Portal to book an appointment.
To verify your email ID or phone number, click .
For Email verification- Use the OTP received on your email, as provided at the time of UIN creation.
For Phone number verification - Since our mobile services are temporarily unavailable, please use the email services.
To access all the features of Resident portal in MOSIP, click to login.
For more information, refer to our .
To get more information about Resident Portal, click .
You will be able to explore and get a better understanding of Resident Portal configurations, UI, deployment, and OIDC client configuration to mention a few.
By adhering to these instructions, you will acquire the necessary knowledge to effortlessly configure the Resident Portal and proficiently utilize all of its functionalities.
If you require any assistance or encounter any issues during the testing and integration process, kindly reach out to us through the support mechanism provided below.
Navigate to .
Provide a detailed description about the support you require or provide detailed information about the issue you have encountered, including steps to reproduce, error messages, logs and any other relevant details.
Thank you. Wishing you a pleasant experience!
{
"@context": "https://w3id.org/security/v2",
"id": "https://api.collab.mosip.net/.well-known/controller.json",
"assertionMethod": [
"https://api.collab.mosip.net/.well-known/public-key.json"
]
}{
"@context": [{
"@version": 1.1
},"https://www.w3.org/ns/odrl.jsonld", {
"mosip": "https://api.collab.mosip.net/mosip#",
"schema": "http://schema.org/",
"rdf": "http://www.w3.org/1999/02/22-rdf-syntax-ns#",
"vcVer": "mosip:vcVer",
"UIN": "mosip:UIN",
"addressLine1": {
"@id": "https://api.collab.mosip.net/mosip#addressLine1",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"addressLine2": {
"@id": "https://api.collab.mosip.net/mosip#addressLine2",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"addressLine3": {
"@id": "https://api.collab.mosip.net/mosip#addressLine3",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"city": {
"@id": "https://api.collab.mosip.net/mosip#city",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"gender": {
"@id": "https://api.collab.mosip.net/mosip#gender",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"residenceStatus": {
"@id": "https://api.collab.mosip.net/mosip#residenceStatus",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"dateOfBirth": "mosip:dateOfBirth",
"email": "mosip:email",
"fullName": {
"@id": "https://api.collab.mosip.net/mosip#fullName",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"phone": "mosip:phone",
"postalCode": "mosip:postalCode",
"province": {
"@id": "https://api.collab.mosip.net/mosip#province",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"region": {
"@id": "https://api.collab.mosip.net/mosip#region",
"@context": {"value": "rdf:value", "lang": "@language"}
},
"biometrics": "mosip:biometrics"
}]
}{
"@context": "https://w3id.org/security/v2",
"type": "RsaVerificationKey2018",
"id": "https://api.collab.mosip.net/.well-known/public-key.json",
"controller": "https://api.collab.mosip.net/.well-known/controller.json",
"publicKeyPem": "-----BEGIN PUBLIC KEY-----\r\nMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA07+Esb/PSV2e5p/afi4O\r\n6ICRD699POqCWzt9obGBPHdmPTD3QYU3c/CnEPNHBzvQKWcaIWRmwTi8yGAwyUU9\r\n5ESU9/o78ACHrcFRIdluuiQuhDP4ojQLDpX/dPULPc/dt96b5t1uPhELnySq/EPr\r\n6hcqGuMyLl/yfKr/vQdaTqKmmrm8gTTnzsQ4jvpeucrDEBqm5LtSzYQb4PRMQe0u\r\nhrnZjbVmoUKCNpXXrKMfswqLhz2gInkN7+SJToCEcEj1f2tJYUsL0LufceEQQFy0\r\nKaq+Xu1Jx1OwnRP1HhS8aepLct8O1H3e0DrMCLgSZ89HiSpWQ+0DMKDMdROCm7uU\r\noQIDAQAB\r\n-----END PUBLIC KEY-----"
}Registration Processor(Regproc) is a backend processing engine to enable the ID Lifecycle management. It has several stages and services, registration packet flows through various stages depending on the type of flow.
The documentation here will guide you through the prerequisites required for the developer's setup.
Below are a list of tools required in Registration Processor:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up Registration Processor on your local system:
1. Download lombok.jar and settings.xml from here.
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to conf folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the registration repository from and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true -DskipTests=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available here with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone mosip-config repository.
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all the config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As Registration Processor is using two properties files, registration-processor-default and application-default, you will have to configure them according to your environment. The same files are available here for reference.
5. To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
8. Before running any application of Registration Processor, replace the below properties in bootstrap.properties:
spring.cloud.config.uri=http://localhost:51000/config
spring.cloud.config.label=master
spring.profiles.active=default
spring.profiles.active can be dmz or mz(default)
9. An alternative approach to start the application is to place the dependency of application to be executed in the pom of MOSIP stage executor update maven and place above mentioned properties in the bootstrap.properties and then start MOSIP stage executor.
The documentation here will guide you through the pre-requisites and the other necessary details required for Android Registration Client developer setup.
The android-registration-client repository contains the Android Registration Client software for MOSIP. The feature-flutter branch focuses on integrating Flutter into the client.
To set up the Android Registration Client with Flutter and Android Studio, follow the steps below:
Flutter SDK (3.10.4): Install Flutter by following the official Flutter installation guide.
Android Studio (or Any IDE of your choice): Download and install Android Studio from the official Android Studio website.
The develop branch of android-reg-client is currently being actively developed. If you wish to access this branch, you can clone the repository by executing the following command in your terminal. Alternatively, you can download one of the releases available in the repository's release section.
git clone -b feature-flutter https://github.com/mosip/android-registration-client.gitActive Branches:
release-1.0.x(developer release branch)
develop(active development branch)
To begin, launch Android Studio.
Next, select Open an existing Android Studio project and navigate to the cloned repository.
Open the android-registration-client directory as a project in Android Studio.
In order to integrate Flutter with Android Studio, install the Flutter plugin by accessing File > Settings > Plugins and searching for Flutter. Proceed to click on Install to install the plugin.
To ensure proper functionality, configure the Flutter SDK path by navigating to File > Settings > Languages & Frameworks > Flutter and specifying the Flutter SDK path as the location where you have installed Flutter.
Finally, save the changes by clicking on the "Apply" button.
Customizing the Registration Client
Styling of the application can be configured by modifying these files lib/utils/app_style.dart, lib/utils/app_config.dart
Application language bundles can be added to this path lib/l10n After adding the bundle run the below command to generate Localization data (Required for the first time).
flutter gen-l10nThe label and application logo can be changed here android/app/src/main/AndroidManifest.xml
The pigeon.sh file consists of the necessary commands for downloading dependencies and generating Flutter - Android native communication code. Please execute the pigeon.sh file or execute the commands within the file separately.
Ensure you have connected an Android device or initiated an Android emulator.
Open the terminal within Android Studio or use an external terminal.
Navigate to the android-registration-client directory.
Run the following command to build and execute the application:
flutter runExecute the commands below to debug and release the APK
// Debug APK
flutter build apk --debug
// Release APK
flutter build apk --releaseThe Mock MDS tool can be utilized to simulate the functionalities of biometric devices. The Mock MDS application is compliant with CTK standards and can serve as a substitute for Android SBI modules during testing and validation.
Install the Mock MDS application.
Access the Settings menu.
Under Device Configuration, choose Registration from the dropdown menu.
In P12 Configuration:
Enter the necessary credentials for the Device Key and upload the Device P12 file.
Enter the required credentials for the FTM Key and upload the FTM P12 file.
Complete all fields in MOSIP IDA Configuration.
In Modality Configuration, specify the quality score for Face, Finger, and Iris scans(these values can also be adjusted during testing).
Click on the Save button.
Go back to the Home Page and select LOAD AND VALIDATE CERTIFICATES.
A toast message will be displayed indicating the success of the validation process.
Note: To view the released version of the Mock SBI APK, click here.
To download the Mock SBI APK, click on camera-mds.zip.
If you would like to contribute to the Android Registration Client, please follow the guidelines outlined here.
The Android Registration Client is licensed under the MIT License.
If you encounter any issues or have any questions, please open an issue on the GitHub repository.
GitHub- mosip/android-registration-client: Reference Android Registration Client Software - WIP
Registration Client is a thick Java-based client where the resident's demographic and biometric details are captured along with the supporting documents in online or offline mode.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in Registration Client:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
Git
Follow the steps below to set up Registration Client on your local system:
For the code setup, clone the Registration Client repository and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true -DskipTests=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external dependency that is available here with different versions. (E.g.: You can download mock-sdk.jar and add to registration-services project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Registration Client UI is developed using JavaFX and the UI pages are fxml files which can be opened using a tool called Scene Builder. The JavaFX integration with the Eclipse IDE is provided with the e(fx)clipse tool. Go to Help → Install New Software → Work with → Add. Give Name and Location as mentioned in below image.
Once the software is installed, you will be prompted to restart your IDE.
3. Download openjfx-11.0.2_windows-x64_bin-sdk.zip from here, unzip and place it in your local file system. This folder contains list of javafx related jars that are necessary for running Registration Client UI.
4. We can change the application environment in the file registration-services\src\main\resources\props\mosip-application.properties by modifying the property mosip.hostname
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it creates a Java application which you can see in debug configurations.
2. Open the arguments and pass this --module-path C:\Users\<USER_NAME>\Downloads\openjfx-11.0.2_windows-x64_bin-sdk\javafx-sdk-11.0.2\lib --add-modules=javafx.controls,javafx.fxml,javafx.base,javafx.web,javafx.swing,javafx.graphics --add-exports javafx.graphics/com.sun.javafx.application=ALL-UNNAMED in VM arguments.
3. Click Apply and then debug it (starts running). You can see a popup which shows informative messages of what is happening in background while Registration Client UI is loading and the application will be launched.
Dockerfile is available under registration-client repository.
The concept here is to run nginx in the docker container from which registration-client.zip is hosted and also registration-client on the field will connect to this nginx to check for new updates or changes.
Note: We refer this nginx server as registration-client download and upgrade server.
While running the registration-client docker container we need to pass below environment variables:
Required
client_version_env : pom version of the registration client build
client_upgrade_server_env : public URL of this nginx server
reg_client_sdk_url_env : URL to download sdk zip. Make sure to have SDK jar and its dependent jars in the zip.
artifactory_url_env : artifactory URL to download below mentioned runtime dependencies
“${artifactory_url}/artifactory/libs-release-local/icu4j/icu4j.jar”
“${artifactory_url}/artifactory/libs-release-local/icu4j/kernel-transliteration-icu4j.jar”
“${artifactory_url}/artifactory/libs-release-local/clamav/clamav.jar”
“${artifactory_url}/artifactory/libs-release-local/clamav/kernel-virusscanner-clamav.jar”
keystore_secret_env : password of the keystore.p12 file
host_name_env : syncdata-service public domain name
signer_timestamp_url_env : URL of timestamp server to timestamp registration-client jar files.
Need to mount a volume to “/home/mosip/build_files” with below files
logback.xml
Client.crt : Signer certificate to be added in the registration-client build for jar sign verification.
keystore.p12 : Store private key used to sign the registation-client and registration-services jar files with “CodeSigning” alias.
maven.metadata.xml : Holds the current version of registration-client hosted in the upgrade server.
Optional
reg_client_custom_impls_url_env : URL to download scanner custom implementation jars(runtime dependency).
Finally, you can download the registration client zip from below URL. {registratiionclient download server domain name/ip}/registration-client/{client_version}/reg-client.zip}
References
Run (https://github.com/mosip/mosip-infra/blob/develop/deployment/v3/mosip/regclient/create-signing-certs.sh) to generate Client.crt and keystore.p12.
To get the content of maven-metadata.xml and logback.xml check (https://github.com/mosip/mosip-helm/blob/develop/charts/regclient/templates/configmap.yaml)
Note: The change in nomenclature from 'Print Stage' to 'Credential Requestor Stage' was implemented to enhance clarity and better reflect its expanded functionality.
In MOSIP 0.9.0, the "print stage" was primarily designed to facilitate the submission of printing requests. The core functionality of print stage revolved around initiating a request for the physical printing of credentials. However, as the system evolved and incorporated additional features, the scope of the print stage expanded beyond its original purpose.
In the evolved approach, at the print stage, apart from processing a print request, the application enables partner-specific print capabilities. Contrary to its initial purpose, the print stage no longer serves the singular function of printing credentials. Instead, it has transformed into a multifaceted component with enhanced set of responsibilities.
In the current system, the print stage's role extends beyond traditional printing activities. Its primary function now revolves around initiating a request for credential generation once a Unique Identification Number (UIN) is generated. This request is not aimed at physical printing but serves as a mechanism to gather additional information for specific partners. These partners may require supplementary data beyond what is initially generated with the UIN.
Therefore, in the evolved approach, the print stage has transitioned from being a straightforward printing request to a more versatile component that manages the initiation of credential requests tailored to partner-specific information needs. This adaptation reflects the system's responsiveness to changing requirements and the dynamic nature of credentialing processes. This reason led us to re-name the “Print Stage” to the “Credential Requestor Stage” as this name serves the purpose of the work executed by this stage.
The Credential Requestor Stage in MOSIP, formerly known as the Print Stage, is a crucial component used to request credentials for configurable partners after the UIN is generated. This stage enables countries to share information with multiple partners, each with specific needs after UIN generation. Partners, such as Print Partners and Digital Card Partners, may require demographic or biometric information to perform operations.
The Credential Requestor Stage plays a crucial role in the MOSIP system, serving as a mechanism to solicit credentials from configurable partners post-UIN generation. In this context, partners, previously registered with MOSIP, require demographic and biometric data to execute their respective operations. For instance, a Print Partner necessitates specific demographic details for the purpose of printing cards. Similarly, digital card partners seek demographic information to generate digital cards. Additionally, DPGs might seek confirmation of successful UIN generation to integrate this information into their systems. The Credential Requestor Stage facilitates various use cases where the country aims to share pertinent information with multiple partners subsequent to UIN generation.
MOSIP has introduced a new partner profile for the Credential Requestor Stage. The partner profiles are maintained here.
Sample Partner Profile:
jsonCopy code{
"partners": [
{
"id": "digitalcardPartner",
"partnerId": "mpartner-default-digitalcard",
"credentialType": "PDFCard",
"template": "RPR_UIN_CARD_TEMPLATE",
"appIdBasedCredentialIdSuffix": ".pdf",
"process": null,
"metaInfoFields": null
},
{
"id": "printPartner",
"partnerId": "mpartner-default-print",
"credentialType": "euin",
"template": "RPR_UIN_CARD_TEMPLATE",
"appIdBasedCredentialIdSuffix": null,
"process": null,
"metaInfoFields": null
},
{
"id": "opencrvsPartner",
"partnerId": "opencrvs-partner",
"type": "opencrvs",
"template": "RPR_UIN_CARD_TEMPLATE",
"process": ["OPENCRVS_NEW"],
"metaInfoFields": ["opencrvsBRN"]
}
]
}Field Description
id: Logical unique identifier
partnerId: Partner identifier configured in MOSIP
credentialType: Type of credential configured in MOSIP
template: Template used for generating the credential
appIdBasedCredentialIdSuffix: Applicable for special conditions where the credential ID is the application ID itself, with an optional suffix (for example, .pdf). Currently, this is applicable for digital card credentials.
process: If applicable for a particular process. If applicable for all processes, value is null
metaInfoFields: Meta information fields to be sent as additional information while generating the credential
Configuration Changes
Once the partner profile is configured, the System Integrator (SI) should make changes to the following configurations:
mosip.registration.processor.credential.partner-profiles: Specify the file name for the partner profiles. By default its → registration-processor-credential-partners.json. If a country intends to change the file name only then this configuration should be updated otherwise default configuration can be used
mosip.registration.processor.credential.default.partner-ids: Specify default partner IDs for which credentials will be created automatically
mosip.registration.processor.credential.conditional.partner-id-map: Define conditions for conditional partners. Credentials for these partners will be requested only if the conditions are met. Use MVEL expressions for conditions
mosip.registration.processor.credential.conditional.no-match-partner-ids: Specify a partner ID to be used when no conditions are met for conditional partners
Conditional Partner Requests
The stage will create credentials for default partner IDs by default
For conditional partners, credentials will be requested only if they match a particular MVEL expression
MVEL expressions can be written on any identity field as well as meta info field
If there is no condition match for conditional partners, SI can configure a no-match partner, which will be used when no conditional partner match is found
Configuration File Locations
Credential Requestor Stage Configuration: Click here to view credential requestor stage configuration details.
Partner Profile Configuration: Click here to view partner profile configuration details.
The Credential Requestor Stage configuration is an essential part of MOSIP's functionality, enabling seamless communication with partners and ensuring the secure exchange of information post-UIN generation.
Note: Ensure that configured IDs are logically unique and consistent across future configurations.
ID Schema is a standard JSON schema that defines dataset that can be stored in the Identity repository for a resident. The schema allows the adopters to customize the fields that's needed for running the identity program.
Defining the ID Schema is the first step towards creating a foundational ID system. Once defined, all applications built on top of the MOSIP platform must conform to the same.
One should not confuse ID Schema with what is seen on the screen of the Registration client/ Pre-registration. ID Schema is the final data that you would like to store against each user in the final ID Repository. Quite often we collect more data than listed in ID Schema. This is essential to validate the user's claim. We should consider these data as transactional and it will never reach the final ID Repository.
This guide is intended for adopters who would customize the default ID Schema to suit the needs of a specific deployment.
Field: Unit of data collected from residents (eg. fullName, dateOfBirth, proofOfIdentity etc).
Field attribute: Qualification of Field (e.g.: fieldCategory, fieldType, etc).
Definition: Custom data types are defined for collecting different types of data:
simpleType: Multiple languages.
documentType: Document metadata.
biometricType: Biometric file CBEFF XML metadata
bioAttributes:
leftEye, rightEye, leftIndex, leftRing, leftLittle, leftMiddle, rightIndex, rightRing, rightMiddle, rightLittle, rightThumb, leftThumb, face,
fieldCategory
none: Cannot be used for any purpose. But will be stored in id.json (default subpacket). These are used in exceptional cases when we need to store some data for future reference in case of investigating an ID fraud or if law mandates the storage of such data.
pvt: Private information, can be used in authentication. A limited data that can be used for authentication & kyc.
kyc: Information that can be disclosed to partners either as a credential or through the ekyc API's.
evidence: Field is treated as proof and may be subjected to removal. In certain countries law mandates deletion of such data once the Identity of the user is verified. Marking some of the fields as evidence helps in deleting them without violating the source of truth signatures.
optional: Field is treated as proof and will be removed after a predefined interval (defined as policy).
format
lowercased: Value stored in lower case format
uppercased: Value stored in upper case format
none: No format applied to the data
validators
type: Validation engine type. Supported type as of now is regex.
validator: Based on the type the actual script is placed here. In case the type is regex then the actual regex pattern is used here.
arguments: Array to hold parameter or dependent field IDs required for validation.
subType
For every documentType field, document category code must be the value of this key. This document category code is used to validate the provided document types in the ID object.
Refer to the sample ID Schema. A guide to customising the same is given below.
ID schema is loaded as a part of master data to identity_schema table in mosip_masterdata DB.
If any changes are made to the default ID Schema, make sure the following dependencies are updated as well:
UI Specifications
ID Schema is identified based on it's version in the MOSIP system. On publishing of an ID Schema, the schema is versioned. Every ID Object stores the ID Schema version which is validated during ID Object validation.
The following is the list of good practices that MOSIP recommends for creating your ID Schema.
As a privacy by design practice, it is recommended that the number of fields is kept to a usable minimum in order to avoid profiling.
Larger number of data results in serious data quality issues.
Keeping the fields minimum ensures everyone is inclusively added to the foundational identity.
As a best guide, limit the total number of fields to be less than 10.
Stick to one version of ID Schema for better compatibility.
This guide helps the operator in setting up the registration client.
A Trusted Platform Module (TPM) is a specialized chip on a local machines that stores RSA encryption keys specific to the host system for hardware authentication.The pair is maintained inside the chip and cannot be accessed by software. By leveraging this security feature every individual machine would be uniquely registered and identified by the MOSIP server component with it's TPM public key.
To extract the TPM public key, use the TPM key extractor utility.
To onboard the machine and the operator, the Admin needs to:
Create and activate the registration client machine using Admin portal.
Create a user/operator account in Keycloak
Assign the operator a role of either the Supervisor or Officer using the Admin portal.
Finally, perform the User Zone mapping and User Center mapping in the Admin portal.
System prerequisites:
CPU - Dual Core Processor - 2GHZ
RAM - 16 GB
Local Storage Disk Space - 500 GB
USB 2.0 ports or equivalent hub.
Physical machine with TPM 2.0 facility.
Windows OS [10 v]
To setup the registration client:
Download the reg-client.zip from the hosted server.
Unzip the client. You can see the directory structure below.
Click run.bat to launch registration client.
The client always launches with the pre-loader screen which displays the information about the network status, build status verification, online status, etc.
First time launch
After the pre-loader, the login screen is displayed.
Any valid operator credentials can be provided to authenticate and start the initial sync.
On successful intial sync, the operator will be prompted to restart the application.
After the first launch, the operator can notice .mosipkeys and db folders created under the registration client setup folder.
Note: Deletion of either the .mopsipkeys or the db folder makes the application get into an invalid state and hence will fail to launch. To be able to launch the client again, the operator should make sure that both the folders are removed and then re-launch the client.
On the next launch after the initial sync,
The registration client login page provides the operator an option to select the language for viewing the registration client UI.
After successful login, the operator either lands into the operator onboard page or the home page.
For more details on operator onboarding, refer to Operator onboarding guide.
For more details on Home page, refer to Registration client home page.
Offline- Operator can use the registration client in offline mode to only do the registrations and EOD process. During offline mode, the operator authentication will be based on locally saved password hash. An operator can work in offline mode only if they have logged into to the registration client being online atleast once.
Online- Machine must be online for the registration client first launch. For any server-client sync or vice-versa, the registration client must be online. In the online mode, the client reaches out to the server for password authentication.
Note: On successful onboard of the operator, biometric templates of the operator are stored locally. Biometric authentication does not reach out to the server everytime, instead it is validated based on the locally stored templates on the registration client machine.
In the development environment, Registration client can be tested using mock SBI. Find the instructions to build and run the mock SBI, click here.
1. Incorrect username/password
-> Cross-check the machine keys mapping in server ('Machine not found' error in logs)
-> Cross-check machine status
-> 'Invalid Request' error in log - Check your machine time, it shouldnt be less or greater than local timezone datetime (usually accepted lag is +5/-5 minutes)
-> check logs/registration.log for more details2. Configuration / masterdata Sync failed
-> check if kernel-syncdata-service is up.Default settings schema is configured as below:
[
{
"name":"scheduledjobs",
"description":{
"ara":"إعدادات الوظائف المجدولة",
"fra":"Paramètres des travaux planifiés",
"eng":"Scheduled Jobs Settings"
},
"label":{
"ara":"إعدادات الوظائف المجدولة",
"fra":"Paramètres des travaux planifiés",
"eng":"Scheduled Jobs Settings"
},
"fxml":"ScheduledJobsSettings.fxml",
"icon":"scheduledjobs.png",
"order":"1",
"shortcut-icon":"scheduledjobs-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR"
]
},
{
"name":"globalconfigs",
"description":{
"ara":"إعدادات التكوين العامة",
"fra":"Paramètres de configuration globale",
"eng":"Global Config Settings"
},
"label":{
"ara":"إعدادات التكوين العامة",
"fra":"Paramètres de configuration globale",
"eng":"Global Config Settings"
},
"fxml":"GlobalConfigSettings.fxml",
"icon":"globalconfigs.png",
"order":"2",
"shortcut-icon":"globalconfigs-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR"
]
},
{
"name":"devices",
"description":{
"ara":"إعدادات الجهاز",
"fra":"Réglages de l'appareil",
"eng":"Device Settings"
},
"label":{
"ara":"إعدادات الجهاز",
"fra":"Réglages de l'appareil",
"eng":"Device Settings"
},
"fxml":"DeviceSettings.fxml",
"icon":"devices.png",
"order":"3",
"shortcut-icon":"devices-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR",
"REGISTRATION_OFFICER"
]
}
]Clicking on in the home page opens a pop-up displaying configured Settings page as per the above sample settings schema.
All the connected devices are listed in this page.
Option to scan for SBI for any specific port range is available in this page.
If more than one device is idenitied, operator can choose amongst the listed devices to set the default device for the current login session.
Access control on this page is controlled via the settings-schema.
All the Registration Client related configuration key-value pairs are listed in this page.
Operator can set the local preference on the server configraton value, applicable only for permitted configuration keys.
Access control on this page is controlled via the settings-schema.
All the available background jobs are listed here along with their cron expression.
Every job's next and previous trigger time is listed along with the job name.
Privileged operator can update the cron expression of any job.
Synchornize Data in home page will trigger all of these listed jobs with just one click.
If the operator needs to trigger specific job, the same can be handled in this page.
Access control on this page is controlled via the settings-schema.
UI specs of Pre-Registration module are used to configure the form fields in the Demographic Details and Document Upload functionality. UI specs are saved as a JSON file with a list of fields. Each field has a set of attributes/ properties that can be configured which affects the look and feel along with the functionality of the field. Below is the list of all the properties available for each field in the UI specs:
OTP Request Service is used by Authentication/e-KYC Partners to generate OTP for an individual's UIN/VID. The generated OTP is stored in IDA DB for validation during OTP Authentication.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in ID Repository Services:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository Services on your local system:
1. Download lombok.jar and settings.xml from .
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the .
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone .
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As ID Authentication is using two properties files, id-authentication-default and application-default, you will have to configure them according to your environment. The same files are available for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri , and hence there is no need of auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-authentication-default.properties
......
......
5. To run the server, two files are required- and .
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with environment - "Auth-Otp-Service-Dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer .
The services mentioned below are used by Authentication/e-KYC Partners.
Authentication service- used to authenticate an individual's UIN/VID using one ore more authentication types.
KYC Authentication service- used to request e-KYC for an individul's UIN/VID using one ore more authentication types.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in ID Repository Services:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository Services on your local system:
1. Download lombok.jar and settings.xml from .
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the .
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone .
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As ID Authentication is using two properties files, id-authentication-default and application-default, you will have to configure them according to your environment. The same files are available for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri , and hence there is no need of auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-authentication-default.properties
......
......
5. To run the server, two files are required- and .
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with environment - "Auth-Service-Dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer .
This guide contains all the details you may want to know about the operator onboarding.
To generate the first operator in MOSIP eco-system, refer to the steps below.
The Admin needs to:
Create the role Default in KeyCloak with all the other roles.
Create the operator' user account in KeyCloak.
Assign the operator user account with the Default role.
Perform Zone and Center mapping for the operator using the Admin Portal.
Onboard the operator machine using the Admin Portal. Machine' details can be extracted using the
The operator will need to:
Download the latest registration client and login with the credentials set in KeyCloak. The operator will automatically skip Operator/Supervisor onboarding and reaches the home page of the registration client.
Register themselves in MOSIP and get a RID and UIN.
Once the operator is registered:
The Admin changes the role of the operator to either REGISTRATION_OFFICER or REGISTRATION_SUPERVISOR.
Deletes the role Default from KeyCloak so that no other user has the role Default.
This operator can now register and onboard other Supervisors and Officers.
Admin needs to map the operator' UIN in KeyCloak under Attributes with attribute name as individualId.
Admin needs to remove the "Default" role mapping for the operator' user account if it exists.
The operator needs to login (password based) to the Registration Client using Keycloak credentials.
The operator needs to ensure that the Registration Client machine is online.
The operator will land into the below page and needs to click on Get Onboarded
The operator needs to provide their biometrics and click Save.
All the biometric modalities displayed in the Operator biometrics page must be captured before clicking on Save.
Captured biometrics quality must be greater than or equal to the threshold displayed in the UI.
Note- The threshold values are configurable and can be set as per the ID issuer.
After successful onboarding, the operator is automatically re-directed to the .
Note:
After successful onboarding of the operator, the templates are extracted from the captured biometrics using configured Bio-SDK. The extracted templates are stored in Derby DB. This can be used later for operator' biometric-authentication and also for local de-duplication checks during registration.
After the first login and successful on-boarding, the registration client would mandate the operator to login with the configured authentication mode decided by the administrator.
Any number of operators can login to a registration client machine but they need to be mapped to the same center where the machine is onboarded.
Login operator' user ID is case-insensitive.
Summarizing, on-boarding of an operator is successful only if,
The operator is active and not block listed.
The operator and the machine belongs to the same center.
The operator's User ID is mapped to their UIN.
The operator's biometric authentication is successful during on-boarding.
The system is online during on-boarding.
Operator logs into Registration Client for the first time and is redirected to Onboarding screen. Here, they need to capture all their biometrics and then click SAVE button.
Request from Registration Client goes to for operator authentication.
Registration Processor passes this request to where it checks whether the user is mapped to a valid UIN and then matches the biometrics sent in the request with the biometrics of the mapped UIN.
Success/Failure response sent back to Registration Processor based on the authentication result.
Registration Processor sends back this response to Registration Client.
After successful authentication, the captured biometrics are sent to configured Bio-SDK to extract templates.
Extracted templates are sent back from .
The extracted templates are stored in local Derby DB.
These templates stored in local DB can be used later for operator's biometric-authentication and also for local de-duplication checks during registration.
MOSIP supports single factor and multi factor login including password, iris, fingerprint, and face authentication for registration client. An administrative configuration setting determines the mode of authentication login.
The registration client can authenticate an operator in offline mode using the locally stored biometrics templates (face/finger/iris) and password hash.
The registration client temporarily locks the operator’s account in case they provides an invalid password/fingerprint/iris/face for X times continuously to login (X is configurable). The temporary account lock lasts for X minutes (X is again configurable).
An Operator can logout of the registration client by:
Clicking on the Logout button,
Closing the registration client,
Being in-active on the registration client for configured amount of time after which they are automatically logged out.
Upon logout, any unsaved data will be lost.
Data will not be automatically saved in the database and will not be retained in memory though transaction details which is used for auditing will be captured and stored (except for PII data).
Note- Registration client provides an alerts to the operator ‘X’ minutes before reaching the auto logout time limit. Registration client displays a countdown timer in the alert. The operator can choose to dismiss the alert and continue working. This will also reset the timer to zero.
Resident Portal is a self-help web-b portal that can be used by the residents of a country to avail of the services related to their Unique Identification Number (UIN). The architecture, interface overview, and key services provided are discussed below:
Architecture
Interface overview
Key Services
UIN services
View My History
Secure My ID
Manage My VID
Track My Request
Download My Personalized Card
Update My Data
Share My Credential
Get Information
Supporting Document
Registration Center
Verify Email ID/Phone number
Get My UIN
Booking an Appointment
Below is a detailed explanation of each of the features along with the list of relevant APIs.
The Resident Portal menu bar contains the following:
Font Size- Residents can alter the size of the font based on their preferences.
Language- Residents can select the language of preference.
Bell icon Notification- Residents can view the notifications of all the asynchronous events in chronological order.
Profile Icon- Residents can view the following:
Name of the logged in user
Photo of the logged in user
Last login details
Logout option
A dashboard view to quickly locate the 'Key Services'
The residents can view the history of all the transactions associated with their logged-in UIN/ AID/ VID. They can also view their details and if any unaccounted entry is found, a report can be raised against the same.
On clicking “Secure My ID”, the residents can view the status of all the authentication types. They can choose to lock or unlock authentication types like the following:
Email OTP authentication
Phone OTP authentication
Demographic authentication
Fingerprint authentication
Iris authentication
Face authentication
Fetch Authentication Types - Lock status of the individual
Applies the Authentication Types Lock/Unlock request in IDA
\
On clicking “Manage My VID”, the resident will be taken to a page where they can view details of the existing VIDs, generate new VID, revoke existing VIDs, or download a VID card.
The following types of VIDs can be seen based on the VID policy:
Perpetual VID
Temporary VID
One-time VID
Fetch Active VIDs of the Individual
Revoke the VID of the Individual
Store the Credential Request ID and a new Event ID
Notify that the VID card is Ready to Download status.
Download PDF Card
On clicking “Track My Requests”, the residents can track the status of an Event ID (EID) associated with the logged-in UIN/ VID. They can also view and download the detailed information about the entered EID.
On clicking “Get Personalized Card”, the residents can select the data to be added to their credential. They can preview the chosen data and download it. Residents should select at least 3 attributes.
Creates the personalized card and signs it
On clicking “Share My Data”, the residents can choose the data to be shared with any of the registered partners to avail various third party services.
Submits the share credential request
Notifies resident about the credential shared status for the event ID
Fetch existing AID in progress
Submits the update request
Notifies that the UIN card is ready to Download status
Notify for IDENTITY_UPDATED for the Event Id
Get the Status for the AID
Validate the Access token and ID token
Fetch Supporting Documents PDF\
Fetch registration centers
\
The residents can use this feature to verify their registered email ID or phone number.
The residents can use this feature for one of the following:
Download their UIN card
Check the status of their Application ID (AID)
Get PDF card for AID if ready
Check if PDF card URL is notified by Digital card service.
Validates the Action token and ID token.
The residents can book an appointment for registration using the pre-registration portal. To do so, they can click on “Book an appointment” tile which will redirect them to the pre-registration portal. To know more about pre-registration portal, refer to this link [ ]
The table below outlines the frameworks, tools, and technologies employed by Resident Portal.
The table below outlines the frameworks, tools, and technologies employed by Resident Services.
id
The id property is the unique id provided to a field to uniquely identify it. The id can be alpha-numeric without any spaces between them.
"id":"zone"
description
This is a non-mandatory property used to describe the field.
"description": "zone"
labelName
This property defines label name for the field. This property has sub-attributes as the language code (eng, fra, ara) to store data in different languages based on the country's configuration.
"labelName": { "eng": "Zone", "ara": "منطقة", "fra": "Zone"}
controlType
This property defines the kind of UI component to be used to capture data in UI. Currently the values that can be used are: • textbox (creates multiple textboxes for each field to capture input in all the languages configured for the setup) • dropdown • fileupload • date (creates a date picker) • ageDate (creates a date picker along with number toggle to provide age directly) • checkbox (creates a toggle checkbox for the field which can be checked or unchecked) • button (creates dropdown options as buttons, which user can select easily)
inputRequired
This property decides if the field is to be displayed in the UI form or not. It is useful for some internal fields which do not need any input from the user.
required
This is a mandatory property which decides if the field is a required form field or not. If true, user must provide some value for the field.
type
This property defines the data type of the value corresponding to this field. The data types supported are “number”, “string” and “simpleType”. The type “simpleType” means that language specific value will be saved along with the language code.
fieldType
This property is relevant when control type is “dropdown” or “button”. It defines if the field is of type “default” or “dynamic”. If it is “dynamic” then all the options for the dropdown are populated from the “master.dynamic_field” table otherwise they are populated from corresponding table example “master.gender”
subType
This is relevant for 2 cases: 1. When control type is “dropdown”/ “button” and the type is “dynamic” then “subtype” can be used to populate the options for the field with the data available in “master.dynamic_field” table. 2. When the control type is “fileupload”, then the property ”subtype” is used to map the field to a “code” in the “master.doc_category” table.
validators
* This property enables us to add the list of language specific validators for the field. * Each validator can have the below fields, “langCode”, “type”, “validator”, “arguments”, “errorMessageCode” * The “type” defines the validation engine type. * The “validator” gives the pattern/ methodName/ scriptName/ expression * The “arguments” array to is used to hold parameter or dependent field ids required for validation * The “errorMessageCode” can be given to add custom error message which will be shown to the user when the validation fails. The error message corresponding to this code will be picked from language specific i18n translation files. In case “errorMessageCode” is not given then generic error message will be displayed to the user when validation fails. Currently, regex is supported by MOSIP. If “langCode” is not added then same “validator” is used for all languages of the field.
"validators": [{ "langCode": "eng", "type": "regex", "validator": "^(?=.{0,50}$).*", "arguments": [], "errorMessageCode": "UI_1000" },{ "langCode": "ara", "type": "regex", "validator": "^[A-Z]+$", "arguments": [] },{ "langCode": "fra", "type": "regex", "validator": "^[A-Z]+$", "arguments": [] }]
transliteration
If enabled, then value entered by user in one language is transliterated into other.
locationHierarchyLevel
This attribute is mandatory for the location dropdown fields. The value will be as per corresponding location hierarchy level from the master.loc_hierarchy_list table.
{ "id":"region", "controlType":"dropdown", "fieldType":"default", "type":"simpleType", "parentLocCode":"MOR", "locationHierarchyLevel":1 ..}
parentLocCode
This attribute is to be used only for location dropdown fields and it is optional. The corresponding location dropdown will be pre populated in UI based on the value in “parentLocCode”. If this attribute is NOT mentioned in UI specs, then the dropdown will be populated based on selection in its parent dropdown, as before. For the first dropdown, in case this attribute is not mentioned in UI specs then the value from “mosip.country.code” configuration will be used for backward compatibility.
{ "id":"region", "controlType":"dropdown", "fieldType":"default", "type":"simpleType", "parentLocCode":"MOR", "locationHierarchyLevel":1 ..}
visibleCondition
The property is used to define an expression using json-rules-engine which will decide the visibility condition for the form field. Refer https://www.npmjs.com/package/json-rules-engine to get the syntax for the conditions.
"visibleCondition": { "all": [{ "fact": "identity", "operator":"lessThanInclusive", "value": 10, "path": "$.age" }]} This condition will make the field visible only when the “age” field value <= 10.
requiredCondition
The property is used to define an expression using json-rules-engine which will decide the required condition for the form field. Refer https://www.npmjs.com/package/json-rules-engine to get the syntax for the conditions.
"requiredCondition": { "all": [{ "fact": "identity", "operator": "equal", "value": "MLE", "path": "$.gender.0.value" },{ "fact": "identity", "operator": "equal", "value": "102", "path": "$.maritalStatus.0.value" }]} This condition will make the field required only when the “gender” field value = ‘MLE’ and “maritalStatus” field value is 102” .
alignmentGroup
* This property is used to group the fields on the screen. * If it is skipped, then all the fields will appear in same sequence (horizontally layout) as they appear in UI specs. * If you want the first and fifth field to be in same row in the screen, you can add this attribute with same group name. * The UI is responsive so it will accommodate as many fields in one row as they will fit comfortably.
containerStyle
This is used to optionally apply some CSS styles to the UI field container.
"containerStyle": { "width": "600px", "margin-right": "10px" }
headerStyle
This is used to optionally apply some CSS styles to the UI header of the field container.
"headerStyle": { "width": "600px", "margin-right": "10px" }
changeAction
This property can be added to define interaction between the 2 or more form fields when user changes value in one of them. Currently the “changeAction” supported are “copy&disable” and “copyto” ONLY.
1. "changeAction": "copyto:permanentZipcode, presentZipcode,addressCopy" When the checkbox “addressCopy” is checked the value of the field “permanentZipcode” will be copied to “presentZipcode”. 2. "changeAction":"copy&disable: permanentCountry=presentCountry, permanentAddressLine1=presentAddressLine1" When the checkbox “addressCopy” is checked the value of the field “permanentCountry” will be copied to “presentCountry” and the field “presentCountry” will be disabled. Same with “permanentAddressLine1” and “presentAddressLine1”.
7.2.1
AngularJS is a toolset for building the framework most suited to your application development. It is fully extensible and works well with other libraries.
16.2.0
Node.js is a JavaScript runtime built on Chrome's V8 JavaScript engine.
Java SE 11
OpenJDK 11
Language Runtime in Docker Image
GNU General Public License, version 2, with the Classpath Exception
Ubuntu Server
20.04
Docker base image Operating System
Free
Spring
5
Application Framework
Apache License 2.0
Apache commons
Version compatible with Spring 5
Utilities
Apache License 2.0
Hibernate
5.2.17.Final
ORM
Apache Software License 2.0
Hibernate validator
6.0.12.Final
validator
Apache Software License 2.0
mvel2
2.4.7.Final
Expression language
Apache License 2.0
Jackson
2.9.x
JSON marshal/unmarshal
Apache Software License 2.0
Junit
4.x and above
Unit Testing
Common Public License - v 1.0
mockito
2.22.0
Junit - Mock Objects
MIT
power-mock
2.0.7
Junit - Mock Static Classes
Apache Software License 2.0
logback
1.2.3
Log
GNU Lesser GPL Version 2.1
velocity
1.7
Templating
Apache Software License 2.0
Swagger
Open API - 3
API Documentation
Apache Software License 2.0
Tomcat server
8
Application Server
Apache Software License 2.0
PostgreSQL
Server: 10
Database
Postgres License BSD 2-clause "Simplified License"
Sonar
7.2
Code quality Checking
Open Source License
Micrometer Prometheus
1.4.2
Metrics
Apache Software License 2.0
gson
2.8.4
JSON parser
Apache Software License 2.0
h2 database
1.4.197
JUnit Test DB
EPL 1.0, MPL 2.0
lombok
1.18.8
Development - reduce the boilerplate code
MIT
IText PDF
5.5.13.3
PDF Generation
AGPL 3.0
icu4j
63.1
Transliteration
Unicode-3.0
























The right to privacy is a fundamental right in many contexts. Privacy protection or preservation can be ensured in an application by adopting a privacy friendly design stance.
Privacy takes many forms. From an identity system perspective, the confidentiality of identity information and anonymity when using the identity offers privacy.
MOSIP views the identity system as a custodian of the individual's data. This data has to be protected in order to protect the individual from privacy and security risks. Privacy protection measures include data protection, transparency, user control, confidentiality, selective disclosure, user anonymity and intrusion protection.
MOSIP addresses privacy design at four levels.
Functional Privacy ensures the system is designed to process and expose only the data necessary for a specific function. It embodies data minimization and protects individuals from unnecessary data collection and exposure.
By embedding this principle, MOSIP achieves:
📉 Minimal data exposure across system components
🔒 Robust protection against unauthorized access and misuse
🛡️ Compliance with privacy principles like data minimization and purpose limitation
🌐 Alignment with standards and specifications. (refer here to know more about the standards and specification)
MOSIP achieves Functional Privacy through the following key mechanisms:
Selective Disclosure
What it is -Selective disclosure is the principle of limiting the data shared with different system components or relying parties to only what they strictly require.
Purpose -To prevent over-sharing of personal data across services and ensure privacy at every step of the identity lifecycle.
How MOSIP implements it -MOSIP’s modular architecture ensures that different modules (e.g., Registration, ID Authentication) only access and process the subset of identity data they need for their specific tasks. For example:
The Registration Client only collects demographic and biometric data required for enrolment.
Authentication services only verify the attributes requested by the relying party without exposing the full identity.
Anonymization
What it is -Anonymization removes or masks personal identifiers to make it impossible to link data back to an individual.
Purpose -To ensure privacy in scenarios like analytics, system monitoring, and reporting where identification isn’t necessary.
How MOSIP implements it -Audit logs and analytics data in MOSIP are anonymized by stripping or pseudonymizing personally identifiable information (PII), ensuring privacy even in post-processing environments.
Need to Know
What it is -This principle limits access to personal data only to the individuals, modules, or systems that require it for their roles.
Purpose -To reduce the risk of unauthorized access and exposure of sensitive information.
How MOSIP implements it -MOSIP enforces Role-Based Access Control (RBAC) and fine-grained permissions across modules. For example:
Biometric data is accessible only to the modules responsible for deduplication and authentication.
Administrative users can only view logs relevant to their operational scope.
Encryption
What it is -Encryption secures sensitive data by converting it into an unreadable format accessible only with the right cryptographic keys.
Purpose -To safeguard sensitive identity data from unauthorized access, breaches, or interception during storage and transmission.
How MOSIP implements it
MOSIP uses encryption algorithms such as: RSA,Elliptic Curve Cryptography (EC),JSON Web Encryption (JWE)
Secure key management is enforced through Hardware Security Modules (HSMs) for cryptographic key storage and usage.
Tokenization
What it is -Tokenization substitutes sensitive data elements with randomly generated tokens to reduce direct exposure of real identifiers during system operations.
Purpose -To protect sensitive identifiers like UINs during processing and interaction between modules.
How MOSIP implements it -In MOSIP, sensitive identifiers (such as UIN) are tokenized during authentication or API interactions to ensure the original identifiers are not exposed to external systems.
Security is a foundational principle ensuring the protection of the system, user data, and transactions from unauthorized access, breaches, and malicious attacks.
By embedding strong security practices, MOSIP achieves:
🔒 Protection of sensitive identity data from external and internal threats
🧑💻 Resilience against cyberattacks and unauthorized system usage
🌐 Trust and confidence for governments, system integrators, and end-users
🛠️ Compliance with global security standards and frameworks
This robust security framework enables MOSIP to function as a reliable backbone for national ID systems deployed worldwide.
MOSIP implements its security framework through the following key sub-elements:
Data Security
What it is -Data security ensures that all data handled by MOSIP—whether in storage or while processing—is safeguarded against unauthorized access, tampering, or breaches.
Purpose -To prevent data leaks, ensure confidentiality and integrity, and protect user identities throughout their lifecycle.
How MOSIP implements it -MOSIP adopts a multi-layered security approach to protect sensitive data:
Encryption & Decryption – Encryption is achieved using algorithms such as RSA, EC, and JWE.
Hashing – Sensitive elements like biometric templates are hashed with secure algorithms.
HSM-backed Key Management – Cryptographic keys are securely managed using Hardware Security Modules.
Database Security – Role-based permissions and audit trails monitor access. refer this link to know more about how MOSIP Identity Platform supports data security
Trusted Applications
What it is -Trusted applications refer to MOSIP’s mechanism to ensure that only verified and authorized software can interact with core modules and services.
Purpose -To prevent unverified, potentially malicious applications from accessing sensitive APIs or data within MOSIP.
How MOSIP implements it -MOSIP uses several mechanisms to ensure only authorized applications interact with the identity system:
API Key Management – Each external application accessing MOSIP APIs is registered and issued secure API keys.
Digital Certificates – Mutual TLS (mTLS) ensures both MOSIP and external applications verify each other’s identity.
Sandbox Environments – Applications are tested and validated in a sandbox before production deployment.
Access Control
What it is -Access control manages who can view, modify, or use specific data and system functions within MOSIP.
Purpose -To ensure that only authorized personnel and system components can access sensitive data or perform privileged operations.
How MOSIP implements it -MOSIP enforces strict access policies through:
Role-Based Access Control (RBAC) – Defines roles (e.g., admin, registrar, operator) with precise permissions.
Principle of Least Privilege – Grants users/modules only the minimum access necessary for their tasks.
Audit Trails – Tracks and logs all access attempts and changes for monitoring and compliance.
Multi-Factor Authentication (MFA) – Adds an additional layer of protection for administrative access.
User Centricity means putting individuals at the heart of the identity system. It ensures that users are empowered to control their data, understand how it’s used, and interact with the system in ways that are inclusive, usable, and respectful of their privacy.
By adopting user-centric principles, MOSIP achieves:
👤 Empowerment of individuals over their personal data
✅ Transparency and informed decision-making through consent
🌍 Inclusivity for diverse populations, including the marginalized
📱 Usability to support users with varying levels of digital literacy
This approach ensures MOSIP supports privacy rights and accessibility for all users, making identity systems fair and equitable.
MOSIP integrates User Centricity through the following sub-elements:
User Control
What it is -User Control means enabling individuals to manage how their identity data is collected, used, and shared within the system.
Purpose -To empower users with autonomy over their data, preventing misuse or overreach by third parties.
How MOSIP implements it
Users can update certain attributes through designated update mechanisms. For example, if a user wishes to update their address, they can log in to the resident portal and make the change directly. If they require assistance, they may visit a registration center, where an operator will update the address on their behalf. Once the update is successful, the new information will be reflected in the user’s records.
Authentication requests disclose what data is being accessed, giving users the choice to proceed or decline.
Consent
What it is -Consent is the process of obtaining explicit and informed agreement from individuals before accessing or using their personal data.
Purpose -To respect individual privacy rights and comply with global data protection regulations.
How MOSIP implements it -MOSIP integrates consent mechanisms at multiple stages:
During registration – Presents clear information about data usage and requires explicit consent before proceeding.
During authentication – Displays prompts specifying which identity attributes are being requested.
User decision – Individuals can approve or deny data-sharing requests before information is transmitted.
Auditing – Consent actions are securely recorded for transparency and accountability.
Usability
What it is -Usability ensures the system is designed to be simple, intuitive, and accessible to people of varying education levels and digital literacy.
Purpose -To make MOSIP approachable and effective for all users, including those unfamiliar with technology.
How MOSIP implements it
Multilingual support in registration and authentication modules.
Simple, clear UI/UX design in client applications.
Offline capabilities for areas with low connectivity.
Assisted user journeys for vulnerable individuals.
Incorporation of GenderMag principles to evaluate and improve usability across diverse cognitive styles and gender-inclusive perspectives
Inclusion
What it is -Inclusion ensures that the identity system accommodates all segments of society, including marginalized groups, persons with disabilities, and those in remote areas.
Purpose -To prevent exclusion and ensure equitable access to identity for every individual.
How MOSIP implements it
Supports biometric exceptions for individuals unable to provide fingerprints.
Allows demographic-only registration when biometrics cannot be captured.
Provides accessibility features for people with disabilities.
Designed for multilingual, multi-cultural, and resource-constrained environments.
You can refer to this link to know more about how MOSIP Identity Platform supports inclusivity
Transparency ensures that all stakeholders—governments, system integrators, and end users—have clear visibility into how the system works, how decisions are made, and how data is handled.
By embedding transparency into its architecture and processes, MOSIP achieves:
🏛️ Trust through openness and accountability
📜 Verifiability of system behavior and outputs
👥 Governance structures that ensure fair and ethical use of the platform
This fosters confidence in MOSIP as a public good and aligns it with international best practices for open and transparent digital systems.
MOSIP enables Transparency through the following sub-elements:
Openness
What it is -Openness means making MOSIP’s design, codebase, and operational principles publicly accessible to encourage trust, collaboration, and innovation.
Purpose -To promote community participation, allow peer review, and ensure the platform evolves securely and inclusively.
How MOSIP implements it
Open-source architecture – Entire codebase is published under an open-source license on GitHub.
Open APIs and standards – API documentation and integration standards are freely available.
Community engagement – Feedback and contributions from global experts are encouraged.
Verifiability
What it is -Verifiability ensures that the system’s actions and outputs can be independently audited for correctness and compliance.
Purpose -To build stakeholder confidence that the system operates as intended without hidden processes or biases.
How MOSIP implements it
Audit trails – All critical system actions are logged for compliance and monitoring.
Deterministic algorithms – Processes yield consistent, predictable results for identical inputs.
Third-party assessments – Encourages independent audits of MOSIP deployments.
Governance
What it is -Governance refers to the frameworks and policies defining how MOSIP is managed, maintained, and deployed responsibly.
Purpose -To ensure fair, ethical, and lawful operation of MOSIP-based identity systems, protecting individuals’ rights.
How MOSIP implements it
Strong governance model – Managed by IIIT-Bangalore for independence and neutrality.
Advisory boards – Include global experts guiding MOSIP’s evolution.
Policy frameworks – Guidance for governments on privacy, security, and ethical deployment.
These design principles have resulted in features as well as development practices in MOSIP that enhance privacy protection. A typical example for a practice is how PII (Personally Identifiable Information) is dealt with when creating application or audit logs. An example of a feature is how our Datashare policies allow selective sharing of information.
Android Registration Client provides several essential features designed to enhance user convenience and system efficiency.
It facilitates seamless user registration by offering an intuitive interface that supports quick data entry and ensures rigorous data validation to minimize errors.
Read through to know more about the key features of Android Registration:
Operators can securely login using their credentials, whether in offline or online mode, to carry out various registration transactions. To enable offline login, the operator must have previously logged in and synchronized their data over a network.
The Android Registration Client supports multiple languages for content display and data entry.
Display Language Display Language refers to the language used for rendering UI elements such as labels and headings. With the Android Registration Client, Operators have the option to choose their preferred language for UI display. This language selection can be made on the login screen. Currently, the supported display languages include Arabic, French, and English.
New languages can be added by following the below steps:
Additional languages can be configured by adding localization files in the lib/l10n folder present in the root project directory("android_registration_client").
The languages that are rendered on the UI will be based on the country configuration (after master data sync). The default display language is English. Other languages will be available in the UI after the master data sync.
To know more, refer to Flutter doc-Internationalizing Flutter apps.
Data Entry Language: The Data Entry Language refers to the specific language utilized by the Operator while gathering data, which is then stored on the server in that selected language. During the registration process, the Operator can choose the language preference for the data collected, allowing applicants to provide information in their desired language. This language selection option becomes available upon initiating a new registration. The responsibility for managing the data entry language lies within the UI Spec, and any modifications or changes can be made through that specification.
On launching the Android Registration Client and logging in for the first time, the system automatically syncs the following data:
Configuration sync: Sync of properties which drives in deciding the ARC UI functionality. For example: Invalid login attempts, idle timeout, thresholds, etc.
Masterdata sync: As a part of this sync, supporting information like Dynamic field data, templates, locations, screen authorization, blocklisted words, etc. are pulled in.
UserDetails sync: userID, along with their status is synced. Only the user details belonging to machine mapped center will be synced.
Certificate sync: Certificates used to validate the server signatures, device CA certificates, and public key (specific to a center and machine, also called policy key) used to encrypt the registration packet will be synced.
Operators can register a resident using the New Registration feature. The registration process can be customized through the Android Registration Client UI specification. The required data for registering an applicant are as follows:
Consent: Before the registration process, applicants must provide consent to the terms and conditions presented on the consent screen. This explicitly asks the applicant to grant permission for storing and using their Personally Identifiable Information (PII).
Demographic Details: Once the consent is obtained, the Operator will enter the demographic data of the applicant in the language preferred by the applicant. This includes details such as their name, gender, date of birth, and residential address.
Documents Upload: Following the completion of the demographic details, the Operator can select the document type, input the reference, and upload the supporting documents provided by the applicant. Supporting documents may include Proof of Address, Proof of Identity, and Proof of Birth, based on the country-specific requirements.
Biometrics: After the documents have been uploaded, the Operator will proceed to capture the applicant's biometrics. The biometrics captured are as follows:
- Fingerprints
- Iris
- Photograph
- Exception photographThe acquisition of biometric data is regulated by the country. The country has control over the capture of each type of biometric (fingerprint, iris, or face) through the global configuration. When the Operator selects the Capture button, the biometric SBI application is accessed to capture the biometrics.
Once the biometrics are obtained, the data and control are returned to the Android Registration Client. To obtain the resident's biometrics, the quality of the captured image must exceed the threshold specified by the country. The biometrics can be captured a set number of times if necessary to meet the quality threshold. In situations where none of the captured images meet the threshold, the image with the highest quality score will be saved.
If the resident has a biometric exception (such as a missing finger/eye or very poor finger/iris quality), the Operator can designate that particular biometric as an exception. However, the Operator must still capture the resident's exception photo.
Biometrics exceptions: If the resident has a biometric exception (such as a missing finger/eye or very poor finger/iris quality), the Operator can designate that particular biometric as an exception. However, the Operator must still capture the resident's exception photo.
Preview section: The Operator can review the data entered by the applicant, including demographic information, uploaded documents, and captured biometrics. This preview allows the Operator to ensure the accuracy of the entered data. If any mistakes are found, the Operator can easily go back to the corresponding section and make the necessary corrections. If the data is correct, the Operator can proceed to the next step, which is to authenticate themselves.
Operator authentication: Once both the Operator and applicant have confirmed that the data is accurately filled, the Operator is required to authenticate themselves using their credentials. After a successful authentication, the data packets are created and only then the sync and upload operations can be performed.
Acknowledgment section: Following the completion of the new registration process, an acknowledgment receipt is generated. This receipt includes the AID(Application ID), captured demographic data in the selected language, a photograph of the resident, and a ranking of each finger from 1 to 10, with 1 representing the finger with the best quality. The receipt is designed to be easily printed.
Packet sync and upload: After the applicant's registration form has been completed and the Operator has authenticated themselves, a packet sync must be performed. This can be done either manually or as a background job(auto sync and upload of packets). Packet sync ensures that the packet is prepared for uploading and the status of the uploaded packet is synchronized with the server. Once the packet sync is completed, the system will proceed to upload the packet to the server when an internet connection is available. If there is no network access, the system will attempt to upload the packet as soon as connectivity is established.
To log in to the Android Registration Client, the operator must complete the onboarding process. This functionality is available only during the first online login. The operator must onboard by capturing their fingerprints, thumbprints, iris, and face. Once these are captured, the operator can start registering residents and using other services.
The Operator can access the dashboard where he can view the following:
Packets created: This will show the total number of packets created from the time the Android Registration Client was installed.
Packets Synced: This will show the total number of packets synced from the time the Android Registration Client was installed.
Packets Uploaded: This will show the total number of packets uploaded from the time the Android Registration Client was installed.
User details:
User ID: This will show the list of User IDs of the Users mapped to the device.
Username: This will show the list of usernames of the Users mapped to the device.
Status: This will show the status of Users mapped to the device. This can take values such as onboarded, active, inactive, etc.
Once the packet is created by the Operator, as an additional check, the Supervisor will have to go through each application to make sure the details filled are coherent. At this stage, the Supervisor can either Approve the Application or he can Reject it. If the Supervisor decides to reject it, they also will have to mandatorily mention the reason for rejection. Once the Application has been Approved or Rejected, the Supervisor will have to authenticate himself by entering his Username and Password. Once they have successfully authenticated, the Application will be removed from the “Supervisor’s Approval” section and will be moved to the “Manage Application” Section.
Once the Application is either Approved or Rejected by the Supervisor, those packets can be uploaded to the server from the “Manage Application” section. If there is internet connectivity, the packet will be synced and uploaded to the server but in case of lack of internet connectivity, the User can also export the packet to their local device storage.
In a scenario where the Resident wants to update their data, they can do so by letting the Operator know their UIN and the data that needs to be updated. Residents can update their demographic details, documents, and biometrics using this feature.
Using this feature, once the user is done with their registration and other activities, they can logout. If no background tasks are running, the user will be immediately logged out. If there are tasks (like sync) running in the background, the user will be notified about the same. From here if the User wants to cancel the logout, the background activities will keep running whereas if the user chooses to logout, they will be logged out and the background activities will be terminated.
In a scenario where the operator wants to update his biometric section from operational tasks to update.
The Handles Feature is designed to streamline citizen registration and authentication. During registration, specific attributes such as email or national ID can be designated as a handle. This handle serves as a unique identifier that can later be used for authentication for various services. Handles can also be used to update data in case of data discrepancies. By allowing flexible and secure identification, the feature enhances the accuracy and integrity of citizen records while simplifying user interactions with government systems-
In a scenario where the Resident has forgotten their UIN, the Operator can use the “Retrieve Lost UIN” option to initiate a request by capturing the resident’s consent, optional demographic details, and mandatory biometrics. After verifying the data in the preview screen and authenticating themselves, the Operator can generate and upload the packet to the server, following which an acknowledgment receipt with the new Application ID (AID) will be shown.
This feature allows Operators to scan a resident’s pre-registration AID QR code to auto-fill their demographic and document data during a new registration. After logging in and selecting “New Registration", the Operator chooses display and notification languages, captures consent, and proceeds to the demographic page. From here, they can scan the AID QR code or enter it manually. If the AID is valid, the system fetches the pre-filled demographic and document data. The Operator can then proceed to capture biometrics and complete registration. This works whether or not the pre-registration was done for the same center and zone, using on-demand fetch if needed. Alternate flows include continuing without scanning or by manually entering the AID.
This feature allows Operators and Supervisors to reset their password using the “Reset Password” option available in the Profile section. On clicking the option, users are redirected to the Keycloak login page (this link is configurable) where they can update their password. After resetting the password, users can return to the ARC login page and sign in with the new password.
If a Supervisor or Operator forgets their password, they can use the "Forgot Password" option available on the login screen. After entering their username, users will be redirected to the Keycloak login page (configurable link) where they can click the "Forgot Password" link. This triggers an email to the registered email ID with instructions to reset the password. Once the password is updated, users can return to the ARC login page and log in using their new password.
The Auto Logout feature enhances application security by automatically logging out users after a defined period of inactivity. The system monitors user activity, and when inactivity exceeds a configurable threshold, a warning message appears with a countdown timer. Users can choose to stay logged in or log out immediately. If the user remains inactive during the warning period, the application automatically logs them out and securely clears all authentication states and session data.
This feature enables the Operator to automatically capture GPS location (latitude and longitude) when creating any packet through Android Registration Client. The GPS location is captured at the point of packet creation and attached as metadata to the packet, ensuring that the Operator's location is tracked for audit and verification purposes. If the device's location services are disabled or GPS is unavailable, the system will log a warning but will not block packet creation.
The Biometric Correction feature enables operators to update and correct the biometric information of applicants, ensuring accurate association with their Unique Identification Number (UIN). When a resident's biometric data does not meet the required threshold during the registration process, the system generates an Additional Info Request ID. This ID is sent to the resident via notification, allowing them to schedule an appointment and update their biometric information at a registration centre.
The Manage Scheduled Jobs feature allows admin and supervisor users to view, manage, and trigger scheduled sync/batch jobs directly from the Scheduled Jobs Settings screen. This feature provides visibility into system jobs (e.g., syncs, cleanup, updates) and enables supervisors to modify their scheduling configuration (cron expressions) on the local device. Each job entry displays the Job Name, Next Run Time, Last Run Time, Cron Expression (editable), and a Manual Trigger Button (Run Now).
This feature enables authorized users (Supervisors) to view and manage global configurations in a single Global Config Settings screen. The feature displays server values fetched from masterdata and allows supervisors to override these values locally on the device. Local configuration changes apply only to the current device and do not affect server-side configurations or other devices. Supervisors can edit Local Values for permitted configuration keys and submit changes, which will automatically restart the app to apply the updates.
This feature enables authorized users (Supervisors and Officers) to view and monitor all devices/peripherals connected to the Android Registration Client tablet. On opening the Device Settings page, the system will automatically scan for connected devices and display device information including device name, device ID, and connection status. If no devices are detected, users can click on the "Scan Now" button to manually trigger a device scan.
The Android Registration Client now fully supports landscape orientation across key screens and workflows. This enhancement ensures a seamless and responsive experience when devices are used horizontally particularly useful for tablets, rugged field devices, and setups where landscape mode improves visibility, usability, or ergonomics. UI components dynamically adjust to maintain clarity, readability, and smooth navigation, offering operators greater flexibility in diverse registration environments.
We’ve optimised the Android Registration Client for smaller screens to ensure a clean, intuitive, and efficient experience on mobile phones. Layouts, forms, and action buttons are now adaptive, automatically adjusting to the constraints of smaller displays without compromising functionality. This enhancement enables field officers and mobile registration teams to operate the client comfortably on compact devices, ensuring consistent performance across a wider range of Android form factors.
Identity Service stores, updates, retrieves identity information.
Also, retrieves and updates UIN status.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in ID Repository Services (Identity Service) setup:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository- Identity Services on your local system:
1. Download lombok.jar and settings.xml from here.
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available here with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone mosip-config repository.
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As Id Repository is using two properties files, id-repository-default and application-default, you will have to configure them according to your environment. The same files are available here for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri , and hence there is no need of auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-repository-default.properties
mosip.idrepo.db.url
mosip.idrepo.db.port
Comment out all the lines containing mosip.biometric.sdk.providers.finger, mosip.biometric.sdk.providers.face and mosip.biometric.sdk.providers.iris.
Comment out this property mosip.kernel.idobjectvalidator.referenceValidator.
mosip.idrepo.mosip-config-url=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
5. To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with environment - "Identity-Service-dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer here.
The APIs can be tested with the help of Swagger-UI.
Swagger is an interface description language for describing restful APIs expressed using JSON. You can access Swagger-UI of identity-services for localhost from http://localhost:8090/idrepository/v1/identity/swagger-ui/index.html?configUrl=/idrepository/v1/identity/v3/api-docs/swagger-config#/.
Welcome to the Registration Client Guide tailored specifically for our Collab Environment!
The Registration Client setup guide for the MOSIP Collab environment offers a detailed and user-friendly walk-through to assist you in configuring and accessing the Registration Client module. This module is specifically designed to provide Operators/Supervisors with a wide range of functionalities, including onboarding, data synchronization, packet management, and more.
The primary goal of this guide is to ensure that you can efficiently set up the Registration Client in the MOSIP Collab environment with minimal effort. Whether you are new to the module and just starting to explore its features or an experienced operator seeking a streamlined setup process, this document will guide you through the essential steps to ensure that you have all the necessary tools available at your disposal.
With the implementation of this Registration Client Demo Setup, you are now on track to demonstrate the remarkable capabilities of MOSIP's Registration system. Let us proceed with the next steps to commence the process.
Workstation
Windows 10/11 laptop or desktop
Minimum 16 GB RAM
50 GB of free space on the hard disk
The workstation should be TPM 2.0 enabled. To access the guidelines on how to verify the TPM compatibility of your workstation, click here.
Wireguard access
JAVA - Ensure JAVA 11 is installed and JAVA_HOME is in the PATH. To download JAVA 11 in your system, click here.
Download the JDK installer
Access the Java SE Downloads page and click Accept License Agreement. Under the Download menu, click the download link that corresponds to .exe the version of Windows 10.
Download the file jdk-11.interim.update.patch_windows-x64_bin.exe.
Run the JDK installer
You must have administrator privilege to install the JDK on Microsoft Windows.
To run the JDK installer, start the JDK 11 installer by double-clicking the installer's icon or file name in the download location.
Follow the instructions provided by the installer.
After the installation is complete, delete the downloaded file to recover the disk space.
Download and run the TPM Utility
This is used for registering the workstation on which the Registration Client would be executed.
To access and set up the utility, click here.
Steps to download and extract the TPM utility
Open the README.txt file for supporting information.
Download and extract the TPM utility (using the command prompt).
Run the following command from the folder where the TPM jar is located (The location of the folder is necessary while running the command) - java -jar tpmutility-0.0.2.jar > tpmdetails.txt
Make note of the details within tpmdetails.txt for the next step.
Share TPM Details
Once the TPM utility is extracted and run in your system, fill out the details in this form here to get your machine registered with MOSIP.
Make sure you share tpmdetails.txt with us according to the form fields.
Once the details are received, we at MOSIP, will register your machine for usage of Registration Client in the Collab environment.
Credentials and WireGuard: Once the TPM request is received via the form, and your machine is registered with us, we will provide you with the necessary credentials to access the Registration Client. Along with these credentials, you will also need to receive access to WireGuard. The details will be shared via the email ID provided in the form.
Mock MDS: Click here to download the Mock MDS in your system folder, which will enable you to simulate biometric capture (without real biometric devices).
Download the Mock MDS zip provided here.
Click on the folder where the Mock MDS is downloaded and double-click on the folder name mock.
You will be able to see the run.bat file in the mock folder.
Double-click on run.bat and extract the file in your system where you can name the folder Collab-mock-mds-reg.
Click on the Collab-mock-mds-reg folder where you will find the sub-folder called Target and then you can click on the Target folder to find the required files to run in the system to activate mock mds.
You can click and explore collab-mock-mds-reg › target › Profile › Default › Registration to see the demo biometrics already updated for finger, iris, and face which will be used while testing the Registration Client, so you won’t be required to do any additional work here.
Click on run_reg.bat to run the mock MDS for the Registration Client.
To effectively experience the Registration Client features in the Collab environment, follow the steps given below:
Step 1: Access the Registration Client Portal
Visit the following URL to access the Registration Client portal in the Collab environment: Registration Client Portal
Click on Registration Client- Windows 10 and download it to your local system.
step 2: Activitating Wireguard.
Launch the wireguard and connect to the provided configuration to enable a secure VPN connection.
Step 3: Login
After completing the above prerequisites, you should receive the username and password you need to log in to the portal.
Step 4: Explore the features on the Registration Client Portal
To start running the Registration Client, refer to our Registration Client Installation Guide.
To access all the features of the Registration Client portal and explore the registration process in MOSIP, refer Registration Client User Guide.
If you require any assistance or encounter any issues during the testing and integration process, kindly reach out to us through the support mechanism provided below.
Navigate to Community.
Provide a detailed description of the support you require or provide detailed information about the issue you have encountered, including steps to reproduce, error messages, logs, and any other relevant details.
Thank you. Wishing you a pleasant experience!
This service creates request for credential issuance.
Keymanager encrypts/decrypts data.
Auth Adapter integrates with Keycloak for authentication.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in ID Repository (Credential Request Generator Service) setup:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository Services on your local system:
1. Download lombok.jar and settings.xml from here.
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available here with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone mosip-config repository.
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As ID Repository is using two properties files, id-repository-default and application-default, you will have to configure them according to your environment. The same files are available here for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri , and hence there is no need of auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-repository-default.properties
mosip.credential.service.database.hostname
mosip.credential.service.database.port
5. To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=/home/vipul/Desktop/tspl/mosip-config/sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with environment - "Credential-request-generator-dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer here.
The APIs can be tested with the help of Swagger-UI.
Swagger is an interface description language for describing restful APIs expressed using JSON. You can access Swagger-UI of credential-request-generator-services for localhost from https://localhost:8094/v1/credentialrequest/swagger-ui/index.html?configUrl=/v1/credentialrequest/v3/api-docs/swagger-config#/.
Internal Authentication Service: The authentication service used by internal MOSIP modules such as Resident Service, Registration Processor, and Registration Client to authenticate individuals.
Internal OTP Service: used by Resident Service to generate an OTP for an Individual for performing OTP Authentication.
Authentication Transaction History Service: used by Resident Service to retrieve a paginated list of authentication and OTP Request transactions for an individual.
The documentation here will guide you through the prerequisites required for the developer's setup.
Below is a list of tools required in ID Repository Services:
JDK 11
Any IDE (like Eclipse or IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository Services on your local system:
1. Download lombok.jar and settings.xml from here.
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file, wait for some time until it completes the scan for the Eclipse IDE, and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately, as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open the command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successfully importing of project, update the project by right-clicking on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available here with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to the project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone mosip-config repository.
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As ID Authentication is using two property files, id-authentication-default and application-default, you will have to configure them according to your environment. The same files are available here for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri, and hence there is no need for auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-authentication-default.properties
......
......
5. To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with the environment - "Auth-Internal-Service-Dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer here.
Pre-registration offers a comprehensive suite of capabilities that simplify and optimize the identity registration journey. By enabling residents to complete few essential steps online—such as entering demographic details and uploading documents to initiate pre-registration—the module reduces wait times and improves data accuracy. Integrated verification mechanisms and secure data handling ensure both user convenience and system integrity. These set of features collectively address challenges like manual data entry, appointment scheduling bottlenecks, and fragmented communication, resulting in a streamlined, secure, and user-friendly onboarding process for residents.
Residents can access the Pre-registration portal using login methods based on email or mobile number, ensuring flexibility and convenience for application creation.
Login allows residents to securely log in and initiate pre-registration for identity issuance using email or mobile number.
Multi-channel Registration: Create accounts using email or mobile number.
OTP-based Verification: Secure account verification via OTP sent to email or SMS, with retry options.
CAPTCHA Security: Prevents automated bot registrations.
Pre-registration enables residents to initiate identity applications online by entering details, uploading documents, and booking appointments before visiting registration centers.
User Consent Management: Explicit consent for data processing and acceptance of terms.
Session Management: Secure sessions with configurable timeout.
Easy Application Creation: The resident can navigate to the application creation page, enters the required details, reviews the information for accuracy, and submits the application.
Document Upload: Upload supporting documents (e.g., Proof of Address, Birth Certificate).
Pre-registration ID Generation: Each application is assigned a unique Application ID (AID), formerly known as PRID (Pre Registration ID), for secure tracking and reference.
Multiple Applicant Support: Register multiple family members or individuals in a single session.
Add Applicant Functionality: Easily add new applicants during the registration process.
Manage and track pre-registration applications with a user-friendly dashboard, status indicators, and lifecycle controls.
Application Status Management Efficiently manage and track the status of pre-registration applications throughout their lifecycle. The system tracks each application's progress through distinct status.
Incomplete: Only demographic details are filled.
Action Required: Upload documents and book an appointment.
Pending Appointment: Demographic details and documents are completed.
Action Required: Book an appointment.
Booked: Application is complete with a scheduled appointment.
Action Required: Visit the registration center on the appointment date and time.
Expired: Appointment date has passed.
Action Required: Re-book an appointment.
Cancelled: Appointment has been cancelled by the user.
Action Required: Re-book an appointment.
Application Dashboard
A centralized dashboard for residents to view, manage, and track all their pre-registration applications and statuses in one place.
Chronological Sorting: Applications are sorted by creation date, with the newest first.
Visual Status Indicators: Each application displays a clear status.
Bulk Operations: Select multiple applicants for group actions.
Persistent Storage: Expired and cancelled applications remain visible for reference and re-booking.
Application Lifecycle Management
Efficiently manage the entire lifecycle of pre-registration applications, from creation and modification to tracking and deletion.
Create New Applications: Generate multiple applications as needed.
Data Modification: Edit demographic data and documents before booking an appointment.
Application Preview: Residents can review all entered information—including demographic details and uploaded documents before final submission to ensure accuracy.
Version Control: Maintain a history of changes to application data, allowing users and administrators to track modifications and preserve data integrity throughout the application lifecycle.
Delete Applications: Permanently delete applications.
The Appointment Booking allows users to select a registration center using criteria such as postal code or geo-location. Once a center is chosen, available time slots are displayed for scheduling. Users also have the flexibility to cancel or re-book appointments as needed.
Discover and select registration centers using postal code, location-on-map, or search criteria for convenient appointment booking.
Recommended Centers: Automatically suggests centers based on demographic details (e.g., postal code).
Location-based Search: Find centers using geo-location with a "Nearby" option.
Search Functionality: Search centers by name, address, or other criteria.
Center Information Display: View details such as working hours and available services for each center.
Distance Estimation: Can display a map with nearby registration center indicators on it.
Efficiently manage and book available time slots for identity registration appointments with real-time updates and capacity controls.
Calendar Interface: User-friendly calendar displays available dates and booking counts.
Time Categorization: Slots are organized by morning and afternoon sessions (configurable).
Real-time Availability: Live display of available time slots.
Capacity Management: Slot availability is managed based on center capacity.
Multi-applicant Booking: Book appointments for multiple applicants in a single session.
Appointment Flexibility empowers users to easily reschedule or cancel appointments, ensuring adaptability to changing schedules.
Rescheduling: Modify appointment date/time easily, with a notice period which is configurable (e.g., 48 hours).
Cancellation: Cancel appointments and automatically release slots for others.
Booking Confirmation: Receive instant confirmation with unique appointment details.
Time Restrictions: Minimum time between booking and appointment is configurable.
Booking or Re-Booking: While booking or re-booking, only the current or future date and time is displayed.
The Notification and Acknowledgment System ensures residents receive timely updates about their pre-registration status and appointments through email and SMS. Upon successful booking, users are provided with an acknowledgment that includes their AID and a QR code, which can be printed or presented digitally at registration centers for efficient processing.
Stay informed with instant, multi-channel notifications and acknowledgments for every step of your pre-registration journey.
Email Notifications: Receive appointment confirmations, reminders, and updates via email.
SMS Alerts: Get critical updates and appointment reminders through SMS.
A single, unified system for delivering secure, real-time notifications and digital acknowledgments to residents throughout the pre-registration process.
Multiple Delivery Options:
Print acknowledgment directly from the portal.
Download acknowledgment as a PDF.
Send acknowledgment via registered email.
Send acknowledgment via SMS to the registered mobile numbers.
Complete Information Package: Acknowledgment includes AID and relevant application details.
The Notification and Acknowledgment System delivers timely updates and confirmations to residents throughout the pre-registration process via email and SMS.
Booking Confirmations: Immediate notification upon successful appointment booking, re-booking and cancellation.
Status Updates: Alerts for changes in application status.
OTP Notifications: OTPs for login.
At the registration center, residents present their AID or QR code, allowing staff to quickly retrieve and pre-fill registration forms with pre-registration data. This seamless integration streamlines the enrollment process and reduces manual data entry.
Pre-registration integrates directly with the Registration Client, allowing registration centers to securely access and download resident data for scheduled appointments. This streamlines registration and minimizes manual data entry.
Data Download: Registration centers can securely download pre-registration data for scheduled appointments.
Offline Support: Enables access to pre-registration data even when the registration center is offline.
Data Pre-filling: Automatically populates registration forms with resident data from pre-registration, reducing manual entry.
Integrates real-time master data to ensure accurate, up-to-date information for location selection, center details, and appointment scheduling.
Dynamic Dropdowns: Utilizes real-time data from the Master Data service to populate location and center selection fields.
Center Information: Provides up-to-date details on registration centers, including capacity and availability.
Holiday Management: Integrates with holiday calendars to manage appointment slot availability and prevent bookings on non-working days.
The following section describes the security and privacy measures that protect resident data throughout the pre-registration process.
Pre-registration enables secure and efficient online identity onboarding.
Encryption: All PI data is protected with end-to-end encryption throughout the registration process.
Audit Logging: Every user action is recorded to provide a comprehensive audit trail for security and compliance.
Pre-registration ensures secure, privacy-focused handling of resident data with robust consent and anonymization controls.
Consent Management: Users provide granular consent for data usage, ensuring transparency and compliance.
Data Anonymization: Personal data is anonymized as per regulatory requirements, ensuring that sensitive information is masked or removed when not needed for processing. This protects resident privacy and supports compliance with data protection standards.
Right to Deletion: Residents can request deletion of their personal data in accordance with applicable privacy regulations.
Automatic Center Suggestions: As mentioned above with Registration Center Discovery, Pre-reg can also let a user find the recommended registration centers based on postal code and demographic information. This enhances user experience by eliminating the need to manually search in the portal for registration centers.
Locate-On-Map: Users can easily find the nearest registration centers on an interactive map.
Safe Date Selection while Booking and Re-booking: The system prevents users from selecting past dates during booking or re-booking, reducing manual errors.
VID Service provides functionality to create/update Virtual IDs mapped against an UIN. It also provides the facility to update the status of VID. VIDs are created based on the VID policy defined in the configuration.
The documentation here will guide you through the prerequisites required for the developer' setup.
Below are a list of tools required in ID Repository VID Services setup:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up ID Repository (VID Services) on your local system:
1. Download lombok.jar and settings.xml from here.
2. Unzip Apache Maven and move the unzipped folder in C:\Program Files and settings.xml to "conf" folder C:\Program Files\apache-maven-3.8.4\conf.
3. Install Eclipse, open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update.
4. Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if the lombok.jar is added. By doing this, you don't have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
5. Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the Code Contributions.
Open the project folder where pom.xml is present.
Open command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true to build the project and wait for the build to complete successfully.
After building of a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of project, update the project by right-click on Project → Maven → Update Project.
1. For the environment setup, you need an external JAR that is available here with different versions. (E.g.: You can download kernel-auth-adapter.jar and add to project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
2. Clone mosip-config repository.
3. Create an empty folder inside the mosip-config with sandbox-local name and then copy and paste all config files inside sandbox-local folder except .gitignore, README and LICENSE.
4. As Id Repository is using two properties files, id-repository-default and application-default, you will have to configure them according to your environment. The same files are available here for reference.
Properties to be updated:
application-default.properties
mosip.mosip.resident.client.secret = <current_password>.
db.dbuser.password=<password>.
mosip.kernel.xsdstorage-uri=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
Comment this out auth.server.admin.issuer.internal.uri in application-default.properties file because you already have this auth.server.admin.issuer.uri , and hence there is no need of auth.server.admin.issuer.internal.uri.
mosip.identity.mapping-file=<Path_to_identity_mapping_json_file>. (For Example: file:///home/user/Desktop/tspl/mosip-config/sandbox-local/identity-mapping.json)
id-repository-default.properties
mosip.idrepo.db.url
mosip.idrepo.db.port
Comment out all the lines containing mosip.biometric.sdk.providers.finger, mosip.biometric.sdk.providers.face and mosip.biometric.sdk.providers.iris.
mosip.idrepo.mosip-config-url=file:///home/user/Desktop/tspl/mosip-config/sandbox-local/(i.e. sandbox-local folder location).
5. To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
6. Put both the files in the same folder and change the location attribute to sandbox-local folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
java -jar -Dspring.profiles.active=native -Dspring.cloud.config.server.native.search-locations=file:C:\Users\myDell\mosipProject\mosip-config\sandbox-local -Dspring.cloud.config.server.accept-empty=true -Dspring.cloud.config.server.git.force-pull=false -Dspring.cloud.config.server.git.cloneOnStart=false -Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar.
7. Run the server by opening the config-server-start.bat file.
The server should now be up and running.
Below are the configurations to be done in Eclipse:
1. Open Eclipse and run the project for one time as Java application, so that it will create a Java application which you can see in debug configurations and then change its name. (e.g.: project name with environment - "vid-service-dev").
2. Open the arguments and pass this -Ddomain.url=dev.mosip.net -Dapplication.base.url=http://localhost:8090 -Dspring.profiles.active=default -Dspring.cloud.config.uri=http://localhost:51000/config -Dspring.cloud.config.label=master in VM arguments.
3. Here, the domain URL represents the environment on which you are working (eg., it can be dev2.mosip.net or qa3.mosip.net).
4. Click Apply and then debug it (starts running).
For API documentation, refer here.
The APIs can be tested with the help of Swagger-UI.
Swagger is an interface description language for describing restful APIs expressed using JSON. You can access Swagger-UI of resident-services for localhost from http://localhost:8091/idrepository/v1/swagger-ui/index.html?configUrl=/idrepository/v1/v3/api-docs/swagger-config#/.
ID Authentication is built as an independent service that can be seeded with data for authentication by any system, including MOSIP. In the current design, we can have multiple IDA modules running from a single issuer.
The ID Authentication (IDA) module of MOSIP consists of the following services:
Authentication Services
OTP Service
Internal Services
To learn more about it, refer to the below video:
The services mentioned below are used by Authentication or e-KYC Partners.
Authentication Service: used to authenticate an individual's UIN/VID using one or more authentication types.
KYC Authentication Service: used to request e-KYC for an individual's UIN/VID using one or more authentication types.
OTP Request Service is used by Authentication/e-KYC Partners to generate OTP for an individual's UIN/VID. The generated OTP is stored in IDA DB for validation during OTP Authentication.
Internal Authentication Service - The authentication service used by internal MOSIP modules such as Resident Service, Registration Processor and Registration Client to authenticate individuals.
Internal OTP Service - used by Resident Service to generate OTP for an Individual for performing OTP Authentication.
Authentication Transaction History Service - used by Resident Service to retrieve a paginated list of authentication and OTP Request transactions for an individual.
ID Authentication uses the credential data of the individuals for performing authentication.
This credential is requested by ID Repository upon any UIN insertion/update or VID creation.
WebSub invokes the credential-issuance callback in ID Authentication where the credential data is downloaded from Datashare and then stored in IDA DB.
ID Authentication needs the below keys to be generated during the deployment for usage in Authentication Service.
IDA IDENTITY_CACHE(K18) symmetric key to encrypt and decrypt the Zero-knowledge 10K random keys
IDA ROOT master key(K15)), IDA module master key(K16), IDA-SIGN master key
Base keys CRED_SERVICE(K22), IDA-FIR(K21), INTERNAL(K19), PARTNER(K20)
This is a reference application to demonstrate how authentication and KYC can be performed by Authentication Partners.
Refer to the repository for more details.
Below is the sample authentication demo UI image.
The ID Authentication service now offers an Authentication Error Eventing feature. When an authentication related error occurs, a message will prompt to the user to retry after a few minutes. In the meantime, Kafka event will be triggered to publish the data to the designated topic, allowing subscribers to receive a message for further processing.
This feature can be utilized for different use cases such as on demand template extraction, report generations, to identify any fraudulent occurrence etc.
One such use case is on demand template extraction. In an instance where a user has successfully registered and obtained a valid UIN/VID but encounters an error during authentication due to unavailability of the entered UIN/VID in the IDA DB, this feature comes into play. This issue tends to occur particularly during periods of high registration and UIN generation volumes, where additional time is needed for data transmission from the ID Repo to the IDA DB. This authentication error eventing feature will help in capturing the errors related to this issue and event will be created. subscribers can capture this event and process them accordingly to enable the template extraction to proceed with the authentication/verification process.
This feature is designed to be a plugin feature in IDA, which can be configured based on the requirement. To enable the feature below property should be marked as True:
mosip.ida.authentication.error.eventing.enabled=true
Once this property is enabled, related kafka property setup should be installed to utilize the feature.
For further guidance on this feature, you can refer here
Subscribers who will be subscribing to the event should be onboarded as authentication partners. To on board subscribers below steps needed to be followed:
Steps to onboard the subscribers:
Create a policygroup by the name mpolicygroup-default-tempextraction
The policy should be configured to not allow any authentication to be carryout but the partner except reading the kafka event. To attain this, allowedAuthTypes should be marked as null
For example:
{"authTokenType":"partner","allowedKycAttributes":[{"attributeName":"fullName"},{"attributeName":"gender"}, {"attributeName":"residenceStatus"},{"attributeName":"dateOfBirth"},{"attributeName":"photo"}],"kycLanguages":["ara","eng"],"allowedAuthTypes":[]}
Publish the policygroup and policy
Refer this link to onboard the subscribers as authentication partners. The name of the partner should be mpartner-default-tempextraction
Note: This feature is exclusively available in ID Authentication version 1.2.1.0 only. To configure the latest version of IDA and access this new feature, please refer to this link here
Refer to ID Authentication Configuration Guide.
To know more about the developer setups, read:
Refer API Documentation.
The documentation here will guide you through the pre-requisites required for developer setup.
JDK 11
Any IDE (Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
(file)
MOSIP Pre-registration specific JARs: The version will depend on which Pre Registration branch you have cloned. If it is "release-1.2.0.1" then you can download 1.2.0.1.B1 or 1.2.0.1.B2 version of below jars whichever is available.
Notepad++ (optional)
Fork the MOSIP from Github MOSIP repository to your GitHub account.
Clone the forked repository into your local machine.
git clone https://github.com/${urgithubaccname}/pre-registration.git
git remote add upstream https://github.com/mosip/pre-registration.git
git remote set-url --push upstream no_push
git remote -v
git checkout -b my-release-1.2.0.1
git fetch upstream
git rebase upstream/release-1.2.0.1
Inside settings.xml change local repository directory to your directory name where .m2 folder is located. E.g.: <localRepository>C:/Users/username/.m2/repository</localRepository>
Add settings.xml inside .m2 folder (Maven Folder). E.g.: C:\Users\username\.m2
Import the project in Eclipse IDE and it starts updating Maven projects configuration, refreshing workspaces, project starts building (downloading sources, javadoc).
Add downloaded lombok.jar to project, click on downloaded JAR and install specifying Eclipse IDE(eclipse.exe) location.
Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
Add MOSIP Pre-registration specific JARs from :
Adding JARs to Build Path: Right click on service -> Build Path -> Configure Build Path -> click on Classpath -> Add External JARs -> Add required JARs -> Apply and close.
Add auth-adapter, transliteration, ref-idobjectvalidator, virusscanner, lombok JARs to pre-registration-application-service, pre-registration-datasync-service classpath.
Add auth-adapter, lombok JARs to pre-registration-core, pre-registration-batchjob, pre-registration-captcha-service, pre-registration-booking-service classpath.
Run mvn clean install -Dgpg.skip=true command to build locally and to execute test cases.
Update Maven dependencies: Maven syncs the Eclipse project settings with that of the pom. It downloads dependencies required for the project.
Build and run the Project.
To run the pre-registration-application-service locally without config server, update values in application.properties and bootstrap.properties:
spring.cloud.config.uri=https://localhost:8080
spring.cloud.config.label=develop
spring.cloud.config.name=pre-registration
spring.application.name=pre-registration-application-service
spring.profiles.active=default Point below urls to a valid env which has MOSIP setup:
mosip.base.url=https://yourenvurl
auth-token-generator.rest.issuerUrl:https://iam.yourenvurl/auth/realms/mosip
javax.persistence.jdbc.password: XXXXXX
javax.persistence.jdbc.url=jdbc:postgresql://yourenvurl:5432/mosip_prereg
mosip.batch.token.authmanager.password: XXXXXX
mosip.iam.adapter.appid=prereg
mosip.iam.adapter.clientsecret=XXXXXX
auth.server.admin.issuer.uri=https://iam.yourenvurl/auth/realms/
Fork the to your GitHub account.
Clone the forked repository into your local machine.
git clone https://github.com/${urgithubaccname}/pre-registration-ui.git
git remote add upstream https://github.com/mosip/pre-registration-ui.git
git remote set-url --push upstream no_push
git remote -v
git checkout -b my-release-1.2.0.1
git fetch upstream
git rebase upstream/release-1.2.0.1
Install all dependencies with npm install.
Install Angular JS npm install -g @angular/cli.
Start the Angular JS server ng serve.
Open http://localhost:4200 to access the application.
You will face CORS issue since API Services are hosted on https://{env}.
Update the API services BASE_URL in config.json:
config.json is found inside assets directory.
E.g.: C:\MOSIP\pre-registration-ui\pre-registration-ui\src\assets\config.json
Create a new file named proxy.conf.json:
Location should be in C:\MOSIP\pre-registration-ui\pre-registration-ui\proxy.conf.json project folder.
Start the server by executing ng serve --proxy-config proxy.conf.json --ssl true.
Open the browser, load the app with https://localhost:4200.
For API documentation, refer .
The APIs can be tested with the help of Swagger-UI and Postman.
Swagger is an interface description language for describing restful APIs expressed using JSON. You can access Swagger-UI of pre-registration here:
Pre-registration Application service : https://{env}/preregistration/v1/application-service/swagger-ui.html
Pre-registration Datasync Service : https://{env}/preregistration/v1/sync/datasync-service/swagger-ui.html
Pre-registration Captcha service : https://{env}/preregistration/v1/captcha/swagger-ui.html
Pre-registration Booking service : https://{env}/preregistration/v1/appointment/booking-service/swagger-ui.html
This guide provides a comprehensive list of configurable properties for the Android Registration Client. Please note that this list is not exhaustive but serves as a helpful checklist for reviewing commonly configured properties.
It is important to acknowledge that all properties listed in this guide are automatically synchronized with the Android Registration Client. These properties are sourced from the registration-default.properties file.
In the registration-default.properties file, update the following property to specify the field values on which you want to enable the handle. Ensure that these field values match the field values in the IDSchema.
In the id-authentication-default.properties file, update the Regex to validate handles with the provided key as the postfix:
In the id-repository-default.properties file, map the postfix values with the corresponding field values:
application-default.properties
registration-default.properties
Timeouts in milliseconds are set during any HTTP calls to SBI.
Quality score threshold based on modality, Possible values 1 to 100
Retry attempts, Possible values 1 to 10
Quality score threshold based on the modality for operator authentication, Possible values 1 to 100`
Jobs like RID sync, packet upload, and status sync are carried out in batches, several registration records are to be executed in a batch on every trigger.
Default CRON expression for scheduling the Jobs.
mosip.registration.sync_jobs_restart_freq=0 0 */11 ? * *
Enables/disables reviewer authentication on any biometric exception during registration
mosip.registration.reviewer_authentication_configuration=Y
If enabled, cross-check of resident's biometrics with locally stored operator biometric templates.
mosip.registration.mds.deduplication.enable.flag=N
Minimum disk space required to create a packet - in MB
mosip.registration.disk_space_size=5
Maximum no. of days for approved packet pending to be synced to a server beyond which Registration Client is frozen for registration
mosip.registration.last_export_registration_config_time=100
No. of days beyond audit creation date to delete audits
mosip.registration.audit_log_deletion_configured_days=10
The maximum duration to which registration is permitted without sync of master data
mosip.registration.sync_transaction_no_of_days_limit=5
Allowed several invalid login attempts
mosip.registration.invalid_login_count=50
Configuration is used to check if any sync job is missed/ failed beyond expected days, this configuration is checked every time the operator clicks on any registration process. We follow the below convention to create this config key.
mosip.registration.job api name as in sync_job_def table.frequency=value in days
Date format to be displayed on acknowledgment slip, default value - dd/MM/yyyy hh:mm a
mosip.registration.application_date_format
Date format to be displayed on Registration Client dashboard, default format - dd MMM hh:mm a
mosip.registration.dashboard_date_format
Due to the absence of UI specifications in the 1.1.5.x versions, the android regclient addresses backward compatibility by migrating the schema of these versions to the LTS UI Spec structure.
To facilitate this migration, certain configurations and templates have been incorporated to ensure compatibility with the 1.1.5.x server. The list of these configurations is provided below.
mosip.registration.consent-screen-template-name=reg-consent-screen-content-template
The consent screen is not a part of 1.1.5.x schema structure. So, we are completely fetching this consent screen content from master.template table, and the templateTypeCode for the consent screen content is mentioned in the above configuration.
mosip.registration.individual-biometrics-id=individualBiometrics
The id of individual biometrics should be mentioned in the above property according to the configured 1.1.5.x schema.
mosip.registration.introducer-biometrics-id=guardianBiometrics
The id of guardian/ introducer biometrics should be mentioned in the above property according to the configured 1.1.5.x schema.
mosip.registration.infant-agegroup-name=INFANT
The age-group name for infants (aged below 5 years) which is configured in the configured server should be mentioned in the above property.
mosip.registration.agegroup-config={"INFANT":{"bioAttributes":["face"],"isGuardianAuthRequired":true},"ADULT":{"bioAttributes":["leftEye","rightEye","rightIndex","rightLittle","rightRing","rightMiddle","leftIndex","leftLittle","leftRing","leftMiddle","leftThumb","rightThumb","face"],"isGuardianAuthRequired":false},"SENIOR_CITIZEN":{"bioAttributes":["leftEye","rightEye","rightIndex","rightLittle","rightRing","rightMiddle","leftIndex","leftLittle","leftRing","leftMiddle","leftThumb","rightThumb","face"],"isGuardianAuthRequired":false}}
The above property indicates a list of age groups, required bio-attributes, and a flag that indicates whether guardian authentication is required or not. This property should be changed according to the server configuration and requirements.
mosip.registration.allowed-bioattributes=leftEye,rightEye,rightIndex,rightLittle,rightRing,rightMiddle,leftIndex,leftLittle,leftRing,leftMiddle,leftThumb,rightThumb,face
The above property defines the list of bio-attributes that are allowed for scanning during registration. If there are any changes in the server, it should be changed accordingly.
mosip.registration.default-app-type-code=000
The above property defines the default applicantTypeCode. In LTS, we have applicanttype.mvel script to fetch the documents according to age, gender, and some other attributes. Based on the applicant details, the script returns an applicantTypeCode which can be any value from “000” to “014”, and respective documents will be fetched from master.applicant_valid_document table. Since we do not have this script defined in 1.1.5.x to handle this, we have added a default applicantTypeCode.
Ensure that the preview and acknowledge templates are present in the template table of mosip_master database with the following type code:
reg-android-preview-template-part
reg-android-ack-template-part
Logout from ARC will check for any running background tasks in the background. Ask the user if the user still wants to logout from the application.
If the user clicks on logout on the popup, all the jobs running and scheduled jobs will stop.
If no jobs are running in the background, the user will simply log out and navigate to the login screen.
No configuration changes are required to log out of ARC.
Before fetching any Pre-Registration application on the registration page, clear all previously captured data.
The downloaded Pre-Registration packets will be stored locally at the following path:
Pre-registration applications fetch period, No. of days before the appointment date.
The Android Registration Client supports two types of password management:
Available on the Password Login screen.
Used when the operator has forgotten their password.
Clicking Forgot Password redirects to a configurable Keycloak URL.
Available on the Profile screen.
Used by a logged-in operator to change their existing password.
Clicking Reset Password redirects to the same configurable Keycloak URL.
This redirects the operator to a configurable URL:
Time in Seconds for forced log-out of the operator, if the operator is idle for the specified duration
mosip.registration.idle_time=900
Time in Seconds to display the warning message pop-up to the operator, if the operator is idle for the specified duration
mosip.registration.refreshed_login_time=600
Number of days beyond appointment date to delete unconsumed pre-registration application data
mosip.registration.pre_reg_deletion_configured_days=1
Enable GPS for capturing the geo-location. If y, GPS device will be enabled. If n, GPS device will be disabled.
mosip.registration.gps_device_enable_flag=N
The Distance Parameter for GPS Verification
mosip.registration.distance.from.machine.to.center=900000
mosip.registration.default-selected-handle-fields=email,phonemosip.ida.handle-types.regex={ '@email' : '.*@email$', '@phonenumber' : '.*@phonenumber$' }mosip.identity.fieldid.handle-postfix.mapping={'email':'@email', 'phone':'@phonenumber'}mosip.registration.mdm.connection.timeout=10000
mosip.registration.mdm.RCAPTURE.connection.timeout=40000
mosip.registration.mdm.MOSIPDINFO.connection.timeout=5000
mosip.registration.mdm.MOSIPDISC.connection.timeout=5000mosip.registration.leftslap_fingerprint_threshold=40
mosip.registration.rightslap_fingerprint_threshold=40
mosip.registration.thumbs_fingerprint_threshold=40
mosip.registration.iris_threshold=60
mosip.registration.face_threshold=9mosip.fingerprint_authentication.quality_score=30
mosip.iris_authentication.quality_score=30
mosip.face_authentication.quality_score=30mosip.fingerprint_authentication.quality_score=30
mosip.iris_authentication.quality_score=30
mosip.face_authentication.quality_score=30 mosip.registration.rid_sync_batch_size=5
mosip.registration.packet_upload_batch_size=5
mosip.registration.status_sync_batch_size=5 mosip.registration.registration_pre_reg_packet_location=PreRegPacketStoremosip.registration.pre_reg_no_of_days_limit=7mosip.registration.reset_password_url=${mosip.api.internal.url}/keycloak/auth/realms/mosip/account/{
"BASE_URL": "https://localhost:4200/proxyapi/",
"PRE_REG_URL": "preregistration/v1/"
}{
"/proxyapi": {
"target": "https://{env}/",
"secure": true,
"changeOrigin": true,
"pathRewrite": {
"^/proxyapi": ""
}
}
}The MOSIP Authentication SDK is a (Python-based) wrapper designed to simplify interaction with the MOSIP Authentication Service, enabling seamless integration of robust identity verification workflows into Python applications. This SDK abstracts complex details such as request/response structures, encryption/decryption mechanisms, and error handling, allowing developers to implement authentication workflows quickly and efficiently. Currently, the SDK supports OTP authentication and demographic authentication. Future updates will expand its functionality to include biometric authentication. Additionally, although the SDK is currently Python-based, we will soon be expanding support to other languages to offer broader compatibility.
This page provides an overview of the Authentication SDK, outlining its functionality and providing a detailed process for installing and testing the IDA API using the SDK.
While building your solution around MOSIP, it is recommended to use eSignet, MOSIP's OAuth- and OIDC-based solution, for most online and scalable authentication needs due to its modern, standards-compliant design. However, the MOSIP Authentication SDK offers its own advantages, particularly in the flexibility it provides, making it an invaluable tool for addressing a wide range of identity verification requirements.
Ease of Integration: Simplifies the process of working with MOSIP’s APIs, reducing the learning curve for developers
Consistency: Provides a uniform interface for different authentication operations, ensuring a consistent experience
Security: Manages encryption and decryption of requests and responses, adhering to MOSIP's security standards
Flexibility: Supports multiple authentication methods, including demographic authentication, offering versatility in identity verification workflows
Simplified API Interaction: Abstracts the complexity of direct API calls to MOSIP services
Support for Multiple Authentication Workflows: Includes controllers for both KYC-based and general authentication
Comprehensive Configuration: Allows customization via a configuration file (authenticator-config.toml)
Secure Handling: Automatically encrypts requests and decrypts responses to ensure secure communication
Error Management: Provides clear error messages and handling mechanisms
The SDK provides two primary controllers, each designed for a specific authentication workflow:
kyc-auth-controller Used for Know Your Customer (KYC) authentication. This controller facilitates verification using demographic data or OTP verification. Reference: KYC Auth Controller API Documentation
auth-controller Used for general authentication of individuals, allowing verification based on a wide range of identifiers such as demographic authentication and OTP authentication. Reference: Auth Controller API Documentation
The SDK provides two key methods for authentication:
kyc Method: Used for KYC-based authentication by verifying an individual's demographic data and OTP.
auth Method: Handles general authentication requests with similar parameters as kyc.
Both methods require the individual's ID (individual_id), ID type (individual_id_type), demographic data (DemographicsModel), optionally an OTP, biometric data, and consent confirmation. These methods streamline identity verification processes for diverse use cases. Please refer below to know more about the methods.
Authenticates an individual using KYC-based workflow.
kyc(
individual_id: str,
individual_id_type: str,
demographic_data: DemographicsModel,
otp_value: Optional[str] = None,
biometrics: Optional[List[BiometricModel]] = None,
consent: bool = False
) -> ResponsePerforms a general authentication.
auth(
individual_id: str,
individual_id_type: str,
demographic_data: DemographicsModel,
otp_value: Optional[str] = None,
biometrics: Optional[List[BiometricModel]] = None,
consent: bool = False
) -> ResponseCommon Parameters
individual_id (str): The unique ID of the individual (e.g., VID, UIN)
individual_id_type (str): Specifies the type of ID used (e.g., VID, UIN)
demographic_data (DemographicsModel): A model containing demographic details such as name and address
otp_value (Optional[str]): The One-Time Password (OTP) for authentication, if applicable
consent (bool): Indicates if the individual has given consent for authentication
Pre-requisites:
Before beginning the installation and configuration of this SDK, the user must complete the following steps:
Register as an Authentication Partner (AP): Register their organization as an Authentication Partner. Please refer to this link here and follow the steps for registration.
Obtain the IDA-FIR(K21) Certificate: The user must possess the IDA-FIR(K21) certificate. The certificate can be obtained here.
Provide required details in the request:
app id: IDA
ref : IDA-FIR
Install pip on the machine: The user should install pip to manage Python packages. Installation instructions can be found here.
During installation, the SDK must be configured by updating the authenticator-config.toml file. Please refer to this link here for the configuration file, This file contains essential details, such as:
Service Endpoints
Encryption Keys
Timeout Settings
Logging Settings
Refer to this link here for a sample configuration file to guide you in the setup process.
Install the SDK using pip:
pip install git+https://github.com/mosip/[email protected]Users who wish to try out this SDK should follow these steps:
Initialize the Authenticator: Set up the authentication instance to begin interacting with the SDK
Create Demographic Data: Prepare the necessary demographic information required for authentication
Perform Authentication: Execute the authentication request using the SDK
Handle the Response: Process and utilize the response received from the authentication service
For detailed guidance on performing these steps during the installation process, please refer to the model implementation below.
Basic Example:
from mosip_auth_sdk import MOSIPAuthenticator
from mosip_auth_sdk.models import DemographicsModel, BiometricModel
# Initialize the authenticator
authenticator = MOSIPAuthenticator(config={
# Configuration settings (refer to authenticator-config.toml for details)
})
# Create demographic data
demographics_data = DemographicsModel(
name="John Doe",
address="123 Main Street"
# Add other fields as required
)
# Perform KYC authentication
response = authenticator.kyc(
individual_id="123456789",
individual_id_type="VID",
demographic_data=demographics_data,
otp_value="1234",
consent=True
)
# Handle the response
if response.status_code == 200:
decrypted_data = authenticator.decrypt_response(response.json())
print("Authentication successful:", decrypted_data)
else:
print("Authentication failed:", response.json())The SDK provides clear error messages and codes to help diagnose issues effectively. Review the errors field in the response for details.
All communication with the MOSIP service is securely encrypted. Use the decrypt_response method to handle encrypted responses appropriately.
The MOSIP Authentication SDK simplifies the integration of robust authentication workflows into Python applications, ensuring secure, efficient, and compliant identity verification. By abstracting the complexities of direct API interaction, the SDK enables developers to focus on building impactful solutions without having to manage intricate implementation details.
If you require any assistance or encounter any issues during the testing and integration process, kindly reach out to us through the support provided below.
Navigate to Community.
Provide a detailed description about the support you require or provide complete information about the issue you have encountered, including steps to reproduce, error messages, logs and any other required details.
Thank you. Wishing you a pleasant experience!

Tag: 169 (identity-data)
Data Item: JSON Object
Semantics: Identity Data of a Person in QR-Code
Point of Contact: Resham Chugani ([email protected])
IANA Registration: IANA CWT Registry (Search Key: 169)
Version: 1.0.0
This document specifies a generic data structure and encoding mechanism for storing the Identity Data of a registered person using any ID platform. It also provides a transport encoding mechanism in a machine-readable optical format (QR).
Once a person is registered in an identity system, their data serves as the foundation for identification, granting them access to social benefits and government services. The level of assurance in this identification process varies depending on the authentication methods employed. Low assurance is achieved through basic identifiers like ID numbers, demographic data, passwords, or PINs. Conversely, higher assurance levels are attained through one-time passwords (OTP) and biometrics.
Among these methods, biometric-based authentication, such as facial authentication, offers the highest level of assurance as it assures the presence of the individual. While this is effective for online systems & personal phones where verification is conducted on a server or a personal device; offline authentication presents challenges in maintaining a similarly high level of assurance. The offline authentication mechanism should work for people with no phone.
For instance, in a cross-border scenario, remote areas often face significant internet connectivity issues. Even when internet access is available, server reliability may be inconsistent. In such circumstances, scanning a standard QR code containing the person's facial photograph and identity information, alongside assurance that the data is country-signed, provides an additional layer of security and affirmation for the countries involved.
Please note: The trust layers required to sync the country's key are beyond the scope of this document. We assume the app scanning the QR code already has the country's key to verify.
To tackle the aforementioned challenge, we propose a standard CBOR-based QR Code that involves embedding a low-resolution image of the person with a minimal demographic dataset within the QR code. This QR code would be digitally signed by the ID authorities (Issuer) and then printed on a physical card. Subsequently, the signed data within the QR code can be utilized for facial authentication. This approach also helps enhance interoperability. Note: It is essential to recognize that QR codes have limitations regarding size. We suggest leveraging CBOR Web Token (CWT) with ED25519/ECC keys to generate a smaller signature and more condensed data.
Claim 169 represents a JSON Object that includes the following ID attributes, as outlined in the table. You can find an illustration of the ID structure contained within Claim 169, as stated below:
Note:
All the fields here are optional.
The issuer of IDClaim169 is expected to host the JWKS file at the standard .well-known URL. This allows relying parties to verify the signature of the issued IDClaim169.
1
tstr
ID
Unique ID to indicate the PII data
2
tstr
Version
Version of the ID data
3
tstr
Language
Language used in other attributes: Use the three-letter language code
4
tstr
Full Name
Full name of the person
5
tstr
First Name
First name of the person
6
tstr
Middle Name
Middle name of the person
7
tstr
Last Name
Last name of the person
8
tstr
Date of Birth
Date of birth in YYYYMMDD format
9
tstr
Gender
Gender with the following values: 1 - Male, 2 - Female, 3 - Others
10
tstr
Address
Address of the person - Separator character \n
11
tstr
Email ID
Email id of the person
12
tstr
Phone Number
Contact number of the person: Use international notation
13
tstr
Nationality
Nationality of the person: Use the two-letter country code
14
int
Marital Status
Marital status - Can contain the following values: 1 - Unmarried, 2 - Married, 3 - Divorced
15
tstr
Guardian
Name/id of the entity playing the role of a guardian, such as a mother, father, spouse, sister, legal guardian etc.
16
tstr
Binary Image
Binary image of the person's photograph
17
int
Binary Image Format
Binary image format. Can contain the following values 1 - JPEG, 2 - JPEG2, 3 - AVIF, 4- WEBP
18
[int]
Best Quality Fingers
An unsigned 8-bit number encoding the hand position of the finger. It must be in the range 0-10, where 0 represents "Unknown", 1-5 represents right thumb to little finger, and 6-10 represents left thumb to little finger in sequence
19.. 99
tstr
Reserved
Reserved for future attributes
{
"1":"COUN",
"6":1665980929,
"8":{
"3":"dfd1aa976d8d4575a0fe34b96de2bfad"
},
"169":{
"1": "11110000324013",
"2": "1.0",
"3": "eng",
"4": "Peter M Jhon",
"5": "Peter",
"6": "M",
"7": "Jhon",
"8": "19880102",
"9": 1,
"10": "New City, METRO LINE, PA",
"11": "[email protected]",
"12": "+1 234-567",
"13": "US",
"14": 2,
"15": "Jhon Honai",
"16": "03CBABDF83D068ACB5DE65B3CDF25E0036F2C546CB90378C587A076E7A759DFD27CA7872B6CDFF339AEAACA61A6023FD1D305A9B4F33CAA248CEDE38B67D7C915C59A51BB4E77D10077A625258873183F82D65F4C482503A5A01F41DEE612C3542E5370987815E592B8EA2020FD3BDDC747897DB10237EAD179E55B441BC6D8BAD07CE535129CF8D559445CC3A29D746FBF1174DE2E7C0F3439BE7DBEA4520CF88825AAE6B1F291A746AB8177C65B2A459DD19BD32C0C3070004B85C1D63034707CC690AB0BA023350C8337FC6894061EB8A714A8F22FE2365E7A904C72DEC9746ABEA1A3296ECACD1A40450794EDCD2B34844E7C19EB7FB1A4AF3B05C3B374BD2941603F72D3F9A62EAB9A2FDAEEEEC8EE6E350F8A1863C0A0AB1B4058D154559A1CD5133EFCF682ABC339960819C9427889D60380B635A7D21D017974BBA57798490F668ADD86DA58125D9C4C1202CA1308F7734E43E8F77CEB0AF968A8F8B88849F9B98B26620399470ED057E7931DED82876DCA896A30D0031A8CBD7B9EDFDF16C15C6853F4F8D9EEC09317C84EDAE4B349FE54D23D8EC7DC9BB9F69FD7B7B23383B64F22E25F",
"17": 2,
"18": [1,2],
}Claim Name: identity-data
Claim Description: Registering the claim for storing identity data of a person, which could be personally identifiable data (PII) mostly used in Foundational/National ID for cross-border interoperability.
Claim Key: 169
Claim Value Type(s): map
Change Controller: MOSIP
Specification Document(s): Section 3, Section 4
[1] C. Bormann, and P. Hoffman. "Concise Binary Object Representation (CBOR)". RFC 7049, October 2013.
[2] Mike Jones, Hannes Tschofenig, Ludwig Seitz "CBOR Web Token (CWT)". RFC 8392, March 2018.
Mahammed Taheer ([email protected])
Resham Chugani ([email protected])
Rounak Nayak ([email protected])
Sasikumar G ([email protected])
Sreenadh S ([email protected])
ID Repository contains the records of the identity of an individual and provides API based mechanism to store, retrieve, and update identity details by other MOSIP modules. ID Repository is used by Registration Processor, ID Authentication, and Resident Services.
ID Repository module consists of the following components:
Identity service
VID service
Credential service
Credential Request Generator service
Credential Feeder
Salt generator
Stores, updates, and retrieves identity information.
Also, retrieves and updates UIN status.
Identity service uses Biometric SDK (server) to extract templates from provided biometric data.
Above is the entity relationship diagram illustrated for the Identity service. NOTE: The numbers do not signify a sequence of operations or control flow. Arrows indicate the data flow.
Key Manager encrypts/decrypts data.
The credential request generator issues credentials for new/updated UIN data.
Object Store stores/retrieves biometrics and demographic documents.
All demographic data of UIN and references to biometric and demographic files stored in the object store are stored in mosip_idrepo DB.
Partner management service retrieves online verification partners to issue credentials.
Audit logs are logged into Audit Manager.
Biometric SDK extracts the templates for input biometric data.
Auth Adapter integrates with KeyCloak for authentication.
Masterdata service retreives Identity schema based on input schema version.
WebSub publishes events related to UIN updation and auth type status updates.
Kernel ID generator generates UIN.
VID service fetches the list of VIDs associated with UIN to issue credential of update UIN and to create and activate draft VID.
VID Service provides functionality to create/update Virtual IDs mapped against a UIN. It also provides the facility to update the status of VID. VIDs are created based on the VID policy defined in the configuration.
Key Manager encrypts/decrypts data.
The credential request generator issues credentials for new/updated UIN data.
All VID related data is stored in mosip_idmap DB.
Partner management service retrieves online verification partners to issue credentials.
Audit logs are logged into Audit Manager.
The Auth Adapter integrates with KeyCloak for authentication.
WebSub publishes events related to VID updation.
The kernel ID generator generates VID.
The identity service checks the status of UIN to create a VID.
Key Manager encrypts/decrypts data and also used to sign data.
WebSub subscribes to get notifications related to credential status from IDA.
DataShare creates datashare url for sharable attributes.
Identity service retrieves identity data for UIN/VID.
Partner management service retrieves policies related to credential type and also retrieves policy for bio-extraction.
Auth Adapter integrates with KeyCloak for authentication.
A credential can be defined as any document, object, or data structure that vouches for the identity of a person through some method of trust and authentication. Simply put, a credential is the thing that a person presents—in person or remotely—to say "this is who I am." The types of credentials issued in an ID system vary along multiple dimensions, depending on whether they are physical (i.e., they must be physically carried by a person in order to use them), or digital (i.e., they are machine readable and therefore can be used in a digital environment).
A credential type essentially maps to partner and data share policy.
Default credential types provided as part of sandbox deployment are given below:
auth: Represents individual's data shared with Online Verification Partners (further used for Authentication and eKYC).
qrcode: qrcode type is used for qrcode partners to issue qrcode related credential data.
euin: It is used to issue credential data to partners who wish to download euin card using euin policy.
reprint: Reprint auth type is used for issuing credential information to reprint partners.
vercred: To issue verifiable credentials to partners, vercred credential type is used.
These types are defined in partner_policy_credential_type table of mosip_pms database.
New credential types may be defined as per needs of a country.
This service creates request for credential issuance.
Key Manager encrypts/decrypts data.
The Auth Adapter integrates with KeyCloak for authentication.
This job will feed the existing UIN/ VID identity information to the newly deployed IDA instance.
This is a one-time job that populates salts that are used to hash and encrypt data for Identity and VID services. This job must be executed before deploying these services. The following tables are populated:
uin_hash_salt in mosip_idrepo DB.
uin_encrypt_salt in mosip_idmap DB.
In the MOSIP sandbox, the job is run here.
To know more about the developer setups, read:
Refer to API Documentation.
The guide here lists down some of the important properties that may be customized for a given installation. Note that the listing here is not exhaustive, but a checklist to review properties that are likely to be different from default. If you would like to see all the properties, then refer to the files listed below.
See for the location of these files.
Registration Client reaches SBI on 127.0.0.1 within the below configured port range. As per SBI spec, the allowed port range is from 4501 to 4600.
Timeouts in milliseconds are set during any http calls to SBI.
Quality score threshold based on modality, Possible values 1 to 100
Retry attempts, Possible values 1 to 10
Quality score threshold based on the modality for operator authentication, Possible values 1 to 100
Registration clients can be integrated with more than one bio-sdks. Possible values for "modality-name" are "finger", "iris" or "face".
SDK implementation class full name
mosip.biometric.sdk.providers.<modality-name>.<vendor-name>.classname
SDK API version
mosip.biometric.sdk.providers.<modality-name>.<vendor-name>.version
SDK implementation class constructor args - comma separated
mosip.biometric.sdk.providers.<modality-name>.<vendor-name>.args
SDK initialization args, this will be passed as initparams
mosip.biometric.sdk.provider.<modality-name>.<vendor-name>.<key1>=<value1>
Quality threshold used by SDK to match modality
mosip.biometric.sdk.providers.<modality-name>.<vendor-name>.threshold
Example configurations are shown below for MOCK SDK named as mockvendor:
On every successful biometric capture during registration, the Quality of the biometrics is computed by bio-sdk if below config is enabled. Possible values are Y/N.
mosip.registration.quality_check_with_sdk=Y
Jobs like RID sync, packet upload, and status sync are carried out in batches, number of registration records to be executed in a batch on every trigger.
Only the modalities configured will be collected during operator onboarding.
On every Pre-Registration application fetch in the registration page, clear all the captured data before the Pre-Registration application fetch. Set the field IDs which should not be cleared after the Pre-Registration application fetch. It is a comma-separated list of field ids as per UI-SPEC.
Storage Location to store the downloaded Pre-Registration Packets in the local system
Pre-registration applications fetch period, No. of days before the appointment date.
Comma-separated list of offline job IDs. Offline jobs are jobs that are not part of manual sync.
Comma separated list of untagged job IDs. Untagged jobs, which will be not part of manual sync but only from the scheduler.
Comma separated list of job IDs that need Registration Client restart.
Registration batch jobs scheduler.
Default CRON expression for scheduling the Jobs.
All the identified scanner implementations will be used to list the identified devices. For each device dpi, width and height can be configured. If it is not configured, it defaults to 0.
Values in this config mosip.registration.docscanner.id map support regex.
Enable GPS device for capturing the geo-location. If y, the GPS device will be enabled. If n, the GPS device will be disabled.
mosip.registration.gps_device_enable_flag=N
Model of the GPS Device
mosip.registration.gps_device_model=GPSBU343Connector
Timeout for connecting to GPS device
mosip.registration.gps_port_timeout=1000
GPS Serial Port in Linux machine
mosip.registration.gps_serial_port_linux=/dev/ttyusb0
GPS Serial Port in Windows machine
mosip.registration.gps_serial_port_windows=
The Distance Parameter for GPS Verification
mosip.registration.distance.from.machine.to.center=900000
To reset a password in the Registration Client, click Reset Password from the Actions menu in the top-right corner of the Home page. This redirects the operator to a configurable URL:
This configuration determines whether supervisor approval is required before the Sync and Upload of registration packets.
If enabled (Y), the system requires a supervisor to review and approve the registration packets before it is synched and uploaded.
If disabled (N), the registration proceeds auto approving, and packets are automatically uploaded in the next scheduled job.
Additionally, the system will cross-check the resident’s biometrics with locally stored operator biometric templates to verify the registration.
Minimum disk space that should be available in the machine to proceed with registration - in MB
Location to store registration packets in the client machine:
Number of days allowed to start Registration Client without upgrade when software upgrade is available.
mosip.registration.softwareUpdateCheck_configured_frequency=60
Time in Seconds for forced log-out of the operator, if the operator is idle for the specified duration
mosip.registration.idle_time=900
Time in Seconds to display the warning message pop-up to the operator, if the operator is idle for the specified duration
mosip.registration.refreshed_login_time=600
Maximum no. of days for approved packet pending to be synced to a server beyond which Registration Client is frozen for registration
mosip.registration.last_export_registration_config_time=100
Maximum no. of packets pending EOD approval beyond which Registration Client is frozen for registration
mosip.registration.reg_pak_max_cnt_apprv_limit=100
Enable supervisor authentication feature. If y, supervisor approval will be enabled, else, will be disabled
mosip.registration.supervisor_approval_config_flag=Y
No. of days beyond audit creation date to delete audits
mosip.registration.audit_log_deletion_configured_days=10
No. of days beyond the registration date to delete synced and uploaded registration packet:
mosip.registration.reg_deletion_configured_days=1
No. of days beyond the appointment date to delete unconsumed pre-registration application data
mosip.registration.pre_reg_deletion_configured_days=1
The maximum duration to which registration is permitted without sync of master data
mosip.registration.sync_transaction_no_of_days_limit=5
Allowed a number of invalid login attempts:
mosip.registration.invalid_login_count=50
Used to configure the time (in minutes) for locking the account after crossing the configured invalid login count
mosip.registration.invalid_login_time=2
Configuration is used to check if any sync job is missed/failed beyond expected days, this configuration is checked every time the operator clicks on any registration process. We follow the below convention to create this config key.
mosip.registration.job api name as in sync_job_def table.frequency=value in days
#Maximum no. of days without running the Master Sync Job beyond which Registration Client is frozen for registration
mosip.registration.masterSyncJob.frequency=190
#Maximum no. of days without running the Pre-Registration Sync Job beyond which Registration Client is frozen for registration
mosip.registration.preRegistrationDataSyncJob.frequency=190
#Maximum no. of days without running the Packet Sync Status Job beyond which Registration Client is frozen for registration
mosip.registration.packetSyncStatusJob.frequency=190
#Maximum no. of days without running the Key Policy Sync Job beyond which Registration Client is frozen for registration
mosip.registration.keyPolicySyncJob.frequency=190
#Maximum no. of days without running the Registration Deletion Job beyond which Registration Client is frozen for registration
mosip.registration.registrationDeletionJob.frequency=190
#Maximum no. of days without running the Configuration Sync Job beyond which Registration Client is frozen for registration
mosip.registration.synchConfigDataJob.frequency=190
#Maximum no. of days without running the Audit Logs Deletion Job beyond which Registration Client is frozen for registration
mosip.registration.deleteAuditLogsJob.frequency=190
Date format to be displayed on acknowledgment slip, default value - dd/MM/yyyy hh:mm a
Date format to be displayed on Registration Client dashboard, default format - dd MMM hh:mm a
are the self-services used by residents themselves via a portal. The Resident Portal is a web-based UI application that provides residents of a country with services related to their Unique Identification Number (UIN).
The documentation here will guide you through the prerequisites required for the developer's setup.
Below is a list of tools required in Resident Services:
JDK 11
Any IDE (like Eclipse, IntelliJ IDEA)
Apache Maven (zip folder)
pgAdmin
Postman
Git
Notepad++ (optional)
lombok.jar (file)
settings.xml (document)
Follow the steps below to set up Resident Services on your local system:
Download lombok.jar and settings.xml from .
Install Apache Maven.
Copy the settings.xml to ".m2" folder C:\Users\<username>\.m2.
Install Eclipse.
Open the lombok.jar file and wait for some time until it completes the scan for Eclipse IDE and then click Install/Update. Specify the eclipse installation location if required by clicking the ‘Specify location…’ button. Then, click Install/Update the button to proceed.
Check the Eclipse installation folder C:\Users\userName\eclipse\jee-2021-12\eclipse to see if lombok.jar is added. By doing this, you will not have to add the dependency of lombok in your pom.xml file separately as it is auto-configured by Eclipse.
Configure the JDK (Standard VM) with your Eclipse by traversing through Preferences → Java → Installed JREs.
For the code setup, clone the repository and follow the guidelines mentioned in the .
Open the project folder where pom.xml is present.
Open the command prompt from the same folder.
Run the command mvn clean install -Dgpg.skip=true -DskipTests=true to build the project and wait for the build to complete successfully.
After building a project, open Eclipse and select Import Projects → Maven → Existing Maven Projects → Next → Browse to project directory → Finish.
After successful importing of the project, update the project by right-clicking on Project → Maven → Update Project.
For the environment setup, you need an external JAR that is available with different versions. Download the below-mentioned JARs with appropriate latest/appropriate versions. You will need to input the appropriate artifact ID and version and other inputs.
a. icu4j.jar
b. kernel-auth-adapter.jar
c. kernel-ref-idobjectvalidator.jar
d. kernel-transliteration-icu4j.jar
E.g.: You can download kernel-auth-adapter.jar and add to the project Libraries → Classpath → Add External JARs → Select Downloaded JAR → Add → Apply and Close).
Clone .
a. As Resident Services is using two properties files- resident-default.properties and application-default.properties. But for the local running of the application, you need to provide additional/overriding properties such as secrets, passwords, and properties passed by the environment which can be added to new files application-dev-default.properties (common properties for all modules) and resident-dev-default.properties (Resident service-specific properties).
b. You will have to create both the property files according to your environment and put them in mosip-config folder (cloned). The same files are available below for reference.
These two files are loaded by the application by specifying the application names in the Application VM arguments like- Dspring.cloud.config.name=application,resident,application-dev, resident-dev (also detailed in a later section).
To run the server, two files are required- kernel-config-server.jar and config-server-start.bat.
Put both files in the same folder and point to the property- Dspring.cloud.config.server.native.search-locations to mosip-config folder in config-server-start.bat file and also check the version of kernel-config-server.jar towards the end of the command.
Example:
As mentioned earlier, you will have to create property files according to your environment like resident-env-default and application-env-default (here env represents environment name). Both files will contain different configurations such as resident-env-default will have config properties (e.g., secrets, passcodes, etc) used for the resident-services module only and application-env-default is used for environment-specific changes and can be used for other modules as well.
In this example, currently, these two files are created for the dev environment and hence the files have suffixes of -dev. If you want to run it for a different environment such as qa, create these two files with -qa suffixes, and then you will also need to provide the appropriate VM argument for that referring to qa environment.
For instance,
Add mosip.resident.client.secret=*********** property to be able to use a decrypted passcode and run it on your local machine.
If you check the URLs present in application-default the file, they are set to module-specific URLs, but you need to use internal/external environment URLs to access the APIs by using an application-dev-default file.
In application-dev-default file, assign environment domain URL to mosipbox.public.url , and change all other URLs with ${mosipbox.public.url}.
It results in mosipbox.public.url=internal/externalAPI (e.g., mosipbox.public.url=https://api-internal.dev.mosip.net) and it will connect with the Development environment.
Run the server by opening the config-server-start.bat file.
Open Eclipse and run the project for one time as a Java application, so that it will create a Java application which you can see in debug configurations, and then change its name. (e.g.: project name with the environment - "Resident-dev").
Open the Arguments tab and specify Application VM arguments: For example, for a development environment:
Save this run configuration as ‘Resident-dev’ .
For qa environment, you can create Resident-qa run configuration with VM argument as below.
Example:
Click Apply and then debug it (starts running). In the console, you can see a message like Started ResidentBootApplication in 34.078 seconds (JVM running for 38.361).
For API documentation, refer .
The APIs can be tested with the help of Postman or Swagger-UI.
Postman is an API platform for building and using APIs. Postman simplifies each step of the API lifecycle and streamlines collaboration so you can create better APIs—faster. It is a widely used tool for API testing. Below you will find the APIs postman collection of resident-services.
Swagger is an interface description language for describing restful APIs expressed using JSON. You can access Swagger-UI of resident-services for the dev-environment from https://api-internal.dev.mosip.net/resident/v1/swagger-ui.html and localhost from http://localhost:8099/resident/v1/swagger-ui.html.
Download the JSON collection available below and import it to your postman. .
Create an environment as shown in the image below.
This environment is created for dev. Give the variable name as url and set both values as https://api-internal.dev.mosip.net.
Similarly, create another environment as shown below.
This environment is created for localhost. Give the variable name as url and set both values as http://localhost:8099.
application-default.properties
registration-default.propertiesmosip.registration.mdm.portRangeFrom=4501
mosip.registration.mdm.portRangeTo=4600mosip.registration.mdm.connection.timeout=10000
mosip.registration.mdm.RCAPTURE.connection.timeout=40000
mosip.registration.mdm.MOSIPDINFO.connection.timeout=5000
mosip.registration.mdm.MOSIPDISC.connection.timeout=5000mosip.registration.leftslap_fingerprint_threshold=40
mosip.registration.rightslap_fingerprint_threshold=40
mosip.registration.thumbs_fingerprint_threshold=40
mosip.registration.iris_threshold=60
mosip.registration.face_threshold=9mosip.registration.num_of_fingerprint_retries=3
mosip.registration.num_of_iris_retries=3
mosip.registration.num_of_face_retries=3mosip.fingerprint_authentication.quality_score=30
mosip.iris_authentication.quality_score=30
mosip.face_authentication.quality_score=30mosip.biometric.sdk.providers.finger.mockvendor.classname=io.mosip.mock.sdk.impl.SampleSDK
mosip.biometric.sdk.providers.finger.mockvendor.version=0.9
mosip.biometric.sdk.providers.finger.mockvendor.args=
mosip.biometric.sdk.providers.finger.mockvendor.threshold=60
mosip.biometric.sdk.providers.iris.mockvendor.classname=io.mosip.mock.sdk.impl.SampleSDK
mosip.biometric.sdk.providers.iris.mockvendor.version=0.9
mosip.biometric.sdk.providers.iris.mockvendor.args=
mosip.biometric.sdk.providers.iris.mockvendor.threshold=60
mosip.biometric.sdk.providers.face.mockvendor.classname=io.mosip.mock.sdk.impl.SampleSDK
mosip.biometric.sdk.providers.face.mockvendor.version=0.9
mosip.biometric.sdk.providers.face.mockvendor.args=
mosip.biometric.sdk.providers.face.mockvendor.threshold=60mosip.registration.rid_sync_batch_size=5
mosip.registration.packet_upload_batch_size=5
mosip.registration.status_sync_batch_size=5mosip.registration.operator.onboarding.bioattributes=leftLittle,leftRing,leftMiddle,leftIndex,leftThumb,rightLittle,rightRing,rightMiddle,rightIndex,rightThumb,leftEye,rightEye,facemosip.registration.fields.to.retain.post.prid.fetch=consent,consentText,preferredLangmosip.registration.registration_pre_reg_packet_location=PreRegPacketStoremosip.registration.pre_reg_no_of_days_limit=7mosip.registration.jobs.offline=DEL_J00013,RDJ_J00010,ADJ_J00012,PVS_J00015mosip.registration.jobs.unTagged=PDS_J00003mosip.registration.jobs.restart=RCS_J00005mosip.registration.jobs.scheduler.enable=Ymosip.registration.sync_jobs_restart_freq=0 0 */11 ? * *mosip.registration.docscanner.id={ "id1" : "STUB-SCANNER", "id2" : "S600" }
mosip.registration.docscanner.dpi={ "id1" : 200, "id2" : 300 }
mosip.registration.docscanner.width={ "id1" : 200, "id2" : 350 }
mosip.registration.docscanner.height={ "id1" : 200, "id2" : 400 }mosip.registration.reset_password_url=${mosip.api.internal.url}/keycloak/auth/realms/mosip/account/mosip.registration.supervisor_approval_config_flag=Ymosip.registration.mds.deduplication.enable.flag=Nmosip.registration.disk_space_size=5 object.store.base.location=packets mosip.registration.application_date_format mosip.registration.dashboard_date_formatjava -jar -Dspring.profiles.active=native -
Dspring.cloud.config.server.native.search-
locations=file:C:\Users\myDell\mosipProject\mosip-config -
Dspring.cloud.config.server.accept-empty=true -
Dspring.cloud.config.server.git.force-pull=false -
Dspring.cloud.config.server.git.cloneOnStart=false -
Dspring.cloud.config.server.git.refreshRate=0 kernel-config-server-1.2.0-20201016.134941-57.jar-Dspring.profiles.active=default -
Dspring.cloud.config.uri=http://localhost:51000/config -
Dspring.cloud.config.label=master -Dsubdomain=dev -
Dspring.cloud.config.name=application,resident,application-dev,resident-dev --illegal-access=permit.-Dspring.profiles.active=default -
Dspring.cloud.config.uri=http://localhost:51000/config -
Dspring.cloud.config.label=master -Dsubdomain=qa -
Dspring.cloud.config.name=application,resident,application-qa,resident-qa --illegal-access=permitThe Registration Client provides a comprehensive, secure desktop application for capturing resident identity data at registration centers. This thick Java-based client enables operators to collect demographic and biometric information along with supporting documents in both online and offline modes. All captured data is cryptographically secured and packaged into registration packets for tamper-proof processing.
These features collectively address challenges like data security, offline operations, multi-language support, and seamless integration with MOSIP's identity ecosystem, resulting in efficient, secure, and user-friendly identity registration operations.
Secure operator authentication with role-based permissions ensures authorized personnel can perform registration activities efficiently while maintaining data security.
Multi-Role Operator Access
Professional operator management with distinct roles and capabilities for comprehensive registration center operations.
Supervisor Authority: Complete registration oversight with exclusive packet approval/rejection rights, plus all officer capabilities
Officer Operations: Comprehensive registration tasks including onboarding, data synchronization, software upgrades, packet management, and correction processing
Secure Authentication: Robust login system with operator credential verification and session management
Language Selection: Operators choose their preferred interface language during login for optimal usability
Operator Onboarding and Biometric Update
Self-service operator registration and biometric management for maintaining current operator credentials.
Self-Service Onboarding: Operators can register and update their biometric credentials anytime
Biometric Credential Management: Secure storage and validation of operator biometric data
Flexible Updates: Real-time operator biometric updates without system downtime
Comprehensive language support ensuring accessibility and accuracy across diverse populations and operator preferences.
Comprehensive Language Support
Flexible multi-language interface and data collection supporting diverse populations and operator needs.
Operator Interface Language: Operators select their preferred language during login for optimal workflow efficiency
Multi-Language Data Entry: Simultaneous data capture in multiple configured languages during registration process
Configurable Language Options: Operators choose from pre-configured languages before starting registration processes
Real-Time Language Switching: Dynamic language selection without interrupting registration workflows
End-to-end registration workflows supporting multiple registration types with comprehensive data capture and validation.
New Registration Processing
Complete identity enrollment for first-time applicants with comprehensive data capture and validation.
Consent Management: Systematic consent capture for data storage and utilization compliance
Demographic Data Entry: Comprehensive resident detail capture including name, gender, date of birth, and address information
Document Upload Support: Multiple document type handling including proof of address, identity, and birth certificates
Pre-Registration Integration: Auto-population of demographic data and documents using pre-registration IDs
Biometric Data Entry: Professional biometric capture with quality control for fingerprints, iris, and facial data
UIN Update Processing
Streamlined process for residents to update their demographic or biometric information.
Selective Field Updates: Residents choose specific fields requiring updates for efficient processing
UIN-Based Authentication: Secure identity verification using existing UIN credentials
Comprehensive Update Support: Support for both demographic and biometric data modifications
Configurable Update Options: Administrative control over available update fields and processes
Lost UIN Recovery
Secure identity recovery process for residents who have lost their identity credentials or never received them.
Biometric-Based Recovery: Mandatory biometric verification for secure identity recovery
Contact Information Updates: Update phone numbers and email addresses during recovery process
Flexible Data Requirements: Optional demographic data and document uploads for recovery cases
Secure Notification Process: Identity details sent to newly provided contact information upon successful recovery
Registration Correction Process
Systematic correction workflow for residents with pending UIN generation requiring data modifications.
Request ID Integration: Process corrections using provided RequestId for accurate case linking
Comprehensive Correction Support: Support for all registration data types including biometric corrections
Guided Correction Workflow: Step-by-step process ensuring accurate data correction and validation
Professional biometric data collection with quality control, exception handling, and device integration.
Quality-Controlled Biometric Capture
Advanced biometric capture with quality thresholds and automated retry mechanisms.
Quality Threshold Management: Configurable quality thresholds ensuring high-quality biometric data capture
Automated Retry Logic: Intelligent retry mechanisms for achieving optimal biometric quality
Device Timeout Controls: Configurable capture timeouts preventing prolonged capture sessions
Multi-Modal Capture: Support for fingerprint, iris, and face biometric capture based on country configuration
Biometric Exception Handling
Comprehensive exception handling for residents with missing or defective biometric features.
Exception Documentation: Systematic marking and documentation of permanent or temporary biometric exceptions
Proof of Exception Capture: Specialized photography for documenting biometric exceptions
Age-Based Capture Rules: Automatic adjustment of biometric requirements based on applicant age (adult vs. infant)
Flexible Exception Processing: Support for both temporary and permanent biometric exceptions
Robust offline capabilities ensuring continuous service delivery with intelligent data synchronization.
Complete Offline Functionality
Full registration capabilities without internet connectivity ensuring uninterrupted service delivery.
Offline Registration Processing: Complete registration workflows including demographics, biometrics, and documents without internet
Local Data Storage: Secure Derby database storage for offline registration data with encryption
Intelligent Queue Management: Automatic packet queuing during offline periods with seamless sync upon connectivity restoration
Pre-Registration Offline Access: Download and use pre-registration data locally during offline operations
Automated Data Synchronization
Comprehensive background synchronization keeping registration client current with server data.
Configuration Sync: Automatic synchronization of system properties, thresholds, and UI functionality settings
Master Data Updates: Real-time sync of dynamic fields, templates, locations, and authorization data
Certificate Management: Automated certificate updates including device CA certificates and encryption keys
User and Packet Sync: Synchronization of user details, registration packets, and processing status updates
Pre-Registration Data Management
Efficient pre-registration data handling for improved user experience and reduced processing time.
Batch Download Capability: Download pre-registration data for entire center during online periods
Encrypted Local Storage: Secure local storage of pre-registration packets with automatic cleanup
Cross-Center Access: Access any pre-registration application regardless of originally booked center
Automatic Data Cleanup: Configurable deletion of stored pre-registration data after specified periods
Comprehensive packet lifecycle management from creation to server upload with supervisor oversight.
Intelligent Packet Upload
Automated packet upload system with supervisor review integration and comprehensive status tracking.
Supervisor Review Integration: Systematic packet approval/rejection workflow before server upload
Batch Upload Processing: Efficient batch processing of approved packets with automatic scheduling
Comprehensive Status Tracking: Real-time visibility into both client and server packet processing status
Export Functionality: Packet export capabilities for local backup and manual processing needs
Background Upload Automation
Intelligent background processing ensuring continuous packet synchronization with minimal operator intervention.
Automatic Upload Scheduling: Configurable scheduled uploads based on approval requirements and system load
Metadata Synchronization: Comprehensive packet metadata sync improving recovery capabilities
Approval-Based Processing: Intelligent upload logic based on supervisor approval requirements
Auto-Upload Capability: Full automation support for environments not requiring manual approval
End-of-Day Management
Systematic end-of-day processes ensuring complete packet review and processing.
Supervisor Approval Workflow: Comprehensive packet review and approval interface for supervisors
Re-Registration Handling: Dedicated management for packets requiring re-registration
Authentication Integration: Secure supervisor authentication for packet approval decisions
Batch Approval Processing: Efficient handling of multiple packets during end-of-day procedures
Professional system management capabilities ensuring optimal performance and security.
Software Update Management
Automated software maintenance with version control and upgrade management.
Automatic Update Detection: Real-time checking for new client versions from upgrade servers
Confirmation-Based Upgrades: Operator-controlled upgrade process with confirmation prompts
Online Requirement Management: Intelligent online connectivity requirements for update processes
Version Compatibility Checks: Automatic validation of update compatibility before installation
Center Remapping Support
Comprehensive center transition management when machines are remapped between registration centers.
Pending Task Completion: Systematic completion of all center-related pending activities
Data Migration Management: Secure deletion of former center data and full sync with new center
Restart-Based Sync: Complete system refresh ensuring clean transition to new center configuration
Comprehensive Task Tracking: Monitoring of packet approvals, uploads, confirmations, and deletions during transition
Dashboard and Reporting
Comprehensive system monitoring and reporting for operational oversight.
Operator Activity Tracking: Detailed operator performance and activity monitoring
Packet Status Reporting: Real-time visibility into packet processing status and statistics
Sync Activity Monitoring: Comprehensive tracking of synchronization activities and system health
Customizable Dashboard: HTML template-based dashboard customization for country-specific requirements
Enterprise-level security measures protecting sensitive resident data throughout the registration lifecycle.
Hardware Security Integration
Advanced hardware security using TPM for comprehensive data protection and system authentication.
TPM-Based Machine Authentication: Hardware security module providing machine identity and authentication
Encrypted Database Protection: Derby database encryption using TPM-secured boot passwords
Packet Signing and Encryption: Cryptographically signed and encrypted registration packets
Key Management: Secure storage of sensitive files and encryption keys using TPM protection
Data Integrity Protection
Comprehensive data integrity mechanisms ensuring tamper-proof operations.
UI Specification Validation: Hash-based verification of UI specification files preventing tampering
Versioned Configuration Management: Tamper-proof versioned UI specifications with integrity checking
File Hash Verification: Continuous validation of critical system files during operation
Failure Protection: Automatic system protection when tampering is detected
Registration Packet Security
Multi-layered security for registration packets ensuring data confidentiality and integrity.
End-to-End Encryption: Complete encryption of registration packets from creation to processing
Digital Signatures: Cryptographic signatures ensuring packet authenticity and non-repudiation
Secure Storage Management: Configurable secure directories for packet and acknowledgment storage
Pre-Registration Encryption: TPM-encrypted storage for synced pre-registration data
Seamless integration with external devices and systems for comprehensive registration center operations.
Biometric Device Integration
Professional biometric device connectivity through standardized interfaces.
SBI Compliance: Full integration with Secure Biometric Interface standards
Port Range Scanning: Automatic device discovery across configured port ranges (4501-4600)
Multi-Device Support: Simultaneous connection and management of multiple biometric devices
Device Auto-Discovery: Intelligent detection and connection to available biometric devices
Document Scanner Integration
Direct integration with document scanning devices for efficient document capture.
Direct Scanner Connectivity: Seamless integration with document scanning hardware
Multi-Format Support: Support for various document formats and scanning requirements
Quality Control: Automatic document quality assessment and validation
Batch Scanning Support: Efficient processing of multiple documents during registration
Printer Integration
Professional printing capabilities for registration acknowledgments and receipts.
Print-Friendly Receipts: Optimized acknowledgment receipt formatting for professional printing
QR Code Generation: Automatic QR code generation for registration IDs on acknowledgment receipts
Multi-Language Printing: Support for acknowledgment printing in selected languages
Quality Ranking Display: Biometric quality rankings (1-10) displayed on printed acknowledgments
This guide describes the various functions provided in the Home page of the reference UI implementation of the registration client.
The Registration Client menu bar displays the following:
MOSIP logo
Home button
Logged in username
Center name
Machine name
Server connection status symbol (shows if the client is online or offline)
Breadcrumbs (User Guide/Reset Password/Logout)
Synchronize data is the data required to make the Registration Client(RC) functional. Full sync is performed initially during the launch of the RC for the first time. Post this, the RC syncs only the changes from sever and this is called as the delta sync. Synchronize data is automated and can be triggered manually. This happens automatically while launching the RC and is also manually initiated by the operator.
Configuration sync: Sync of properties which drives in deciding the RC UI functionality. For example: Invalid login attempts, idle timeout, thresholds, etc.
Masterdata sync : As a part of this sync, supporting information like Dynamic fields data, templates, locations, screen authorization, blocklisted words, etc. are pulled in.
UserDetails sync: userID, along with their status is synced. Only the user details belonging to machine mapped center will be synced.
Certificate sync: Certificates used to validate the server signatures, device CA certificates, public key (specific to a center and machine, also called as policy key) used to encrypt the registration packet will be synced.
Packet sync:
All the approved/rejected Registration IDs(RIDs) will be synced to the server.
All the synced RID packets will be uploaded to the server.
All the uploaded packet status will be synced from server.
An operator can download the pre-registration data of a machine mapped center while being online and store it locally in the registration machine for offline use. Now, when the system is offline and the pre-registration data is already downloaded, the operator can enter the pre-registration ID to auto-populate the registration form. Provided the machine is online, any pre-registration application can be downloaded irrespective of the center booked by the resident.
This pre-registration data is downloaded from pre-registration API as an encrypted packet and stored in the local storage.There is a batch job running in background for deleting the pre-registration packets after configurable number of days.
Note- Date Range of pre-registration data to be downloaded and storage location of pre-registration data in the registration machine is configurable. Also, this is synced as a part of configuration sync.
Using this option, the operators can onboard themselves anytime.
For more details, refer Operator Onboarding Guide.
Application upload refers to upload of supervisor reviewed registration packets (approved and rejected). From this page, the operator can export the packets to any location on their machine on clicking Save to Device button.
Upload of registration packet from this page internally performs two operations in sequence:
Sync registration metadata to server
On successful sync of metadata, actual registration packets are uploaded to the server.
Client Status: This column displays the status of a registration packet based on the above mentioned operation.
APPROVED
REJECTED
SYNCED
EXPORTED
Server Status:
On success,
PUSHED
PROCESSED
ACCEPTED
On failure,
REREGISTER
REJECTED
RESEND
This column displays the type of registration packet (New packet, Lost packet, Update packet, Correction packet)
When a machine is re-mapped from one center to another center, all the pending activities in the machine related to the former center needs to be completed.
On successful completion of pending tasks, the former center's details will be deleted from the local Derby DB and a full sync will be initiated to pull in the new center details.
Packet Approvals/rejections
Packet upload
Server confirmation on receiving a packet
Deletion of packets after receiving a confirmation
Deletion of pre-registration packets
Deletion of center specific data like the public/policy key
Note- After completing the above tasks, a restart will be prompted to initiate the full sync with new center details.
Clicking on this button, triggers a check for any new client version availability in the upgrade server.
The machine must be online to be able to check updates.
If there is any new version available, a confirmation pop-up is displayed to the operator for starting the upgrade or a reminder is displayed.
The operator can initiate any task from amongst- New registrations, Update UIN, Lost UIN, Correction flow. To get started, the operator needs to select a language for data entry. The number of languages displayed in the UI is configurable and depends on the country.
An operator can initiate the process of registering a new applicant in the MOSIP ecosystem by filling the new registration form with the resident.
Below are few of the processes that needs to be completed for a new registration.
Capture consent- For every registration, the registration client provides an option for the operator to mark an individual's consent for data storage and utilization.
Enter demographic data and upload documents If the resident has a pre-registration application ID, the operator can auto-populate the demographic data and the documents by entering the pre-registration ID. If the resident does not have a pre-registration ID, the operator can enter the resident’s demographic details (such as Name, Gender, DOB, Residential Address, etc.) and upload the documents (such as Proof of Address, Proof of Identity, Proof of Birth) based on the ID Schema defined by the country.
Capture biometrics of a resident The capture of biometrics is governed by the country, i.e. capture of each modality (fingerprint, iris or face) can be controlled by the country using the global configuration. When the operator clicks on the Capture button and tries to capture the biometrics of the resident, the device needs to make the capture when the quality of the biometrics is more than the threshold configured by the country. The device will try to capture the biometrics until the quality threshold has crossed or the device capture timeout has crossed which is also configurable.
After the timeout has occurred and the captured quality of biometrics is less than the threshold, registration client provides an option to re-try capture of biometrics but for a particular number of times which is also configurable. If the resident has a biometric exception (resident is missing a finger/iris or quality of finger/iris is very poor) the operator can mark that particular biometrics as exception but the operator has to capture the resident's exception photo.
What is the difference between an adult' and an infant' biometric capture?
For an adult, all the configured biometrics can be captured.
For an infant, by default, only the face biometrics is allowed to be captured.
Concept of biometric exception
Permanent or temporary missing / defective fingers or irises can be marked as exception during registration process.
Marked exception finger / iris names are sent as part of rcapture request to SBI.
A photo of resident is captured highlighting his/her biometric exceptions called as Proof of exception (POE).
Biometric exception photo is captured by the biometric face camera device.
Until 1.2.0, POE was collected only as documentType field. From 1.2.0.1, Captured biometric exception photo is stored in the biometric data file (CBEFF xml file).
When a resident visits the registration center to update their demographic or biometric details, the operator captures the updated data as provided by the resident in the registration client. The resident needs to give their UIN and also select the field(s) that needs an update. The image below gives an idea of the update UIN process Flow in the registration client.
There are two situations where a Lost UIN flow is used. I am listing here the situations.
The registrant has lost their Identity details.
The registrant never received his identity due to a wrong address/email/phone
The registrant visits the registration centre to retrieve the same. The operator then captures the biometrics and the demographic details of the individual and processes a request to retrieve the lost UIN. As biometrics play a crucial role in identifying a person's identity, it is mandated to provide the biometrics as a part of the Lost UIN flow. Other details like demographic data, and uploading documents are optional.
As a part of Lost UIN flow, the contact details like the phone number/ e-mail address of the UIN holder can also be updated and stored in the ID Repository based on the value provided for the property uingenerator.lost.packet.allowed.update.fields which is specified in the Registration Processor properties.
If the value already exists for the above mentioned property and once the lost UIN is found, details of the identity of the individual are sent to the newly provided phone number/ e-mail address.
Example: uingenerator.lost.packet.allowed.update.fields= phone,email
For a resident whose UIN is yet not generated, they can get a request intimation to re-provide their details with a RequestId. The same AddtionalInfo RequestId must be provided to the operator during the correction flow.
Note- The above mentioned Registration tasks are completely configurable through UI Specs<>
The operator can preview the data filled and navigate back to the respective tabs in case of corrections.
Once the resident and the operator are satisfied with the data being captured, the operator can proceed to the Authenticate tab and provide his valid credentials to mark the complete of the registration task.
Once the registration process (new registration, UIN update or lost UIN, correction) is completed, the registration client generates an acknowledgement receipt. This receipt contains a QR code of the Registration application ID, captured demographic data in the selected language, photograph of the resident and ranking of each finger from 1 to 10 (1 being the finger with the best quality). This receipt is print friendly and can be used for printing using any printer.
The image below is that of a sample acknowledgement receipt.
The Supervisor has the exclusive authority to approve/reject packets. The supervisor is supposed to manually re-verify the registrations before uploading them to the server. This page enables them to perform this activity.
Steps to approve/reject packets
Click on any of the registrations listed in the left pane. The registration details are displayed on the right pane.
Supervisor needs to manually verify all the details in the right pane.
Supervisor can click Approve/Reject button based on their verification.
To mark the completion of this approval process, they need to click on Authenticate and provide their credentials.
On successful authentication, approved/rejected packets will be removed from here and be seen on the Application Upload page.
All the registrations which are being marked with the RE-REGISTER status is listed here.
On clicking Dashboard, the Registration client dashboard HTML template is rendered. Default dashboard displays information about the operator, Packets and the Sync Activities.
This section has been reserved for the countries to be able to display their live news and updates. This can be implemented as per a country's requirements.
During the training of the Operators, It must be ensured that consent is obtained directly from the resident whose personal information is being collected and processed. There is no technical way to handle this scenario, so the operator training must include this activity as a manual process and emphasize upon strictly following the same.
This guide helps in understanding the pre-registration sample UI implementation. The pre-registration portal can be used in self-service as well as in assisted mode.
In this mode, residents can pre-register themselves by accessing the pre-registration portal. They can login with their email address or phone number and fill up the demographic form, upload relevant documents to book an appointment for themselves and their family/friends. Finally, they would receive an acknowledgment along with a pre-registration ID that can be used at the registration center.
When used in an assisted mode, the operator could be handling the portal helping other residents fill up the details, and creating an application on their behalf. The languages that the operator and the resident understand, may or may not be the same. If we consider a country with linguistic diversity, the possibilities increase. In such cases, the operator might log in with a language that they are familiar with, and also select a language (data capture language) familiar to the resident for filling up the demographic form and other details.
The key steps in this process are:
Login/create a user account
Create an application
Book an appointment
Receive appointment acknowledgement
To create an application, the resident/operator can follow the steps below:
Open the browser and visit the pre-registration portal.
Select the language of your preference from the dropdown.
Enter your valid email address or phone number in the text box.
Select the Captcha field.
Click Send OTP to receive a One Time Password (OTP) on your provided email address or mobile number.
Enter the OTP and click Verify.
Once the OTP is verified, you will see a pop-up for selecting the languages for data entry.
Select the languages and click Submit.
On the Demographic details page, read the Terms and Conditions and select the check box to agree. This agreement is to provide consent for the storage and processing of your personal information.
Click Accept and proceed.
Enter your demographic details, which include Name, Age/DOB, Gender, Residential Status, Address, Mobile Number, Email ID, etc.
You can also change or verify your demographic details in the other selected language.
After you have filled in and verified your demographic details, click Continue.
Note: The mandatory fields/labels have a * mark. Field and button labels, errors, and information messages will be displayed in the user-preferred language selected on the login screen. The fields displayed on this screen are configurable based on the ID schema defined by the country.
UI specs of the Pre-registration module are used to configure the form fields in the Demographic Details and Document Upload functionality pages. These specs are saved as a JSON file with a list of fields.
Select the document (e.g. Passport, Reference Identity Number, etc.) from the document drop-down list.
Click Browse to locate the scanned document on your machine.
Select the file that you want to upload.
When the file is uploaded successfully, the document will appear on the right side. Verify that you have uploaded the correct document.
Repeat the steps above to upload the document(s) for each applicable document category.
When adding an applicant, if a newly added applicant’s Proof of Address (POA) document is the same as that of the existing user’s POA, which has been already uploaded, click the Same As option and select the name of the applicant.
Click Continue to preview your application.
To change the demographic details (Name, Age, etc.), click modify at the top-right corner adjacent to the Demographic details section.
To modify the uploaded documents, click modify at the bottom-right corner adjacent to the Documents Uploaded section and make changes.
To add a new applicant, click Add Applicant. On clicking the Add Applicant option, you will be navigated to the Demographic details page to provide Consent and proceed with providing the required demographic data and uploading documents.
Click Continue.
On Your Applications page, click Create New Application to generate a new application.
Once the application is created, there could be multiple statuses depending on the data filled by the user/resident or the actions performed by them. The user can view all the pre-registration applications created by them in the Dashboard. The different statuses with a brief explanation are mentioned below:
Incomplete
Filled only demographic details
Upload documents and book an appointment
Pending appointment
Filled demographic details and uploaded documents
Book an appointment
Booked
Filled demographic details, uploaded documents, and booked appointment
Visit the registration center on the appointment date and time
Expired
Appointment date has passed
Re-book an appointment
Cancelled
Appointment has been cancelled
Re-book an appointment
The applications are sorted and displayed by the order of creation of the application. The last application created appears first in the list.
If the user visits the registration center and consumes the appointment, then the application will be removed from the list.
If the appointment date has passed, the status changes to "Expired" and is retained on the dashboard for further rebooking/modification as required.
The recommended registration centers are automatically displayed based on your demographic details (Postal Code)
On the Book Appointment page, you can find a registration center through the three options as follows:
Click Nearby centers to view the registration centers based on your geographical location.
Use the search box to find the registration center based on your search criteria.
Click Recommended Centers to view registration centers based on your demographic details. (Postal Code)
Click Continue.
Note: The default display of registration centers will be based on the Postal Code of the user. To modify this setting, please update the location hierarchy in the pre-registration-default.properties file using the property: preregistration.recommended.centers.locCode.
Select your preferred date from the list of available calendar days and the number of available bookings.
The list of available time slots for your selected date is categorized between Morning and Afternoon.
Select your preferred time slot from the list.
Select the particular applicant's name to book an appointment (click + to add the applicant). Note: On clicking the Add Applicant option, you will be navigated to the Demographic Details page to provide Consent and proceed with providing the required demographic data/documents.
Verify the time slot(s) as selected against the applicant's name(s).
Click Continue.
On the confirmation pop-up, click Confirm.
Click OK.
After successful completion of the Pre-registration application, you will receive an acknowledgment on the registered phone number (SMS) or email address as per details provided in the demographic form.
The acknowledgment contains the following information: name, pre-registration ID, age/DOB, mobile number, email ID and registration center details, appointment date, and appointment time)
A QR code containing the pre-registration ID is generated. This QR code can be scanned at the registration center to fetch the details to be used during the registration process.
You can print, download, email, or SMS your acknowledgment.
To print your acknowledgment, click Print.
To download your acknowledgement, click Download PDF.
To add the additional recipient(s) to receive the acknowledgment of your application, follow these steps:
Click Send Email/SMS.
Enter the mobile number and/or enter the email ID.
Click Send to receive the acknowledgment on your provided e-mail address or mobile number.
On Your Applications page, select the check box for the applicable applicant.
Click Book/Modify Appointment to re-book an appointment (on the top right corner)..
The user can select any appointment date available and the appointment slot available
A user cannot re-book the appointment if the appointment booking is less than 48 hours (configurable) from the time of booking
On the Your Applications page, click on the delete icon against the pre-registration application of an applicant, and a pop-up window appears on the screen.
Select the Discard entire application option in the pop-up window.
Click SUBMIT to discard your application.
On Your Applications page, click on the delete icon against the pre-registration application of an applicant, and a pop-up window appears on the screen.
Select Cancel appointment and save the details option in the pop-up window.
Click SUBMIT to cancel an appointment.
Following a successful appointment cancellation, the system unlocks the time slot of the registration center to ensure that someone else can book it.
The registration UI forms are rendered using respective UI specification JSON. This is derived from the ID Schema defined by a country. Here, we will be discussing the properties used in the UI specification of the Registration Client.
In the Registration Client, currently, Registration Tasks(process) forms are configurable using the UI specifications.
Each process has multiple screens and each screen is rendered with one or more fields.
{
"id": "<NEW/UPDATE/LOST/BIOMETRIC_CORRECTION process name as passed in the packet>",
//order in which the process is displayed on the registration client home screen
"order": 1,
"flow": "<NEW/UPDATE/LOST/CORRECTION>",
//Multi-lingual labels displayed based on the logged in language
"label": {
"eng": "Registration",
"ara": "تسجيل",
"fra": "Inscription"
},
//screen details - follows screen spec structure
"screens": [
{}
],
//caption displays on-hover content
"caption": {
"eng": "Registration",
"ara": "تسجيل",
"fra": "Inscription"
},
//icon is the symbol that appears before the process label
"icon": "registration.png",
"isActive": true,
//group names that should be by default selected during UDPATE UIN process
"autoSelectedGroups": [
""
]
}//Order of the screen on the registration page
"order": 1,
"name": "<unique identifier for the screen>",
"label": {
"ara": "شاشة عينة",
"fra": "Exemple d'écran",
"eng": "Sample screen"
},
"caption": {
"ara": "شاشة عينة",
"fra": "Exemple d'écran",
"eng": "Sample screen"
},
//field details - follows field spec structure
"fields": [
{}
],
"layoutTemplate": null,
//displays field to provide pre-reg application ID, data fetched from pre-reg application will be pre-filled in the current registration form
"preRegFetchRequired": true,
//enable below flag to capture additionalInfo request ID , applicable only during correction process
"additionalInfoRequestIdRequired": false,
//show or hide screens
"active": true
}{
"id": "<Unique identifier for the field, must be same as that described in the ID Schema>",
//inputRequired is used to identify if UI input is needed or not
"inputRequired": true,
//type defines the datatype of the field,which must be the same as that is defined in the ID Schema
"type": "<string/simpleType/documentType/biometricsType>",
"controlType": "textbox/fileupload/dropdown/checkbox/button/date/ageDate/html/biometrics",
//minimum- applicable only for date controlType(defined in days)
"minimum": 0,
//maximum- applicable only for date controlType(defined in days)
"maximum": 365,
"description": "<Field description>",
"label": {
"ara": "حقل العينة",
"fra": "Exemple de champ",
"eng": "Sample Field"
},
//fieldType is used to identify if it is a dynamic field
"fieldType": "<default/dynamic>",
//to validate the format should be in upper or lower case
"format": "<lowercase/uppercase/none>",
//list of validators for the field
"validators": [
{
//type of validation engine (currently, only regex is supported)
"type": "regex",
//expression for the validation
"validator": "^([0-9]{10,30})$",
//list of arguments needed for the validator
"arguments": [],
//if null, its applicable for all languages, else validator expression can be provided for each langCode
"langCode": null,
/*error code to be used to display specific error message, if null, generic validation error message is displayed
There error codes must be configured in registration client i18n files*/
"errorCode": "UI_100001"
}
],
//determines sharing and longevity policies applicable as defined in ID Schema
"fieldCategory": "<pvt/evidence/kyc>",
"alignmentGroup": "<fields belonging to same alignment group are placed horizontally next to each other>",
//determines when to display and hide the field(set null if the field has to be displayed always)
"visible": {
"engine": "MVEL",
"expr": "identity.get('ageGroup') == 'INFANT' && (identity.get('introducerRID') == nil || identity.get('introducerRID') == empty)"
},
"contactType": null,
//used to group together the list of fields(only applicable in the Update UIN process)
"group": "<grouping used in update UIN process>",
"groupLabel": {
"eng": "Sample group",
"ara": "مجموعة العينة",
"fra": "Groupe d'échantillons"
},
/*on change of the field value, configured Action will be triggered on other fields
Change action handlers should be implemented in registration client*/
"changeAction": null,
//enable or disable auto-transliteration
"transliterate": false,
/*provide the templateName(applicable only for html controlType fields)
These templates should be configured in templates table*/
"templateName": null,
"fieldLayout": null,
"locationHierarchy": null,
//On any biometric exception, Need to capture exception photo as proof if the below flag is enabled
"exceptionPhotoRequired": true,
/*applicable only for BiometricsType field, defines the list of attributes to be captured
All the supported biometric attributes are listed down for reference*/
"bioAttributes": [
"leftEye",
"rightEye",
"rightIndex",
"rightLittle",
"rightRing",
"rightMiddle",
"leftIndex",
"leftLittle",
"leftRing",
"leftMiddle",
"leftThumb",
"rightThumb",
"face"
],
//capture of above mentioned bioAttributes can be conditionally mandated based on age group
"conditionalBioAttributes": [
{
"ageGroup": "INFANT",
"process": "ALL",
"validationExpr": "face || (leftEye && rightEye)",
"bioAttributes": [
"face",
"leftEye",
"rightEye"
]
}
],
//set true/false to mark the field as mandatory or optional
"required": true,
//if requiredOn is defined, the evaluation result of requiredOn.expr takes the priority over "required" attribute
"requiredOn": [
{
"engine": "MVEL",
"expr": "identity.get('ageGroup') == 'INFANT' && (identity.get('introducerRID') == nil || identity.get('introducerRID') == empty)"
}
],
//used to identify the type of field
"subType": "<document types / applicant / heirarchy level names>"
}{
"id": "BIOMETRIC_CORRECTION",
"order": 4,
"flow": "CORRECTION"
"label": {
"eng": "Biometric correction",
"ara": "التصحيح البيومتري",
"fra": "Correction biométrique"
},
"screens": [
{
"order": 1,
"name": "consentdet",
"label": {
"ara": "موافقة",
"fra": "Consentement",
"eng": "Consent"
},
"caption": {
"ara": "موافقة",
"fra": "Consentement",
"eng": "Consent"
},
"fields": [
{
"id": "consentText",
"inputRequired": true,
"type": "simpleType",
"minimum": 0,
"maximum": 0,
"description": "Consent",
"label": {},
"controlType": "html",
"fieldType": "default",
"format": "none",
"validators": [],
"fieldCategory": "evidence",
"alignmentGroup": null,
"visible": null,
"contactType": null,
"group": "consentText",
"groupLabel": null,
"changeAction": null,
"transliterate": false,
"templateName": "Registration Consent",
"fieldLayout": null,
"locationHierarchy": null,
"conditionalBioAttributes": null,
"required": true,
"bioAttributes": null,
"requiredOn": [],
"subType": "consentText"
},
{
"id": "consent",
"inputRequired": true,
"type": "string",
"minimum": 0,
"maximum": 0,
"description": "consent accepted",
"label": {
"ara": "الاسم الكامل الكامل الكامل",
"fra": "J'ai lu et j'accepte les termes et conditions pour partager mes PII",
"eng": "I have read and accept terms and conditions to share my PII"
},
"controlType": "checkbox",
"fieldType": "default",
"format": "none",
"validators": [],
"fieldCategory": "evidence",
"alignmentGroup": null,
"visible": null,
"contactType": null,
"group": "consent",
"groupLabel": null,
"changeAction": null,
"transliterate": false,
"templateName": null,
"fieldLayout": null,
"locationHierarchy": null,
"conditionalBioAttributes": null,
"required": true,
"bioAttributes": null,
"requiredOn": [],
"subType": "consent"
},
{
"id": "preferredLang",
"inputRequired": true,
"type": "string",
"minimum": 0,
"maximum": 0,
"description": "user preferred Language",
"label": {
"ara": "لغة الإخطار",
"fra": "Langue de notification",
"eng": "Notification Langauge"
},
"controlType": "button",
"fieldType": "dynamic",
"format": "none",
"validators": [],
"fieldCategory": "pvt",
"alignmentGroup": "group1",
"visible": null,
"contactType": null,
"group": "PreferredLanguage",
"groupLabel": null,
"changeAction": null,
"transliterate": false,
"templateName": null,
"fieldLayout": null,
"locationHierarchy": null,
"conditionalBioAttributes": null,
"required": true,
"bioAttributes": null,
"requiredOn": [],
"subType": "preferredLang"
}
],
"layoutTemplate": null,
"preRegFetchRequired": false,
"additionalInfoRequestIdRequired": false,
"active": false
},
{
"order": 2,
"name": "BiometricDetails",
"label": {
"ara": "التفاصيل البيومترية",
"fra": "Détails biométriques",
"eng": "Biometric Details"
},
"caption": {
"ara": "التفاصيل البيومترية",
"fra": "Détails biométriques",
"eng": "Biometric Details"
},
"fields": [
{
"id": "individualBiometrics",
"inputRequired": true,
"type": "biometricsType",
"minimum": 0,
"maximum": 0,
"description": "",
"label": {
"ara": "القياسات الحيوية الفردية",
"fra": "Applicant Biometrics",
"eng": "Applicant Biometrics"
},
"controlType": "biometrics",
"fieldType": "default",
"format": "none",
"validators": [],
"fieldCategory": "pvt",
"alignmentGroup": null,
"visible": null,
"contactType": null,
"group": "Biometrics",
"groupLabel": null,
"changeAction": null,
"transliterate": false,
"templateName": null,
"fieldLayout": null,
"locationHierarchy": null,
"conditionalBioAttributes": [
{
"ageGroup": "INFANT",
"process": "ALL",
"validationExpr": "face",
"bioAttributes": [
"face"
]
}
],
"required": true,
"bioAttributes": [
"leftEye",
"rightEye",
"rightIndex",
"rightLittle",
"rightRing",
"rightMiddle",
"leftIndex",
"leftLittle",
"leftRing",
"leftMiddle",
"leftThumb",
"rightThumb",
"face"
],
"requiredOn": [],
"subType": "applicant"
},
{
"id": "proofOfException",
"inputRequired": false,
"type": "documentType",
"minimum": 0,
"maximum": 0,
"description": "proofOfException",
"label": {
"ara": "إثبات الاستثناء",
"fra": "Exception Proof",
"eng": "Exception Proof"
},
"controlType": "fileupload",
"fieldType": "default",
"format": "none",
"validators": [],
"fieldCategory": "evidence",
"alignmentGroup": null,
"visible": null,
"contactType": null,
"group": "Documents",
"groupLabel": null,
"changeAction": null,
"transliterate": false,
"templateName": null,
"fieldLayout": null,
"locationHierarchy": null,
"conditionalBioAttributes": null,
"required": false,
"bioAttributes": null,
"requiredOn": [],
"subType": "POE"
}
],
"layoutTemplate": null,
"preRegFetchRequired": false,
"additionalInfoRequestIdRequired": true,
"active": false
}
],
"caption": {
"eng": "Biometric correction",
"ara": "التصحيح البيومتري",
"fra": "Correction biométrique"
},
"icon": "UINUpdate.png",
"isActive": true,
"autoSelectedGroups": null
}Add the following in the properties section of IDSchema:
"selectedHandles":
{
"fieldCategory": "none",
"format": "none",
"type": "array",
"items":
{
"type": "string"
},
"fieldType": "default"
},
Example:
"email":
{
"bioAttributes": [],
"validators":
[
{
"langCode": null,
"validator": "^[A-Za-z0-9_\\-]+(\\.[A-Za-z0-9_]+)*@[A-Za-z0-9_-]+(\\.[A-Za-z0-9_]+)*(\\.[a-zA-Z]{2,})$",
"arguments": [],
"type": "regex"
}
],
"fieldCategory": "pvt",
"format": "none",
"type": "string",
"fieldType": "default",
"handle": true
}[
{
"name":"scheduledjobs",
"description":{
"ara":"إعدادات الوظائف المجدولة",
"fra":"Paramètres des travaux planifiés",
"eng":"Scheduled Jobs Settings"
},
"label":{
"ara":"إعدادات الوظائف المجدولة",
"fra":"Paramètres des travaux planifiés",
"eng":"Scheduled Jobs Settings"
},
"fxml":"ScheduledJobsSettings.fxml",
"icon":"scheduledjobs.png",
"order":"1",
"shortcut-icon":"scheduledjobs-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR"
]
},
{
"name":"globalconfigs",
"description":{
"ara":"إعدادات التكوين العامة",
"fra":"Paramètres de configuration globale",
"eng":"Global Config Settings"
},
"label":{
"ara":"إعدادات التكوين العامة",
"fra":"Paramètres de configuration globale",
"eng":"Global Config Settings"
},
"fxml":"GlobalConfigSettings.fxml",
"icon":"globalconfigs.png",
"order":"2",
"shortcut-icon":"globalconfigs-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR"
]
},
{
"name":"devices",
"description":{
"ara":"إعدادات الجهاز",
"fra":"Réglages de l'appareil",
"eng":"Device Settings"
},
"label":{
"ara":"إعدادات الجهاز",
"fra":"Réglages de l'appareil",
"eng":"Device Settings"
},
"fxml":"DeviceSettings.fxml",
"icon":"devices.png",
"order":"3",
"shortcut-icon":"devices-shortcut.png",
"access-control":[
"REGISTRATION_SUPERVISOR",
"REGISTRATION_OFFICER"
]
}
]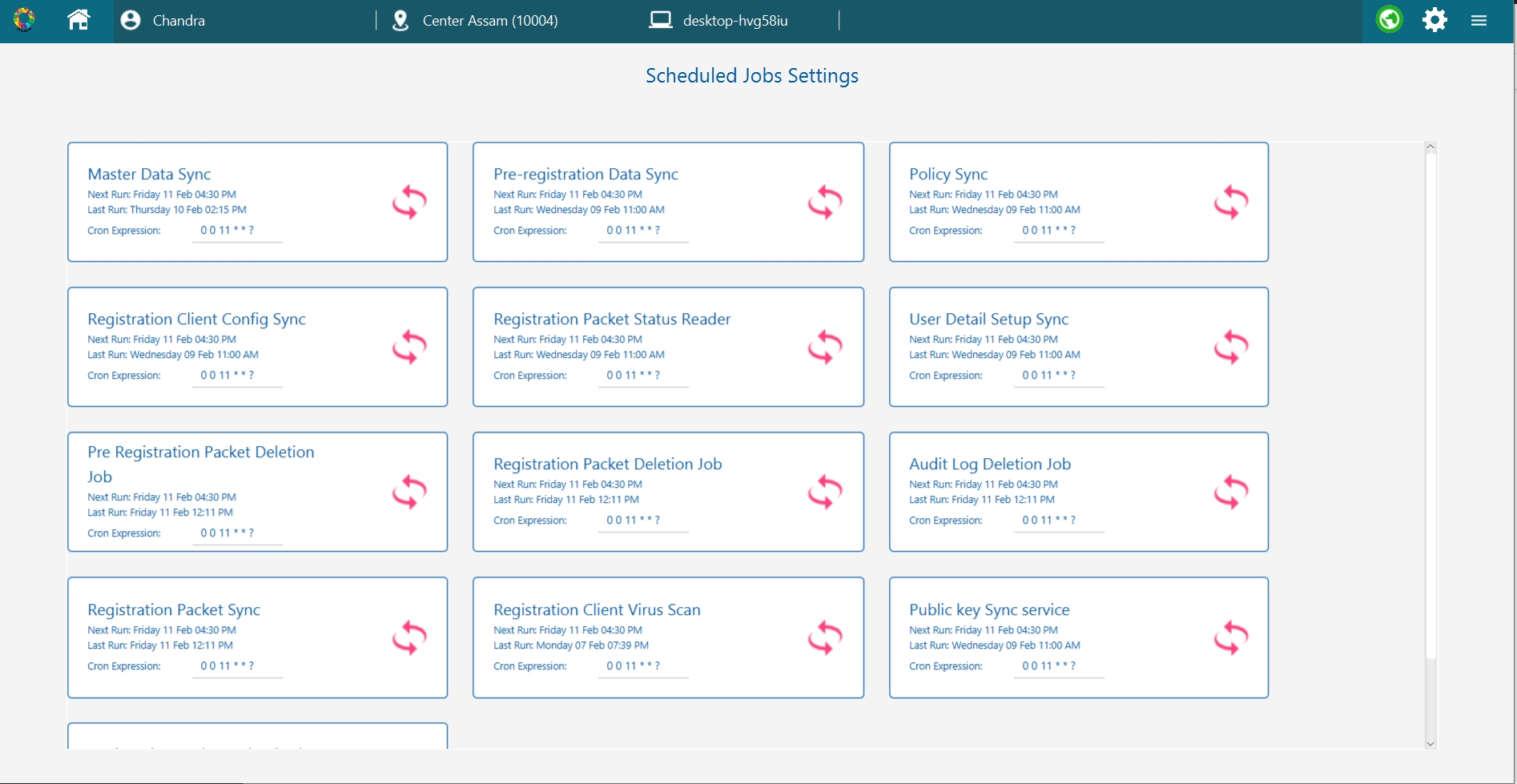
This user guide is designed to provide assistance to Operators and Supervisors in successfully installing, running, and registering applicants to obtain their Unique Identification Numbers (UIN) on tablet devices.
Reliable and consistent Internet connectivity.
Tablets running Android version 10 to 13.
Tablets with a minimum of 4 GB RAM.
The tablets need to be capable of capturing fingerprints, iris, and face (photo) biometrics. Additionally, they should also have the ability to scan documents. However, if the tablets do not support these capabilities, MOCK SBI can be used as an alternative.
Download and install the APK on Android tablet.
Once ARC is installed, long press on the logo to copy the machine details.
On the Admin Portal, using admin credentials, login and perform the following to add the device:
Go to Resources/Machine and click on Create machine
Add a new machine and enter the machine details:
Add the specs as Mobile
Map it to a Zone and Center
Add the Machine spec ID as Mobile
Enter Device name
Enter Public Key
Enter Sign Public Key
Create the role Default in KeyCloak with all the other roles.
Create the Operator’s user account in KeyCloak set the password and assign the role as Default, REGISTRATION_OFFICER, Registration Operator, REGISTRATION_SUPERVISOR
Login into Admin Portal to perform the following and add the user:
After login into the Admin Portal, go to User Zone Mapping and add the zone for the user and activate it.
Go to User Center Mapping and add the center for the user and activate it.
The user should relaunch the ARC and log in using their valid credentials. Additionally, the operator has the option to select their preferred display language.
Upon successful login, the user will be directed to the Home page, which includes the following options:
New Registration
Operational Tasks
Dashboard
Settings (Future scope)
To begin the Registration process, the Operator is required to follow the steps outlined below.
Click on New Registration card.
Select the language to be used for data entry, which will be used to collect the resident's information. There will be a default language for data entry.
Choose the language in which the notification will be sent to the resident. Click Submit to proceed.
The operator will be redirected to the Consent page, where the resident must agree to the terms and conditions to proceed.
After accepting consent, the Operator will need to fill out the demographic data of the resident, including their name, age, date of birth, and address. Once all mandatory fields are completed, the Continue button will be enabled.
Upon clicking the Continue button, the Operator will be navigated to the Document upload page where they will need to:
Select the type of document (e.g. proof of identity, proof of address) from the drop-down menu.
Enter the Reference Number of the document.
Upload the document by clicking on the Scan button to open the camera. The Operator can take a picture of the document and then choose from the following actions:
Cancel: Clicking on the "Cross" icon will remove the captured image and return the Operator to the previous screen.
Crop: The Operator can drag from the four corners of the captured image to crop it as needed.
Save: Clicking on the "Save" button will save the captured image and return the Operator to the previous Document Upload page.
Retake: Clicking on the "Retake" button will remove the captured image, reopen the camera, and allow the Operator to take a new photo.
After ensuring all required information has been accurately entered into the Document Upload screen, the Operator can proceed by clicking on the Continue button to access the Biometric Capture page. Here, the Operator can capture the biometric data of the Resident, including a face photo, fingerprint, and iris scan.
To capture the face photo, the Operator should click on the Scan button to activate the camera and take a picture.
The image quality will be displayed on the screen and must meet a certain threshold to be considered acceptable.
The Operator has three attempts to capture the biometric image.
It is important to note that no exceptions can be made for the face photo biometric capture process.
To capture biometric data, the Operator should click on the Scan button.
This will allow the Operator to capture the biometric information.
Once the data is captured, the image quality will be displayed on the screen and must meet the acceptable threshold limit.
Note: Three attempts are provided to capture the biometric data.
If a thumb is missing or experiencing difficulties that prevent its fingerprint from being captured, the Operator is authorized to indicate an exception. To mark an exception, the operator must select the affected thumb and specify the type of exception as either Temporary or Permanent. Additionally, the operator may include any relevant additional comments.
To initiate the Iris scan, the Operator is required to click on the Scan button.
This action will allow the Operator to capture the Iris image.
Once the Iris has been successfully captured, the quality of the image will be displayed on the screen.
The quality score needs to meet the established threshold limit.
The Operator has three opportunities to capture the biometric data.
If one or both of the Irises are not detected or encounter issues that prevent successful capture, the Operator has the option to mark an exception. To do so, the Operator must identify the specific Iris that is problematic and indicate the type of exception- either Temporary or Permanent. Additionally, the Operator may provide any relevant comments.
After all the biometric data has been properly captured or any exceptions have been noted, the Continue button will be activated. The Operator can then proceed by clicking on the Continue button, which will redirect them to the Preview page. The Preview page will display the following information:
Application ID
Timestamp of Registration
Demographic data collected
Documents submitted
Biometric data recorded
From the Preview page, the Operator can navigate back to previous screens to make any necessary adjustments to the entered or captured data. Once the Operator has verified the accuracy of the entered data, they can proceed by clicking on the Continue button, which will direct them to the Operator Authentication page.
On the Operator Authentication page, operators are required to input their credentials (username and password) that were used during the login process.
Upon successful verification of the credentials, the packet will be uploaded to the server and the operator will be redirected to the Acknowledgment screen. This screen includes the following information:
Application ID
Timestamp of Registration
Demographic data captured
Documents uploaded
Biometric data captured
Print option
QR code for the Application ID
Option to initiate a new registration process.
Pending Approval:
Upon successful verification of the credentials, the acknowledgment will be displayed, and the Application will be moved to the “Pending Approval” section. This feature will only be available for the User who has a Supervisor’s role assigned to him.
Once the packet is created by the Operator, as an additional check, the Supervisor will have to go through each application to make sure the details filled are coherent.
Step 1: The user goes to the “Pending Approval” section from the Operational Tasks section. The user will be taken to the page where they can see the list of all the Applications created by the Operator. All of these Applications will be “Pending”.
Step 2: The Supervisor then clicks on the Application ID one by one. At this stage, the Supervisor can either Approve the Application or he can Reject it. If the Supervisor decides to reject it, they also will have to mandatorily mention the reason for rejection.
Step 3: Once the Application has been Approved or Rejected, the Supervisor will have to authenticate himself by clicking on the “Submit” button and thereby entering their Username and Password. The User can also bulk submit the Applications. The only pre-requisite is that the packet has to be in Approved or Rejected status (pending Applications cannot be submitted for uploading). Once they have successfully authenticated, the Application will be removed from the “Pending Approval” section and will be moved to the “Manage Application” Section.
Step 4: Once the Application is either Approved or Rejected by the Supervisor and is submitted, those packets can be uploaded to the server from the “Manage Application” section or can be exported to their local device storage.
Manual Application upload/export
Once the Application is either Approved or Rejected by the Supervisor, those packets can be uploaded to the server from the “Manage Application” section.
Step 1: The user selects the packets they want to upload (bulk upload can also be done). Once selected, the user clicks on the “Upload” button, after which the packet syncs and gets uploaded if there is internet connectivity.
In case of a lack of internet connectivity, the User can also export the packet to their local device storage. They can also bulk export the packets by choosing the Applications and clicking on the Export button.
On choosing to upload, the packet is uploaded to the Registration Processor. Once the packet has been successfully processed, a unique identification number (UIN) is generated.
Print- The operator can click on this option to obtain a physical copy of the acknowledgment.
New Registration- The operator can initiate another registration by clicking on this option.
In summary, the user (Operator/ Supervisor) can follow the aforementioned steps to register an individual by capturing demographic data, documents, and biometric data to generate their UIN.
Operator Onboarding: To begin the Onboarding process, the Operator is required to follow the steps outlined below. The operator, to log in to the Android Registration Client, will have to onboard himself. This functionality will be available on first-time online login only.
a. On logging in for the first time, the Operator will be taken to the screen where they will have the following two options:
Get onboard: This flow is present for the system to verify the Operator’s biometrics with their registered biometrics. This is to enable local deduplication. To get onboarded the operator must not be assigned "default" role.
Skip to home: This flow is to dodge “Operator’s Onboarding”. If the user selects this, they will be taken to the “Homepage” after which the user can get started with Resident registration. One of the prerequisites of this flow is to have the “Default” role mapped to the center.
Steps to Onboard Operator’s Biometrics:
a. The user will be taken to the Biometrics Capture Homepage where he will be able to see all the below biometrics:
Face capture
Iris capture
Left-hand finger capture
Right-hand finger capture
Thumb capture
b. The user will then have to capture all the above-listed biometrics one by one. c. Steps to capture the biometrics are given here. d. Once all the biometrics are duly captured, the below acknowledgment message will be displayed on the screen.
Dashboard: The Operator can access the dashboard where he can view the following:
Packets created: This will show the total number of packets created from the time the Android Registration Client was installed.
Packets Synced: This will show the total number of packets synced from the time the Android Registration Client was installed.
Packets Uploaded: This will show the total number of packets uploaded from the time the Android Registration Client was installed.
User details:
User ID: This will show the list of User IDs of the Users mapped to the device.
Username: This will show the list of usernames of the Users mapped to the device.
Status: This will show the status of Users mapped to the device. This can take values such as onboarded, active, inactive, etc.
In summary, the aforementioned steps can be followed by the user (Operator/ Supervisor) to onboard themselves, update their biometrics, or view the Dashboard.
Update UIN
In a scenario where the Resident wants to update their data, they can do so by letting the Operator know their UIN along with the data that needs to be updated. Residents can update their demographic details, documents, and biometrics using this feature.
Step 1: Go to “Update UIN” from the Homepage
Step 2: Enter the UIN of the Resident and choose the data to be updated.
Step 3: Enter the data that the Resident wants to update. It could demographic data, documents, and biometrics.
Step 4: Once all the required data is filled, the User will be taken to the Preview screen (data can still be modified) and then to the Acknowledgment screen (data cannot be updated hereafter).
Step 5: The user will then have to authenticate himself using his Username and Password. Once the authentication is successful, the packet will be uploaded to the server.
Logout: Using this feature, once the user is done with their registration and other activities, they can logout. If no background tasks are running, the user will be immediately logged out. If there are tasks (like sync) running in the background, the user will be notified about the same. From here if the User wants to cancel the logout, the background activities will keep running where whereas if the user chooses to logout, they will be logged out and the background activities will be terminated.
This feature will be used by the operators to update their biometrics. They can follow the below steps for the same:
a. The user will be taken to the Biometrics Capture Homepage where he will be able to see all the below biometrics:
Face capture
Iris capture
Left-hand finger capture
Right-hand finger capture
Thumb capture
b. The user will then have to capture all the above-listed biometrics one by one.
c. Steps to capture the biometrics are given here.
d. Once all the biometrics are duly captured, the below acknowledgment message will be displayed on the screen.
Assumption: The Handles feature is enabled, and the email ID is designated as a Handle during registration.
Scenarios: A resident attempts to log into the Resident Portal using their Handle (i.e., email ID).
Step 1: Open the Resident Portal and navigate to "UIN Services."
Step 2: The resident will be taken to the eSignet login page.
Step 3: Choose the option to “Login using OTP”
Step 4: Enter the attributes marked as Handle (email ID in this case) and click on “Get OTP”. OTP will be sent to registered email ID and/or mobile number
Step 5: Enter the OTP received over the registered email ID and/or mobile number
Step 6: Select/De-select the Claims based on preference.
And click on the “Allow” button.
Step 7: You have now successfully authenticated and logged into Resident Portal via eSignet using handles (email ID in this case).
In a scenario where the Operator has forgotten their password, this feature enables the Operator to set a new password to be able to login using the new password and continue with registration tasks.
Step 1: Run Android Registration Client on your system to land on the Login page.
Step 2: Click on Forgot Password option, You will then be redirected to the keycloak Login page.
Step 3: Click on Forgot Password option on the Keycloak login page.
Step 4: Enter your Keycloak Username and click on Submit.
Step 5: You will then receive an email over registered email Id to reset the password. This email contains a link to set a new password.
Step 6: On clicking on the link to set a new password, you (Operator) will be taken to the keycloak page where you can enter the new password. On successfully entering the password twice, the password will be changed. This password can now be used to log into Android Registration Client (when in online mode). In offline mode, the User will still be able to login using the older password until the system goes online and syncs atleast once after resetting the password.
This feature enables the Operator to scan the QR code of the AID (Application ID) QR code generated during pre-registration. On successful scan, the Operator will be able to fetch the pre-registration data and pre-fill the registration form with the available data.
Step 1: Log into Android Registration Client, start new registration to land onto the "Demographic Details" Page.
Step 2: On the "Demographic Details" page, click on the scan button next to "Fetch Data" option. On clicking on the scan button, camera will open up.
Step 3: You can then scan the QR code generated during Applicantʼs pre-registration.
Step 4: On scanning, the Application ID field will be pre-filled with the AID. Along with that, other details, as filled during pre-registration, like Name, age, gender, documents etc. will also be auto filled.
The pre-filled data can also be edited based on the your (Operator) or Residentʼs preference.
In a scenario where a Resident has lost their UIN, they can go to a registration center to retrieve their lost UIN. Below are the steps for the same:
Step 1: You (Operator) have to Launch Android Registration Client and login using valid credentials.
Step 2: Click on "Lost UIN" option on the home page.
Step 3: You (Operator) will then have to select the Data Entry Language and the Preferred Language of Communication.
Step 4 You can then ask and inform the Residents about the Consent and click on "Informed" button.
Step 5 You can fill the demographic details of the Resident. This is an optional step.
Step 6 You will have to capture all the biometrics of the Resident. This is a mandatory step.
Step 7: Once you (Operator) have duly captured the biometrics of the Resident, you can then proceed by clicking on the Continue button, which will redirect you to the Preview page. The Preview page will display the following information:
Application ID
Timestamp of Registration
Demographic data collected (if any) Biometric data recorded
From the Preview page, you (Operator) have the the ability to navigate back to previous screens in order to make any necessary adjustments to the entered or captured data. Once you have verified the accuracy of the entered data, you can proceed by clicking on the Continue button, which will direct them to the Operator Authentication page.
Step 8: On the Operator Authentication page, you (operator) are required to input your credentials (username and password) that were used during the login process.
Step 9: Once that is done successfully, the packet is uploaded to the server and you (operator) will be redirected to the Acknowledgment screen. This screen includes the following information:
Application ID
Timestamp of Registration
Demographic data captured (if any)
Biometric data captured
Print option
QR code for the Application ID
Option to go to the Homepage
In a scenario where the you (Operator) wish to set a new password, you can set a new password using this feature post which you will be able to login using the new password and continue with registration tasks.
Step 1: Launch Android Registration Client and login using valid credentials.
Step 2: Click on the "Profile" Icon on the Home page
Step 3: On the Profile page, click on the "Reset Password" option.
Step 4: On clicking on the "Reset Password" option, You will be redirected to the Keycloak Login page.
Step 5: You can then login using Keycloak credentials.
Step 6: Once you have logged in, you will be taken to the Password section where you can set a New Password.
Once the password is reset, new password can be used to log into Android Registration Client (when in online mode).
Note: In offline mode, you will still be able to login using the older password until the system goes online and syncs atleast once after resetting the password.
The Auto Logout feature enhances application security by automatically logging out users after a defined period of inactivity. This helps protect sensitive data and ensures that only authorized users maintain access to the Android Registration Client.
How it works:
The system continuously monitors user activity, such as touches or navigation events within the application. When inactivity exceeds a configurable threshold, the following sequence occurs:
Step 1: A warning message is displayed on the screen after the idle period, notifying the user of the impending automatic logout. The warning dialog shows a countdown timer indicating the remaining time before automatic logout occurs.
Step 2: During the warning period, the user has two options:
Click the "STAY LOGGED IN" button to dismiss the warning and continue the session normally.
Click the "LOG OUT" button to immediately log out of the application.
Step 3: If the user remains inactive and does not interact with the warning dialog (by clicking either button) during the warning period, the application automatically logs them out.
Step 4: Upon automatic logout, the feature securely clears all authentication states and session data, ensuring that no sensitive information remains accessible.
Note: The inactivity threshold and warning period duration are configurable settings that can be adjusted based on security requirements and operational needs.
The Biometric Correction feature enables operators to update and correct the biometric information of applicants, ensuring accurate association with their Unique Identification Number (UIN). When a resident's biometric data does not meet the required threshold during the registration process, the system generates an Additional Info Request ID. This ID is sent to the resident via notification, allowing them to schedule an appointment and update their biometric information at a registration centre.
Step 1: Create a packet with a lower biometric threshold.
Step 2: You receive a notification with additional Info request ID.
Step 3: Select the biometric correction feature from Home page.
Step 4: Add an additional request ID and give valid biometrics.
Step 5: Preview for the given details.
Step 6: Authenticate the operator.
Step 7: You will receive an acknowledgment of your application.
Step 8: Approve the packet from the pending approvals.
Step 9: Upload the packet.
This is the process to create a biometric correction packet. After this, the data will be updated, and a UIN will be generated.
This feature enables the Operator to automatically capture GPS location (latitude and longitude) when creating any packet through Android Registration Client. The GPS location is captured at the point of packet creation and attached as metadata to the packet, ensuring that the Operator's location is tracked for audit and verification purposes.
Step 1: Log into Android Registration Client using your login credentials.
Step 2: Start creating a packet for any of the following: New Registration, Lost UIN, Update UIN, or Applicant Correction.
Step 3: When you initiate packet creation, the system will automatically capture your current GPS coordinates (latitude and longitude) from the device. If this is the first time accessing location, you will be prompted to grant location permission. You can choose between "Precise" or "Approximate" location accuracy and select the permission duration (While using the app, Only this time, or Don't allow). This happens in the background without any additional action required from you once permission is granted.
Step 4: The captured GPS location will be attached to the packet as metadata when you submit the packet. The metadata includes latitude, longitude, and timestamp of when the location was captured.
The Manage Scheduled Jobs feature allows admin and supervisor users to view, manage, and trigger scheduled sync/batch jobs directly from the Scheduled Jobs Settings screen within the Android Registration Client.
This feature provides visibility into system jobs (e.g., syncs, cleanup, updates) and enables supervisors to modify their scheduling configuration (cron expressions) on the local device.
This feature is useful to provide a centralised interface for administrators to monitor, update, and manually trigger scheduled jobs to ensure smooth and timely system operations.
The Scheduled Jobs Settings screen displays a list or grid of all configured jobs.
Each job entry includes:
Job Name (e.g., Registration Packet Deletion Job)
Next Run Time (calculated from cron expression)
Last Run Time (from job execution logs)
Cron Expression (editable field for supervisors)
Manual Trigger Button (Run Now)
Each job's schedule is defined using a CRON expression.
Steps to find the Scheduled jobs feature:
Step 1: Click the settings button on the home page.
Step 2: It will redirect to the settings page as referred in the image below. The first tab is the scheduled job, here you can access.
This feature enables authorized users (Supervisors) to view and manage global configurations in a single Global Config Settings screen. The feature displays server values fetched from masterdata and allows supervisors to override these values locally on the device. Local configuration changes apply only to the current device and do not affect server-side configurations or other devices.
Step 1: Log into Android Registration Client using your login credentials (Supervisor role).
Step 2: From the home page, click on the "Settings" button. The Settings screen will display with various options.
Step 3: On the Settings screen, click on the "Global Configuration Settings" tab. On clicking, the Global Config Settings page will open and display all configurations with their server values and local values.
Step 4: On the Global Config Settings page, you will see a table with three columns: Key, Server Value, and Local Value. The Server Value column shows the value set from the server (read-only). The Local Value column shows the current local value for that configuration key.
For configurations listed in the permitted configuration keys list, you can edit the Local Value by clicking on the Local Value field and entering the new value.
Step 5: Once you have made changes to one or more Local Values, click on the "Submit" button. On clicking Submit, a confirmation dialog will appear showing the number of configurations to be updated.
Step 6: Click "Confirm" in the dialog to save the changes. The system will save the configuration changes, display a success message, and automatically restart the app to apply the changes.
The updated Local Values will apply only to the current device where the Android Registration Client is running. The Server Value will remain unchanged and unaffected by local edits.
This feature enables authorized users (Supervisors and Officers) to view and monitor all devices/peripherals connected to the Android Registration Client tablet. On opening the Device Settings page, the system will automatically scan for connected devices and display device information including device name, device ID, and connection status.
Step 1: Log into Android Registration Client using your login credentials (Supervisor or Officer role).
Step 2: From the home page, click on the "Settings" button. The Settings screen will display with various options.
Step 3: On the Settings screen, click on the "Device Settings" tab. On clicking, the Device Settings page will open and automatically scan for connected devices.
On scanning, the connected devices will be displayed in a grid layout. For each device, you will see the Device ID, Device Name, and Connection Status.
If no devices are detected, you can click on the "Scan Now" button to manually trigger a device scan. The device list will refresh automatically based on scan results.
Tag: 169 (identity-data)
Data Item: JSON Object
Semantics: Identity Data of a Person in QR-Code
Point of Contact: Resham Chugani ()
IANA Registration: (Search for: 169)
Version: 1.1.0
This document specifies an updated version of the generic data structure and encoding mechanism for storing the Identity Data of a registered person using any ID platform. It also provides a transport encoding mechanism in a machine-readable optical format (QR).
Once a person is registered in an identity system, their data serves as the foundation for identification, granting them access to social benefits and government services. The level of assurance in this identification process varies depending on the authentication methods employed. Low assurance is achieved through basic identifiers like ID numbers, demographic data, passwords, or PINs. Conversely, higher assurance levels are attained through one-time passwords (OTP) and biometrics.
Among these methods, biometric-based authentication, such as facial authentication, offers the highest level of assurance as it assures the presence of the individual. While this is effective for online systems & personal phones where verification is conducted on a server or a personal device; offline authentication presents challenges in maintaining a similarly high level of assurance. The offline authentication mechanism should work for people with no phone.
For instance, in a cross-border scenario remote areas often face significant internet connectivity issues. Even when internet access is available, server reliability may be inconsistent. In such circumstances, scanning a QR code containing the person's facial photograph and identity information, alongside assurance that the data is country-signed, provides an additional layer of security and affirmation for the countries involved.
Please note: The trust layers required to sync the country's key are beyond the scope of this document. We assume the app scanning the QR code already has the country's key to verify.
To tackle the challenge above, we propose a standard CBOR-based QR Code that involves embedding a low-resolution image of the person with a minimal demographic dataset within the QR code. This QR code would be digitally signed by the ID authorities (Issuer) and then printed on a physical card. Subsequently, the signed data within the QR code can be utilized for facial authentication. However, it's essential to recognize that QR codes have limitations regarding size. We suggest leveraging CBOR Web Token (CWT) with ED25519/ECC keys to generate a smaller signature and more condensed data.
Claim 169 represents a JSON Object that includes the below table as ID attributes. You can find an illustration of the ID structure contained within Claim 169, where:
Note:
All the fields here are optional.
The issuer of IDClaim169 is expected to host the JWKS file at the standard .well-known URL. This allows relying parties to verify the signature of the issued IDClaim169.
Please ensure to review the stated below.
Image
Template
Sound
Prepare Identity Data: Start with the sample JSON identity data provided for conversion into Claim 169 format.
Convert to Claim 169 Format
Transform the JSON data into the required Claim 169 structure.
Refer to the sample converted data for guidance.
Generate CWT Data
Use the Claim 169–formatted data to create the CBOR Web Token (CWT) for QR code generation.
Compress the CWT
Apply zlib compression to the generated CWT data.
Encode to Base45 and Generate QR Code
Encode the compressed CWT using Base45.
Use this encoded string to generate the final QR code.
TODO:
Current map structure is in plain text and its not the recommended way to handle privacy. Adoption of SD-JWT or equivalent can be considered.
CWT MUST be signed, create a COSE_Sign/COSE_Sign1 object using the Message as the COSE_Sign/COSE_Sign1 Payload; all steps specified in for creating a COSE_Sign/COSE_Sign1 object MUST be followed.
If the CWT is a COSE_Encrypt/COSE_Encrypt0 object,create a COSE_Encrypt/COSE_Encrypt0 using the Message as the plaintext for the COSE_Encrypt/COSE_Encrypt0 object; all steps specified in for creating a COSE_Encrypt/COSE_Encrypt0 object MUST be followed.
To verify the claims the CWT is a COSE_Sign/COSE_Sign1, follow the steps specified in Section 4 of ("Signing Objects") for validating a COSE_Sign/COSE_Sign1 object. Let the Message be the COSE_Sign/COSE_Sign1 payload. Once signature is valid we SHOULD validate the public key against a preconfigured key. In case encrypted Else, if the CWT is a COSE_Encrypt/COSE_Encrypt0 object, follow the steps specified in Section 5 of [RFC8152] ("Encryption Objects") for validating a COSE_Encrypt/COSE_Encrypt0 object. Let the Message be the resulting plaintext.
The security of the CWT relies upon on the protections offered by COSE. Unless the claims in a CWT are protected, an adversary can modify, add, or remove claims.
Since the claims conveyed in a CWT is used to make identity claim decisions, it is not only important to protect the CWT but also to ensure that the recipient can authenticate the party that assembled the claims and created the CWT. Without trust of the recipient in the party that created the CWT, no sensible identity verification can be made. Furthermore, the creator of the CWT needs to carefully evaluate each claim value prior to including it in the CWT so that the recipient can be assured of the validity of the information provided.
Syntactically, the signing and encryption operations for Nested CWTs may be applied in any order; however, if encryption is necessary, producers normally should sign the message and then encrypt the result (thus encrypting the signature). This prevents attacks in which the signature is stripped, leaving just an encrypted message, as well as providing privacy for the signer. Furthermore, signatures over encrypted text are not considered valid in many jurisdictions.
Claim Name: identity-data Claim Description: Registering the claim for storing identity data of a person, which could be Personally Identifiable Data (PII) mostly used in Foundational/National ID for cross-border interoperability. Claim Key: 169 Claim Value Type(s): map Change Controller: MOSIP Specification Document(s): ,
This work is the result of the dedicated efforts of contributors who recognize the critical importance of interoperability and a consistent QR code specification. The revised version has been shaped significantly by the input of our working group committee, comprising members from the following organizations: GetGroup, PWC and Tech 5.
We extend our gratitude to the committee members for their invaluable time and insights throughout the evaluation phase.
GetGroup: Aiman Tarek
PWC: Chaitanya Giri
Tech 5: Bejoy Ak, Nelson Branco, Rahul Parthe
MOSIP: Harini Sampathkumar, Janardhan BS, Mahammed Taheer, Ramesh Narayanan, Resham Chugani, Reeba Thomas, Sanchi Singh, Sasikumar Ganesan, Sreenadh S, Swati Goel, Vishwanath V
Mahammed Taheer ()
Resham Chugani ()
Rounak Nayak ()
Sasikumar G ()
Sreenadh S ()
1
tstr
ID
Unique ID to indicate the PII data
2
tstr
Version
Version of the ID data
3
tstr
Language
Language used in other attributes: Use the three-letter ISO 639-3 language code
4
tstr
Full Name
Full name of the person
5
tstr
First Name
First name of the person
6
tstr
Middle Name
Middle name of the person
7
tstr
Last Name
Last name of the person
8
tstr
Date of Birth
Date of birth in YYYYMMDD format
9
int
Gender
Gender with the following values 1 - Male, 2 - Female, 3 - Others
10
tstr
Address
Address of the person, separator character \n
11
tstr
Email ID
Email id of the person
12
tstr
Phone Number
Contact number of the person: Use E.123 international notation
13
tstr
Nationality
Nationality of the person: Use the two-letter ISO 3166-2 country code or three-letter ISO 3166-1 alpha-3 country code
14
int
Marital Status
Marital status - Can contain the following values 1 - Unmarried, 2 - Married, 3 - Divorced
15
tstr
Guardian
Name/id of the entity playing the role of a guardian, such as a mother, father, spouse, sister, legal guardian etc.
16
tstr
Binary Image
Binary image of the person's photograph
17
int
Binary Image Format
Binary image format. Can contain the following values 1 - JPEG, 2 - JPEG2, 3 - AVIF, 4 - WEBP
18
[int]
Best Quality Fingers
An unsigned 8-bit number encoding the hand position of the finger. It must be in the range 0-10, where 0 represents "Unknown", 1-5 represents right thumb to little finger, and 6-10 represents left thumb to little finger in sequence
19.. 49
Unassigned
For future - For Demographic Data attributes
50
[Biometrics]
Right Thumb
Person's Right Thumb biometrics
51
[Biometrics]
Right Pointer Finger
Person's Right Pointer Finger biometrics
52
[Biometrics]
Right Middle Finger
Person's Right Middle Finger biometrics
53
[Biometrics]
Right Ring Finger
Person's Right Ring Finger biometrics
54
[Biometrics]
Right Little Finger
Person's Right Little Finger biometrics
55
[Biometrics]
Left Thumb
Person's Left Thumb biometrics
56
[Biometrics]
Left Pointer Finger
Person's Left Pointer Finger biometrics
57
[Biometrics]
Left Middle Finger
Person's Left Middle Finger biometrics
58
[Biometrics]
Left Ring Finger
Person's Left Ring Finger biometrics
59
[Biometrics]
Left Little Finger
Person's Left Little Finger biometrics
60
[Biometrics]
Right Iris
Person's Right Iris biometrics
61
[Biometrics]
Left Iris
Person's Left Iris biometrics
62
[Biometrics]
Face
Person's Face biometrics
63
[Biometrics]
Right Palm Print
Person's Right Palm Print biometrics
64
[Biometrics]
Left Palm Print
Person's Left Palm Print biometrics
65
[Biometrics]
Voice
Person's Voice biometrics
66.. 74
Unassigned
For future - For Biometrics Data attributes
75.. 99
Unassigned
For future - For any other data
0
bstr
Data
Biometrics binary data
1
int
Optional biometrics data format
2
int
Optional biometrics data sub format
3
tstr
Data issuer
Optional biometric data issuer
0
Image
1
Template
2
Sound
3
Bio hash
0
PNG
1
JPEG
2
JPEG2000
3
AVIF
4
WEBP
5
TIFF
6
WSQ
100..200
Vendor specific
0
Fingerprint Template ANSI 378
1
Fingerprint Template ISO 19794-2
2
Fingerprint Template NIST
100..200
Vendor specific
0
WAV
1
MP3
1: www.mosip.io # iss
4: 1787912445 # exp
5: 1756376445 # nbf
6: 1756376445 # iat
169: # identity-data
1: 3918592438 # ID
2: 1.0 # Version
3: eng # Language
4: Janardhan BS # Full name
8: 19880102 # Date of birth
9: 1 # Gender: Male
10: New House, Near Metro Line, Bengaluru, KA # Address
11: [email protected] # Email ID
12: "+919876543210" # Phone number
13: IN # Nationality
14: 2 # Marital status: Married
16: 03CBABDF83D068ACB5DE65B3CDF25E0036F2C54(...)E54D23D8EC7DC9BB9F69FD7B7B23383B64F22E25F # Binary image
17: 2 # Binary image format: JPEG
18: [1, 2] # Best quality fingers
50: # Right Thumb Biometrics
# Right Thumb image
- 0: 03CBA(...)0378C58 # Data
1: 0 # Image
2: 1 # JPEG
# Right Thumb template
- 0: 03CBA(...)0378C58 # Data
1: 1 # Template
2: 100 # Vendor specific
3: VendorA # Biometric data issuer
51: # Right Pointer Finger Biometrics
# Right Pointer Finger image
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Image
2: 6 # WSQ
3: VendorA # Biometric data issuer
# Right Pointer Finger template
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Template
2: 1 # Fingerprint Template ISO 19794-2
3: VendorA # Biometric data issuer
58: # Left Ring Finger Biometrics
# Left Ring Finger image
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Image
2: 6 # WSQ
3: VendorA # Biometric data issuer
# Left Ring Finger template
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Template
2: 1 # Fingerprint Template ISO 19794-2
3: VendorA # Biometric data issuer
60: # Right Iris Biometrics
# Right Iris image
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Image
2: 6 # WSQ
3: VendorX # Biometric data issuer
# Right Iris image
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Image
2: 6 # WSQ
3: VendorY # Biometric data issuer
61: # Left Iris Biometrics
# Left Iris template
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Template
2: 100 # Vendor specific
3: VendorX # Biometric data issuer
# Left Iris image
- 0: 36F2C546(...)CB90378C58 # Data
1: 1 # Template
2: 100 # Vendor specific
3: VendorY # Biometric data issuer
65: # Voice Biometrics
# Voice sound
- 0: 03CBA(...)0378C58 # Data
1: 2 # Sound
2: 1 # MP3
# Voice template
- 0: 03CBA(...)0378C58 # Data
1: 1 # Template
2: 100 # Vendor specific
3: VendorZ # Biometric data issuer{
"id": "3918592438",
"fullName": "Janardhan BS",
"dob": "1984-04-18",
"gender": "1",
"address": "New House, Near Metro Line, Bengaluru, KA",
"email": "[email protected]",
"phone": "+919876543210",
"nationality": "IN",
"face": {
"data": "52494646dc0100005745425056503820d0010000b00d009d012a400040003e913c9b4925
a322a12a1ccae8b01209690013e295b2585d5ee72395f7fe4a35103d1894a549b58a4febe751ae9a3
d00cb96f016fc35075f892786b3bcce1deffb2b3e55e3598b7d4913c80a237f1d9e51be7f271cc971
d63fda0c2c3c34b27a574ec1bbd7752969c56c8c0000fefeffce44d1e6b7ad2535538b4cc7a3cf016
f5b7d160c4e7202269bc041f0609efdf8e687702cdd6bd64e90b2931c9210f095f3c3bef00a954bfe
f4e70c76948b9eedf20e5be9e885edbcceada8f6fbdb9037490fa2eecaeaa62de8123028505f9f2eb
2f781fdfc9b55ff127f12cb657cdc5927866e650426e3032500af838514711241395bfb130fda3c29
d836527eeb82d92121b5a6f3b951d4ecc51ae1566c58266227b0f02ced0050fe35e0e42a33026a2c4
4c581fc65ddd135b6a7e5bc888ef852f6c477ccd817b850b90fa3565e11b61e7fe46f965abe210d09
7ef03eaaf028c4ff9dff5f55ad472464b4920a5958b8c98ef0e0029160f20a8f4d1a02ad3b5ad0c43
c0b03dc549576cafb6c3d6c36f1014c57d94f6985f8a328dc7aef8df3507041dc440e99fe9acd90cd
3ede4381d5b3d64064bce4bb8d05113fd901b158698312bdf8a21049288d6006a2c944dae7bc3e240
00000",
"dataFormat": "image",
"dataSubFormat": "png"
}
}{
1: "3918592438",
4: "Janardhan BS",
8: "1984-04-18",
9: "1",
10: "New House, Near Metro Line, Bengaluru, KA",
11: "[email protected]",
12: "+919876543210",
13: "IN",
62: {
0: "52494646dc0100005745425056503820d0010000b00d009d012a40004
0003e913c9b4925a322a12a1ccae8b01209690013e295b2585d5ee72395f7
fe4a35103d1894a549b58a4febe751ae9a3d00cb96f016fc35075f892786b
3bcce1deffb2b3e55e3598b7d4913c80a237f1d9e51be7f271cc971d63fda
0c2c3c34b27a574ec1bbd7752969c56c8c0000fefeffce44d1e6b7ad25355
38b4cc7a3cf016f5b7d160c4e7202269bc041f0609efdf8e687702cdd6bd6
4e90b2931c9210f095f3c3bef00a954bfef4e70c76948b9eedf20e5be9e88
5edbcceada8f6fbdb9037490fa2eecaeaa62de8123028505f9f2eb2f781fd
fc9b55ff127f12cb657cdc5927866e650426e3032500af838514711241395
bfb130fda3c29d836527eeb82d92121b5a6f3b951d4ecc51ae1566c582662
27b0f02ced0050fe35e0e42a33026a2c44c581fc65ddd135b6a7e5bc888ef
852f6c477ccd817b850b90fa3565e11b61e7fe46f965abe210d097ef03eaa
f028c4ff9dff5f55ad472464b4920a5958b8c98ef0e0029160f20a8f4d1a0
2ad3b5ad0c43c0b03dc549576cafb6c3d6c36f1014c57d94f6985f8a328dc
7aef8df3507041dc440e99fe9acd90cd3ede4381d5b3d64064bce4bb8d051
13fd901b158698312bdf8a21049288d6006a2c944dae7bc3e24000000",
1: 0,
2: 4
}
}61 / CWT Tag / (
18 / COSE_Sign1 Tag / (
[
h'A10127', / Protected Header /
{4: h'6B2D31313031'}, / Unprotected Header /
h'A5016C7777772E6D6F7369702E696F041A6A9160FD051A68B02D7D061A68B02D7D18A95902
6DA9016A33393138353932343338046C4A616E61726468616E20425308683139383430343138
0961310A78294E657720486F7573652C204E656172204D6574726F204C696E652C2042656E67
616C7572752C204B410B756A616E61726468616E406578616D706C652E636F6D0C6D2B393139
3837363534333231300D62494E183EA3005901E452494646DC0100005745425056503820D001
0000B00D009D012A400040003E913C9B4925A322A12A1CCAE8B01209690013E295B2585D5EE7
2395F7FE4A35103D1894A549B58A4FEBE751AE9A3D00CB96F016FC35075F892786B3BCCE1DEF
FB2B3E55E3598B7D4913C80A237F1D9E51BE7F271CC971D63FDA0C2C3C34B27A574EC1BBD775
2969C56C8C0000FEFEFFCE44D1E6B7AD2535538B4CC7A3CF016F5B7D160C4E7202269BC041F0
609EFDF8E687702CDD6BD64E90B2931C9210F095F3C3BEF00A954BFEF4E70C76948B9EEDF20E
5BE9E885EDBCCEADA8F6FBDB9037490FA2EECAEAA62DE8123028505F9F2EB2F781FDFC9B55FF
127F12CB657CDC5927866E650426E3032500AF838514711241395BFB130FDA3C29D836527EEB
82D92121B5A6F3B951D4ECC51AE1566C58266227B0F02CED0050FE35E0E42A33026A2C44C581
FC65DDD135B6A7E5BC888EF852F6C477CCD817B850B90FA3565E11B61E7FE46F965ABE210D09
7EF03EAAF028C4FF9DFF5F55AD472464B4920A5958B8C98EF0E0029160F20A8F4D1A02AD3B5A
D0C43C0B03DC549576CAFB6C3D6C36F1014C57D94F6985F8A328DC7AEF8DF3507041DC440E99
FE9ACD90CD3EDE4381D5B3D64064BCE4BB8D05113FD901B158698312BDF8A21049288D6006A2
C944DAE7BC3E2400000001000204', / Payload with claim 169 tag /
h'74E64803A946B30EC091D138433DD6A288CCBB44A8614DFA6094695B998FBCC9D8AD3EEB56
8B3360FA67EEAD58B89F924DB5F58781A80E501E908231EDEE1C05' / Signature /
]
)
)






























































































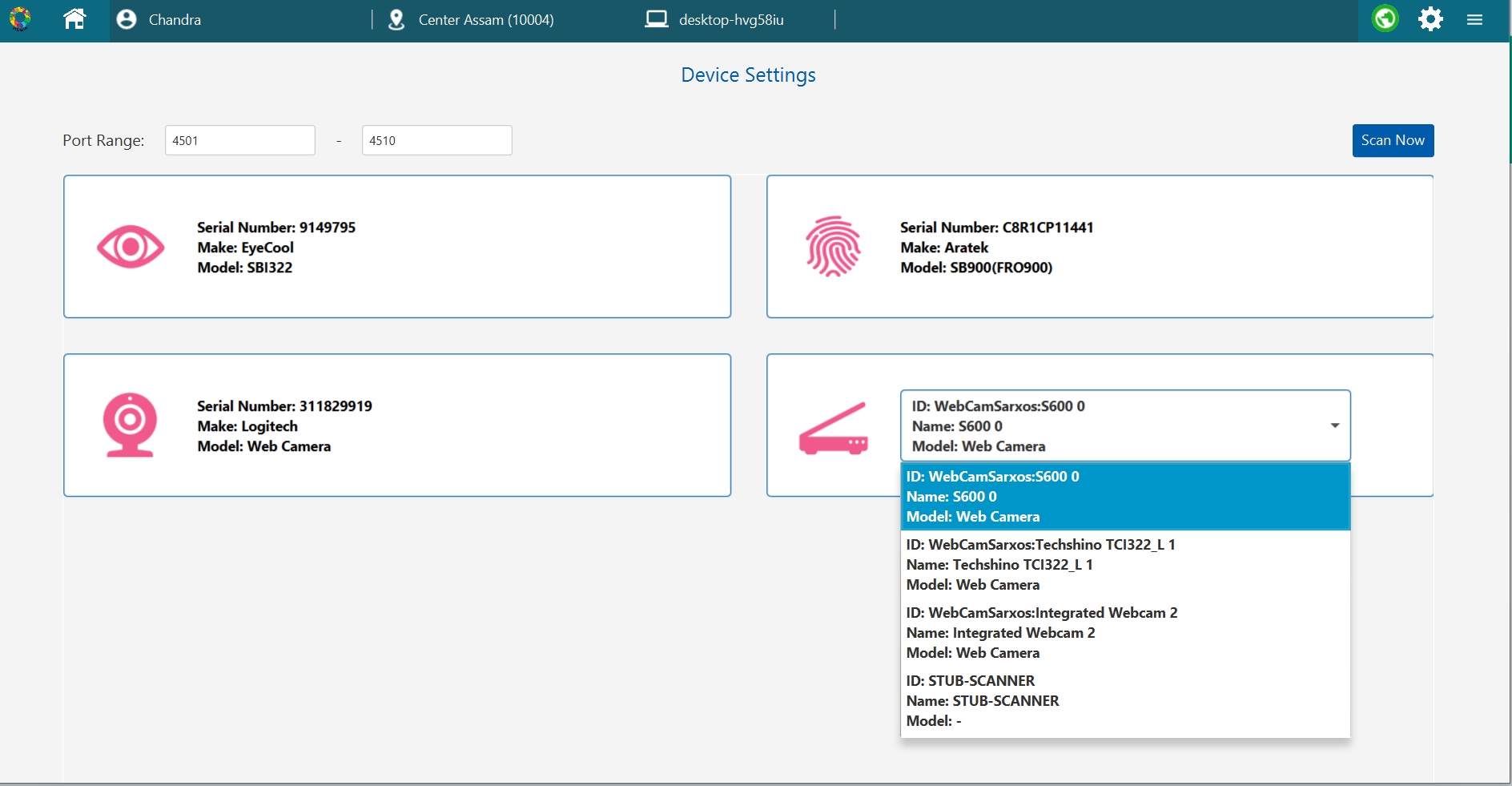
The Resident Portal is a user-friendly web-based platform designed to assist residents in accessing various services associated with their Unique Identification Number (UIN). This portal offers a range of essential services such as:
UIN services using UIN/VID (through e-Signet):
View My History
Manage My VID
Secure My ID
Track My Requests
Get Personalised Card
Share My Data
Logout
Get Information
About Registration Centers
List of supporting documents
Get My UIN (using UIN/ VID/ AID)
Verify email ID and/ or phone number
Responsive UI support- Support for the application to work seamlessly on various resolutions.
Book an appointment for new enrolment (via the pre-registration portal)
Ancillary features
Font size
Get Notifications (email and bell notifications)
View profile details of the logged in user (name, photo, and last login details)
Below is the detailed explanation of each of the features mentioned above.
Residents can use these services to view, update, change, manage or share their data. They can also report an issue in case of a grievance.
Pre-requisites: To login into the Resident Portal, the resident should have their unique virtual ID (VID) or Unique Identification Number (UIN) and also have access to the registered email ID/ phone number to be able to receive the OTP.
Resident accesses the Resident Portal dashboard page.
Resident clicks on UIN Services.
The login screen appears and the resident can choose one of the options to log in.
To login with OTP authentication, the resident clicks on Log in here> More ways to login > Login with OTP.
Resident needs to enter valid VID in the Enter Your VID text field and check the box I'm not a robot.
Next, the resident clicks on the Get OTP button.
The resident receives the OTP on the registered phone number and email ID.
The resident needs to enter the valid OTP received within stipulated time and click the Verify button.
The resident is then navigated to the Consent page. On this page, the Essential and Voluntary claims are displayed. Additionally, they will also have to allow access to their data in Authorize Scope section to avail various services. Based on the consent provided by the resident, the services will be made available for modification.
The resident has the choice to select from the list of Voluntary claims while the Essential claims are mandatory.
The resident should now click the Continue button. The system navigates the resident to the UIN Services menu page from where they can avail various services.
Note: Consent page will be available only for first time login.
The residents can view the history of all the transactions associated with their logged-in UIN/ VID. They can also view their details and if any unaccounted entry is found, a report can be raised against the same.
The residents can perform the following:
Search: The residents can enter an Event ID to search a particular event.
Filter based on date (From date and To date): The Residents can put a “from” and “to” date in order to get the list of all the events performed in the chosen date range.
Filter based on status (Success/ In Progress/ Failure): The Residents can filter based on the status of the event. E.g.: If they want to view all “In Progress” events, they can choose the status as “In Progress”. Additionally, they can also select any combination of the above three options.
Filter based on History Type (Authentication, ID Management, Data Update, Data Share, Service Requests): The Residents can filter based on the type of event. Additionally, they can also choose any combination of the above five options.
Authentication Request: This includes all the authentication and e-KYC requests.
ID Management Request: This includes the below services:
Manage My VID (Generate/Revoke VID)
Verify phone number/email ID
Secure My ID (Lock/unlock various authentication types)
Data Update Request: This includes the below services:
Update my UIN (demographic data and contact data)
Data Share Request: This includes the below services:
Share with a partner
Service Request: This includes the below services:
Download configured card
Physical card
Get my UIN
Book an appointment (lost UIN, Update UIN, Pre-registration, other)
Go button: Residents can click on the Go button once they are done selecting all the required filters.
Download the PDF of the results: The residents can download the PDF version of the search result populated.
Clicking on the accordion/ the caret of a particular event, the following options will appear:
a. View Details: The residents can view the details about an event by clicking on View Details. They will be redirected to Track My Request page with pre-filled EID where they can see further details about the event.
b. Pin Event to the top: The residents can pin the events to the top of the list based on their preference. Currently, this is configured for up to 3 events but it can be customized as per country’s requirements. Also, the resident can unpin the pinned events by clicking Unpin from Top.
c. Report a grievance: The residents can report a grievance in case of fraud or for any event not initiated by them. On clicking Report an Issue, the resident will be redirected to the Grievance Redressal Form page where they will see a set of pre-filled data as well as a set of data to be filled.
Pre-filled data:
Name
Event ID (EID)
Registered Email ID
Registered Mobile Number
Data to be filled:
Alternate Email ID
Alternate Mobile Number
Comments
Once the event is completed, a message is displayed containing the grievance tracking ID.
Below are the images with different filters on this page.
On clicking Manage My VID, the resident will be taken to a page where they can view details of the existing VIDs, generate new VID, revoke existing VID or download a VID card.
The following types of VIDs can be seen based on the VID policy:
Perpetual VID
Temporary VID
One-time VID
Note: The resident can get to know about the features of a particular VID by hovering over the “i” symbol.
The residents can perform the following:
Create a new VID : The residents can click on the Create button against any of the VID type selected. They can click on Yes to proceed. Once the event is completed, a message is displayed containing the Event ID along with a link to track the service.
Revoke an existing VID: The residents can click on the Delete icon to revoke an existing VID. They can click on Yes to proceed. Once the event is completed, a message is displayed containing the Event ID along with a link to track the service.
Download a VID card:
a. The residents can click on the Download icon to initiate the download process. They can click on Download to proceed. Once the event is completed, a message is displayed containing the Event ID, a link to track the service and the password combination.
b. Once the card is ready to download, they will receive a notification for the same under the bell icon displayed on the top right corner of the screen and as an Email notification.
c. On clicking on the notification, the resident will be taken to Track My Request page with pre-filled EID.
d. On this screen, the resident will be able to download the card by clicking on Download My VID card button on the bottom left corner of the screen.
e. The downloaded card will be a password protected PDF. The residents can view the downloaded VID card by entering the password combination displayed on the screen.
View VID number: All the VID numbers will be masked by default. The residents can view the unmasked version of VID by clicking on eye icon next to the VID number.
On clicking Secure My ID, the residents can view the status of all the authentication types. They can choose to lock or unlock authentication types like the following:
Email authentication
Mobile authentication
Demographic authentication
Fingerprint authentication
Iris authentication
Face authentication
The residents can perform the following,
View the current status of authentication types: The lock icon on each card indicates the current status of the authentication type. E.g.: If the lock is open, the authentication type is unlocked which means the residents can authenticate themselves using that particular authentication type and vice versa.
Lock/ unlock the authentication types: To lock/ unlock a particular authentication type, the residents can click on lock/ unlock button. Once the preferences of each authentication type is selected, the residents can click on Submit to save the changes and click Yes to proceed. Once the event is completed, a message is displayed containing the Event ID along with a link to track the service.
On clicking Track My Requests, the residents can track the status of an EID associated with the logged-in UIN/ VID. They can also view and download the detailed information about the entered EID like:
Event ID- This is the unique ID provided against each event
Event Type- This is the feature that is being availed. E.g.: Lock/unlock authentication types
Event Status- This is the status of the event which can hold values like Success, Failure or In-Progress
Individual ID- This is the type of individual ID that was used to login. E.g.: VID or UIN
Summary- This the the detailed description of the event.
Timestamp- This the time when the event occurred.
Authentication Mode- This is the authentication mode used to login. E.g.: OTP or Biometric or QR code
Partner Logo- This is the logo of the registered partner.
Partner Name- This is the name of the registered partner.
Attribute List- This is the list of attributes shared with the registered partner.
Purpose- This is the purpose of sharing data with the registered partner as input by the resident.
The resident can reach Track My Requests page by the following ways:
UIN services > View history > Click on the event tile > View details
By clicking the bell icon
UIN services > Track My Requests
Note:
Residents can download their updated UIN /VID card.
Report a grievance: The residents can report a grievance in case of fraud or for any event not initiated by them. On clicking Report an Issue, the resident will be redirected to the Grievance Redressal Form page where they will see a set of pre-filled data as well as a set of data to be filled.
On clicking Get Personalised Card, the residents can select the data to be added to their credential. They can preview the chosen data and download it. To be able to download the card, residents should select at least 3 attributes from the list mentioned below:
Name- Name of the resident. They can choose the format in which they want the name to be displayed.
Date of Birth- Date of birth of the resident. They can choose the format in which they want the date of birth to be displayed.
UIN- Unique Identification Number. They can choose to mask or unmask the UIN.
Perpetual VID- Perpetual Virtual ID. They can choose to mask or unmask the VID.
Phone number- Registered phone number of the resident. They can choose to mask or unmask the phone number.
Email ID- Registered email ID of the resident. They can choose to mask or unmask the email ID.
Address- Address of the resident. They can choose the format in which they want the address to be displayed.
Gender
Photo
These details can be previewed as and when the attributes are chosen.
Once the event is completed, a message is displayed containing the Event ID along with a link to track the service.
On clicking Share My Data, the residents can choose the data to be shared with any of the registered partners to avail various third party services.
To share the data, residents should select at least 3 attributes from the list mentioned below:
Name- Name of the resident. They can choose the format in which they want the name to be displayed.
Date of Birth- Date of birth of the resident. They can choose the format in which they want the date of birth to be displayed.
UIN- Unique Identification Number. They can choose to mask or unmask the UIN.
Perpetual VID- Perpetual Virtual ID. They can choose to mask or unmask the VID.
Phone number- Registered phone number of the resident. They can choose to mask or unmask the phone number.
Email ID- Registered email ID of the resident. They can choose to mask or unmask the email ID.
Address- Address of the resident. They can choose the format in which they want the address to be displayed.
Gender
Photo
These details can be previewed as and when the attributes are chosen.
Additionally, the residents have to:
Select the partner with whom they want to share their data from a dropdown list of registered partners.
Enter the purpose of sharing the data with the registered partner.
On clicking the Share button, the resident will have to provide consent to share their data with the external partner.
Once the event is completed, a message is displayed containing the Event ID along with a link to track the service.
The Resident Portal menu bar contains the following:
Font Size- Residents can alter the size of the font based on their preferences.
Language- Residents can select the language of preference.
Bell icon Notification- Residents can view the notifications of all the asynchronous events in chronological order.
Profile Icon- Residents can view the following:
Name of the logged in user
Photo of the logged in user
Last login details
Logout option
The residents can book an appointment for registration using the pre-registration portal. To do so, they can click on Book an appointment tile which will redirect them to the pre-registration portal. To know more about pre-registration portal, refer to this link Pre-registration.
The residents can use this feature to verify their registered email ID or phone number.
Steps to verify email ID/ phone number:
Resident clicks either on Verify email ID or Verify phone number option
Enter the UIN/VID.
Select I’m not a robot against the captcha and click on Send OTP.
Resident enters the OTP received on the requested channel and clicks on Submit.
Based on the scenario, any of the below three messages will be displayed:
a. Email ID/ phone number successfully verified: On successful verification, a message is displayed on the screen saying that the phone number/ email ID has been successfully verified.
b. Email ID/ phone number was already verified: If the verification has been previously completed, a message is displayed saying the email ID/ phone number was already verified.
c. Email ID/ phone number does not exist: If there is no email ID/ phone number linked to the UIN/VID, a message is displayed saying no email ID/ phone number was found associated to this UIN/VID.
The residents can use this feature for one of the following:
Download their UIN card
Check the status of their Application ID (AID)
Steps to download the UIN:
Resident clicks on Get My UIN
Enter the AID/UIN/VID.
Select I’m not a robot against the captcha and click on Send OTP.
Resident enters the OTP received on the registered email ID/ phone number and clicks on Submit.
The default PDF of UIN card will be downloaded and a success message is seen stating that the UIN has been successfully downloaded.
Steps to check the status of the AID:
Note: If the UIN is not ready, then the AID is used to get status else UIN card will be downloaded using AID too.
Resident clicks onGet My UIN.
Enter the AID.
Select I’m not a robot against the captcha and click on Send OTP.
Resident enters the OTP received on the registered email ID/ phone number and clicks on Submit.
The status of the AID will be shown.
Residents can view the list of supported documents in the PDF format and download the same. Also, some sample documents are available for reference.
Residents can search for Registration Centres on the basis of below two mechanisms:
Nearby centers: The resident will be asked to allow permission for location access in order to enable the system to suggest the nearest Registration Centres.
Manually look for centers: If the Resident wants to manually look for a center, they can do so by choosing a level in location hierarchy from the drop-down (e.g.: Region, Province, Postal Code) and entering the value against the same.
They can also download the PDF version of the result displayed on the screen for reference.
Update My Data
Identity data
Name
DOB
Gender
POI document
Address
Full address
POA document
Contact Information
Phone number
Email ID
Preferred Language
Identity Data: Residents can update their identity data like Name, Date of Birth, Gender certain number of times (number of times the identity data can be updated is configurable). To update the Identity Data, the residents will have to do the following:
a. Go to “Update My Data”
b. Click on “Identity” tab
c. Enter the new Name/ new Date of Birth/ new Gender in preferred language.
d. The resident will then have to choose the type of document from drop-down.
e. Upload a valid supporting document as Proof of Identity to back their change in identity request.
f. Once the document is uploaded, the “Preview” button will be made clickable
g. The Residents will then be taken to the preview screen where they can view the updated data and the uploaded supporting document which they can modify if required. When the resident is satisfied with all the data entered, he can go ahead and submit the data update request by clicking on “Update” button.
h. The Resident will then have to accept the terms and conditions and click on “Submit” button to submit the data update request.
i. Once the event is completed, a message will be displayed containing the Event ID along with a link to track the service.
j. A bell icon and an email notification will be triggered using which the residents can view the status of the application.
k. Once the update is successful, the card can be downloaded with new data by clicking on the particular notification.
Address: Residents can update their partial address or full address on the basis of their requirement any number of times. To update the Address, the residents will have to do the following:
a. Go to “Update My Data”
b. Click on “Address” tab
c. Enter the new address.
d. The resident will then have to choose the type of document from drop-down.
e. Upload a valid supporting document as Proof of Address to support their change in address request.
f. Once the document is uploaded, the preview button will be enabled.
g. The Residents will be taken to the preview screen where they can view the updated data and the uploaded supporting document which they can modify if required by clicking on the pencil icon.
h. When the resident is satisfied with all the data entered, they can go ahead and submit the data update request by clicking on “update”.
i. The Resident will also have to accept the terms and conditions in order to proceed and click on “Submit” button to proceed.
j. Once the event is successful, a message will be displayed consisting of the Event ID along with a link to track the service.
k. A bell icon and an email notification will be triggered using which the residents can view the status of the application.
l. Once the update is successful, the card can be downloaded with new data by clicking on the particular notification.
Contact Data: Residents can update their existing email ID and phone number. To update the Contact Data, the residents will have to do the following:
a . Go to “Update My Data”.
b. Click on “Contact Data” tab.
c. Enter the new email ID or Phone number (whichever needs to be updated).
d. The Resident will receive an OTP over their new email ID/ Phone number and thereby entering the OTP received on the new email ID/ phone number.
e. Once the event is completed, a message will be displayed consisting of the Event ID along with a link to track the service.
f. A bell icon and an email notification will be triggered using which the residents can view the status of the application.
g. Once the update is successful, the card can be downloaded with new data by clicking on the particular notification.
Notification Language Preference: Residents can update the language in which all the notifications are being sent to them. The residents can change the notification language as many times as they want to. To update the Notification Language, the residents will have to do the following:
a. Go to “Update My Data”
b. Go to “Language Preference” tab
c. Click on the “New Notification Language” drop-down.
d. Choose the new Notification Language and click in “Submit” button.
e. On clicking on “Submit”, a message will be displayed consisting of the Event ID along with a link to track the service.
Multi-Lingual Support:
The Residents can view the entire portal in the language that they prefer using the language change option on the top right corner of the screen. On choosing any language, all the labels/ texts/ success or error messages, PDF downloads will be displayed in the chosen language.
To change the language, the residents will have to do the following:
Click on the language option from the header menu.
On clicking the language option, a drop-down will open that will have the list of languages in which the Resident Portal can be rendered in.
On choosing any language, the screen will be refreshed and the entire portal will be rendered in the chosen language.
Menu option in English.
Menu option in French
Menu option in Arabic
The Registration Client UI is dynamically configured using JSON specifications derived from the . This approach ensures that registration forms are country-specific and adaptable to different identity requirements.
Process/Task: A registration workflow (NEW, UPDATE, LOST, CORRECTION)
Screen: A page within a process containing multiple fields
Field: Individual input elements with specific data types and validations
Dynamic Rendering: UI components are generated based on JSON specifications
Linear Flow: Screens appear in order sequence
Conditional Display: Based on visible expressions
Validation Gates: Next screen unlocked after validation
Group-based Navigation: UPDATE process allows group selection
Use descriptive field IDs that match ID Schema exactly
Provide comprehensive labels in all supported languages
Set appropriate field categories (pvt, evidence, kyc)
Configure proper validation for data integrity
Use alignment groups for logical field grouping
Don't use generic field IDs like field1, field2
Don't skip validation for critical fields
Don't ignore multi-language requirements
Don't use inappropriate control types for data
Use UPPERCASE for process IDs
Use descriptive icons for visual identification
Set logical order for home screen display
Enable isActive only for ready processes
Scenario: Show spouse details only for married adults
Scenario: Configure proof of address document upload
Scenario: Configure fingerprint capture with exception support
Scenario: Country-based state selection
Scenario: Name entry with transliteration
Problem: Field configured but not visible Solutions:
Check visible expression syntax
Verify active flag on screen
Confirm field id matches ID Schema
Validate inputRequired setting
Problem: Field accepts invalid data Solutions:
Verify regex pattern syntax
Check langCode specificity
Confirm validator type is supported
Test with sample data
Problem: Biometric fields not capturing data Solutions:
Verify bioAttributes configuration
Check device connectivity
Confirm exceptionPhotoRequired setting
Validate age group conditions
Problem: Cannot proceed to next screen Solutions:
Check required field completion
Verify validation rules pass
Confirm screen order sequence
Check conditional navigation logic
This comprehensive guide provides the foundation for configuring and customizing Registration Client UI specifications to meet specific country requirements while maintaining consistency and usability.

































{
"id": "NEW",
"order": 1,
"flow": "NEW",
"label": {
"eng": "New Registration",
"ara": "تسجيل جديد",
"fra": "Nouvelle inscription"
},
"screens": [...],
"caption": {...},
"icon": "registration.png",
"isActive": true,
"autoSelectedGroups": ["Demographics"]
}id
String
Yes
Unique process identifier (NEW/UPDATE/LOST/CORRECTION)
order
Number
Yes
Display order on home screen
flow
String
Yes
Process flow type
label
Object
Yes
Multi-language process labels
screens
Array
Yes
Screen configurations for the process
caption
Object
No
Tooltip text for process
icon
String
No
Icon file name for process
isActive
Boolean
Yes
Enable/disable process
autoSelectedGroups
Array
No
Pre-selected field groups for UPDATE process
NEW
NEW
Initial registration
First-time identity creation
UPDATE
UPDATE
Update existing identity
Demographic/biometric updates
LOST
LOST
Replace lost identity
UIN card replacement
BIOMETRIC_CORRECTION
CORRECTION
Correct biometric data
Fix biometric capture errors
{
"order": 1,
"name": "demographics",
"label": {
"eng": "Demographic Details",
"ara": "التفاصيل الديموغرافية",
"fra": "Détails démographiques"
},
"caption": {...},
"fields": [...],
"layoutTemplate": null,
"preRegFetchRequired": true,
"additionalInfoRequestIdRequired": false,
"active": true
}order
Number
Yes
Screen sequence in process
name
String
Yes
Unique screen identifier
label
Object
Yes
Multi-language screen titles
caption
Object
No
Screen description/tooltip
fields
Array
Yes
Field configurations
layoutTemplate
String
No
Custom layout template
preRegFetchRequired
Boolean
No
Enable pre-registration data fetch
additionalInfoRequestIdRequired
Boolean
No
Capture additional info request ID
active
Boolean
Yes
Show/hide screen
Data Entry
Capture user information
Next/Previous buttons
Review
Display entered data for confirmation
Edit/Confirm options
Document Upload
File upload interface
Upload/Preview/Remove
Biometric Capture
Biometric data collection
Capture/Retry/Exception
{
"id": "fullName",
"inputRequired": true,
"type": "string",
"controlType": "textbox",
"minimum": 0,
"maximum": 50,
"description": "Full name of the applicant",
"label": {
"eng": "Full Name",
"ara": "الاسم الكامل",
"fra": "Nom complet"
},
"fieldType": "default",
"format": "none",
"validators": [...],
"fieldCategory": "pvt",
"required": true
}id
String
Yes
Unique field identifier matching ID Schema
"fullName"
inputRequired
Boolean
Yes
Whether UI input is needed
true
type
String
Yes
Data type from ID Schema
"string"
controlType
String
Yes
UI component type
"textbox"
label
Object
Yes
Multi-language field labels
{"eng": "Full Name"}
required
Boolean
Yes
Mandatory field flag
true
textbox
Single-line text input
String data
Names, addresses, ID numbers
fileupload
File selection and upload
Document/image files
Certificates, photos, proof documents
dropdown
Selection from predefined options
Selected value from list
Country, state, document type
checkbox
Boolean selection
True/false
Consent acceptance, optional flags
button
Action trigger or selection
Click event/selected option
Language selection, navigation
date
Date picker with calendar
Date value
Date of birth, expiry dates
ageDate
Age-based date validation
Date with age constraints
DOB with min/max age limits
html
Custom HTML content display
Static/dynamic content
Terms & conditions, instructions
biometrics
Biometric capture interface
Biometric data
Fingerprints, iris, face capture
default
Standard form fields
Static configuration in UI spec
dynamic
Runtime-configurable fields
Values loaded from master data
string
Text data
Names, addresses, phone numbers
simpleType
Basic data types
Numbers, booleans, simple strings
documentType
Document uploads
Certificates, ID proofs, photos
biometricsType
Biometric data
Fingerprints, iris scans, face images
minimum
Number
Minimum value/length
Date ranges, text length
maximum
Number
Maximum value/length
Age limits, character limits
format
String
Text case formatting
"uppercase", "lowercase", "none"
validators
Array
Validation rules
Regex patterns, custom validations
fieldCategory
String
Data sharing category
"pvt", "evidence", "kyc"
alignmentGroup
String
Horizontal field grouping
Layout arrangement
visible
Object
Conditional display logic
MVEL expressions
group
String
Field grouping for UPDATE process
Group-based updates
transliterate
Boolean
Auto-transliteration support
Multi-language names
{
"id": "individualBiometrics",
"type": "biometricsType",
"controlType": "biometrics",
"bioAttributes": [
"leftEye", "rightEye", "rightIndex", "leftIndex",
"rightThumb", "leftThumb", "face"
],
"conditionalBioAttributes": [
{
"ageGroup": "INFANT",
"process": "ALL",
"validationExpr": "face || (leftEye && rightEye)",
"bioAttributes": ["face", "leftEye", "rightEye"]
}
],
"exceptionPhotoRequired": true
}face
Facial photograph
All ages
leftEye, rightEye
Iris scans
All ages
leftThumb, rightThumb
Thumb fingerprints
Adults/Children
leftIndex, rightIndex
Index fingerprints
Adults/Children
leftMiddle, rightMiddle
Middle fingerprints
Adults/Children
leftRing, rightRing
Ring fingerprints
Adults/Children
leftLittle, rightLittle
Little fingerprints
Adults/Children
Next
Move to next screen
After validation passes
Previous
Return to previous screen
All screens except first
Home
Return to home screen
All screens
Save
Save current progress
All data entry screens
Submit
Submit completed form
Final review screen
{
"type": "regex",
"validator": "^([0-9]{10,30})$",
"arguments": [],
"langCode": null,
"errorCode": "UI_100001"
}regex
Regular expression validation
Pattern in validator field
required
Mandatory field check
required: true
length
String length validation
minimum/maximum values
date
Date range validation
Date constraints
age
Age-based validation
Age group calculations
UI_1xxxxx
Field validation errors
UI_100001 - Invalid format
UI_2xxxxx
Screen validation errors
UI_200001 - Missing required field
UI_3xxxxx
Process validation errors
UI_300001 - Process not available
// Phone number validation
{
"type": "regex",
"validator": "^[6-9]\\d{9}$",
"errorCode": "INVALID_PHONE_NUMBER"
}
// Age validation for adults
{
"type": "regex",
"validator": "^(1[8-9]|[2-9]\\d|100)$",
"errorCode": "INVALID_AGE_ADULT"
}// Logical screen progression
{
"screens": [
{"order": 1, "name": "consent"},
{"order": 2, "name": "demographics"},
{"order": 3, "name": "documents"},
{"order": 4, "name": "biometrics"},
{"order": 5, "name": "review"}
]
}// Horizontal alignment for related fields
{
"alignmentGroup": "name_group",
"fields": [
{"id": "firstName", "alignmentGroup": "name_group"},
{"id": "middleName", "alignmentGroup": "name_group"},
{"id": "lastName", "alignmentGroup": "name_group"}
]
}{
"visible": {
"engine": "MVEL",
"expr": "identity.get('ageGroup') == 'ADULT' && identity.get('maritalStatus') == 'MARRIED'"
}
}{
"requiredOn": [
{
"engine": "MVEL",
"expr": "identity.get('residencyStatus') == 'FOREIGNER'"
}
]
}{
"id": "spouseName",
"visible": {
"engine": "MVEL",
"expr": "identity.get('ageGroup') == 'ADULT' && identity.get('maritalStatus') == 'MARRIED'"
},
"required": true
}{
"id": "proofOfAddress",
"type": "documentType",
"controlType": "fileupload",
"subType": "POA",
"validators": [
{
"type": "fileType",
"validator": "pdf|jpg|png",
"errorCode": "INVALID_FILE_TYPE"
}
]
}{
"id": "fingerprints",
"type": "biometricsType",
"controlType": "biometrics",
"bioAttributes": ["rightIndex", "leftIndex"],
"exceptionPhotoRequired": true,
"conditionalBioAttributes": [
{
"ageGroup": "ADULT",
"process": "NEW",
"validationExpr": "rightIndex || leftIndex",
"bioAttributes": ["rightIndex", "leftIndex"]
}
]
}{
"id": "state",
"type": "string",
"controlType": "dropdown",
"fieldType": "dynamic",
"changeAction": "loadDistricts",
"visible": {
"engine": "MVEL",
"expr": "identity.get('country') != null"
}
}{
"id": "fullName",
"type": "string",
"controlType": "textbox",
"transliterate": true,
"format": "none",
"validators": [
{
"type": "regex",
"validator": "^[a-zA-Z\\s]{1,50}$",
"langCode": "eng"
}
]
}UI_1xxxxx
Field validation
Check field configuration and input data
UI_2xxxxx
Screen validation
Verify screen-level requirements
UI_3xxxxx
Process validation
Check process configuration
BIO_xxxxx
Biometric errors
Verify device and biometric settings
DOC_xxxxx
Document errors
Check file type and upload settings
{
"id": "termsAndConditions",
"controlType": "html",
"templateName": "Registration Consent",
"fieldCategory": "evidence",
"required": true
}{
"id": "address",
"locationHierarchy": ["country", "state", "district", "city"],
"controlType": "dropdown",
"fieldType": "dynamic"
}{
"id": "country",
"changeAction": "loadStates",
"controlType": "dropdown"
}When biometric duplicates are found in ABIS, the MOSIP system sends a request for manual adjudication to the Manual Adjudication System via a queue.
The system integrator can build the Manual Adjudication System, which would be listening to the MOSIP-to-ManualAdjudication queue for any manual adjudication requests and sends a response back in the ManualAdjudication-to-MOSIP system after verifying the data.
The data sent to the Manual Adjudication System is driven by a policy defined in MOSIP and the specification is similar to ABIS identify request.
The manual adjudication stage in registration processor performs the following functions:
Sends the applicant's demographic and biometric information (via queue + Datashare) to Manual Adjudication System (MAS).
Receives decision from MAS and accordingly forwards the packets.
If rejected, notifies the applicant.
{
"id": "mosip.manual.adjudication.adjudicate",
"version": "1.0",
"requestId": "987654321-89AB-CDEF-0123-456789ABCDEF",
"requesttime": "2019-02-14T12:40:59.768Z",
"referenceId": "27847657360002520181208123456",
"referenceURL": "<datashare url for regid>",
"gallery": {
"referenceIds": [
{
"referenceId": "27847657360002520181208123451",
"referenceURL": "<data share for matchedRegId>"
},
{
"referenceId": "27847657360002520181208123452",
"referenceURL": "<data share for matchedRegId>"
}
],
"addtional": [
{
"abisId": "<abis app code>",
"response": "<abis response text received>"
}
]
}
}requestId: request_id that is associated with each request present in reg_manual_verification table.
referenceId: reg_id that is associated with each request present in reg_manual_verification table.
referenceURL: Datashare url of biometrics, demographics(identity), audits, metainfo, documents of reg_id
gallery: contains the matched ref_id and referenceURL of matched ref_id.
{
"id": "mosip.manual.adjudication.adjudicate",
"version": "1.0",
"requestId": "4d4f27d3-ec73-41c4-a384-bf87fce4969e",
"referenceId": "10002100741000320210107125533",
"requesttime": "2021-01-19T07:16:22.930Z",
"referenceURL": "http://datashare-service/v1/datashare/get/mpolicy-default-adjudication/mpartner-default-adjudication/mpartner-default-adjudicationmpolicy-default-adjudication202011110619201EpLEjvD",
"addtional": null,
"gallery": {
"referenceIds": [
{
"referenceId": "10002100741000120210107111325",
"referenceURL": "http://datashare-service/v1/datashare/get/mpolicy-default-adjudication/mpartner-default-adjudication/mpartner-default-adjudicationmpolicy-default-adjudication202137493575474iefnvvsD"
}
]
}
}{
"id": "mosip.manual.adjudication.adjudicate",
"requestId": "987654321-89AB-CDEF-0123-456789ABCDEF",
"responsetime": "2019-02-14T12:40:59.768Z",
"returnValue": "1",
"candidateList": {
"count": "1",
"candidates": [
{
"referenceId": "27847657360002520181208123451",
"analytics": {
//This section is optional
"primaryOperatorID": "110011",
"primaryOperatorComments": "<comments provided by operator>",
"secondaryOperatorID": "110012",
"secondaryOperatorComments": "<comments provided by operator>",
"key1": "value1",
"key2": "value2"
}
}
],
"analytics": {
// This section is optional
"key1": "value1",
"key2": "value2"
}
}
}returnValue: 1-Success, 2-Failure
candidateList: It contains matched candidate referenceIds, count and analytics.
{
"id": "mosip.manual.adjudication.adjudicate",
"requestId": "c278b2f1-29f7-4d1a-9fa7-e93e3f932816",
"responsetime": "2022-09-23T06:31:31.7456782+00:00",
"returnValue": "1",
"candidateList": {
"count": "0",
"candidates": [],
"analytics": null
}
}{
"id": "mosip.manual.adjudication.adjudicate",
"requestId": "58d5bb0e-e65e-4907-b452-81edbfd3ae46",
"responsetime": "2022-09-23T06:33:11.9869624+00:00",
"returnValue": "1",
"candidateList": {
"count": "1",
"candidates": [
{
"referenceId": "10001100010000620220923053704",
"analytics": {
"primaryOperatorID": "admin",
"primaryOperatorComments": "MATCHED",
"Face": "F",
"Finger": "Right_Thumb,Right_Index,Right_Middle,Right_Ring,Right_Little,Left_Thumb,Left_Index,Left_Middle,Left_Ring,Left_Little",
"Iris": "Right_Iris,Left_Iris"
}
}
],
"analytics": null
}
}Datashare contains biometrics, identity documents, metainfo, audits related to particular rid and the datashare URL contains encrypted form of this data.
Note: Datashare encryption using partner key and decryption in MAS is using private key of that partner.
GET https://datashare-service/v1/datashare/get/mpolicy-default-adjudication/mpartner-default-adjudication/mpartner-default-adjudicationmpolicy-default-adjudication202011110619201EpLEjvD
Block 1
#KEY_SPLITTER#
Block 2
Block 1
#KEY_SPLITTER#
Block 2
{
"id": null,
"version": null,
"responsetime": "2021-02-05T06:29:48.257Z",
"metadata": null,
"response": null,
"errors": [
{
"errorCode": "KER-ATH-401",
"message": "Authentication Failed"
}
]
}DAT-SER-003
File does not exist or File is empty
DAT-SER-006
Data share not found
DAT-SER-006
Data share usage expired
KER-ATH-401
Authentication failed
KER-ATH-403
Forbidden
partner Id: mpartner-default-adjudication policy Id: mpolicy-default-adjudication
{
"shareableAttributes": [
{
"attributeName": "biometrics",
"group": "CBEFF",
"source": [
{
"attribute": "registration-client/NEW/individualBiometrics",
"filter": [
{
"type": "Iris"
}
]
},
{
"attribute": "CNIE/verification/biometrics",
"filter": [
{
"type": "Finger"
}
]
},
{
"attribute": "CNIE/verification/biometrics",
"filter": [
{
"type": "Face"
}
]
}
],
"encrypted": true,
"format": "extraction"
},
{
"attributeName": "fullName",
"source": [
{
"attribute": "fullName"
}
],
"encrypted": true
},
{
"attributeName": "dateOfBirth",
"source": [
{
"attribute": "dateOfBirth"
}
],
"encrypted": true
},
{
"attributeName": "gender",
"source": [
{
"attribute": "gender"
}
],
"encrypted": true
},
{
"attributeName": "phone",
"source": [
{
"attribute": "phone"
}
],
"encrypted": true
},
{
"attributeName": "email",
"source": [
{
"attribute": "email"
}
],
"encrypted": true
},
{
"attributeName": "addressLine1",
"source": [
{
"attribute": "addressLine1"
}
],
"encrypted": true
},
{
"attributeName": "addressLine2",
"source": [
{
"attribute": "addressLine2"
}
],
"encrypted": true
},
{
"attributeName": "addressLine3",
"source": [
{
"attribute": "addressLine3"
}
],
"encrypted": true
},
{
"attributeName": "region",
"source": [
{
"attribute": "region"
}
],
"encrypted": true
},
{
"attributeName": "province",
"source": [
{
"attribute": "province"
}
],
"encrypted": true
},
{
"attributeName": "city",
"source": [
{
"attribute": "city"
}
],
"encrypted": true
},
{
"attributeName": "postalCode",
"source": [
{
"attribute": "postalCode"
}
],
"encrypted": true
}
],
"dataSharePolicies": {
"typeOfShare": "Data Share",
"validForInMinutes": "30",
"transactionsAllowed": "100000",
"encryptionType": "none",
"shareDomain": "datashare.datashare",
"source": "Packet Manager"
}
}registration.processor.queue.manual.adjudication.request
registration.processor.queue.manual.adjudication.request.messageTTL
registration.processor.manual.adjudication.policy.id
registration.processor.manual.adjudication.subscriber.id
registration.processor.manual.adjudication.subscriber.id
mosip.regproc.data.share.protocol
mosip.regproc.data.share.internal.domain.name
registration.processor.queue.manual.adjudication.request
registration.processor.queue.manual.adjudication.request.messageTTL
registration.processor.manual.adjudication.policy.id
registration.processor.manual.adjudication.subscriber.id
registration.processor.manual.adjudication.subscriber.id
mosip.regproc.data.share.protocol
mosip.regproc.data.share.internal.domain.nameIn registration-processor-default.properties, the possible Error codes are as follows:
RPR-MVS-000
manual verification failed
RPR-MVS-001
Registration Id should not empty or null
RPR-MVS-002
No matched reference id found for given RID
RPR-MVS-025
Manual adjudication failed
RPR-MVS-022
Registration Id should not empty or null
RPR-MVS-022
TablenotAccessibleException in Manual verification
RPR-MVS-021
Manual verification rejected
RPR-MVS-025
Manual verification resend to queue
RPR-SYS-012
IO EXCEPTION
This stage is applicable only if required biometrics are not present in the packet as per country configuration.
Sends applicant's demographic documents (via Queue + Datashare) to external Verification System (VS).
Receives decision from VS and accordingly forwards the packets.
If rejected, notifies the applicant.
{
"id": "mosip.verification.adjudicate",
"version": "1.0",
"requestId": "987654321-89AB-CDEF-0123-456789ABCDEF",
"requesttime": "2019-02-14T12:40:59.768Z",
"referenceId": "27847657360002520181208123456",
"referenceURL": "<datashare url for regid>",
"addtional": [
{
"abisId": "<abis app code>",
"response": "<abis response text received>"
}
]
}
}requestId: verification_request_id that is associated with each request present in reg_verification table.
referenceId: reg_id that is associated with each request present in reg_verification table.
referenceURL: Datashare URL of biometrics, demographics(identity) ,audits, metainfo, documents of reg_id .
{
"id": " mosip.verification.adjudicate ",
"version": "1.0",
"requestId": "4d4f27d3-ec73-41c4-a384-bf87fce4969e",
"referenceId": "10002100741000320210107125533",
"requesttime": "2021-01-19T07:16:22.930Z",
"referenceURL": "http://datashare-service/v1/datashare/get/mpolicy-default-adjudication/mpartner-default-adjudication/mpartner-default-adjudicationmpolicy-default-adjudication202011110619201EpLEjvD",
"addtional": null,
}{
"id": " mosip.verification.adjudicate ",
"requestId": "4d4f27d3-ec73-41c4-a384-bf87fce4969e",
"responsetime": "2021-01-19T13:16:22.930Z",
"returnValue": "1"
}Response parameters
returnValue: 1-success, 2-failure
Datashare contains biometrics, identity, documents, metainfo, audits related to particular rid and datashare URL contains encrypted form of this data.
Note: Datashare encryption using partner key and decryption in MAS is using private key of that partner.
GET https://datashare-service/v1/datashare/get/mpolicy-default-adjudication/mpartner-default-adjudication/mpartner-default-adjudicationmpolicy-default-adjudication202011110619201EpLEjvD
Block 1
#KEY_SPLITTER#
Block 2
Block 1
#KEY_SPLITTER#
Block 2
{
"id": null,
"version": null,
"responsetime": "2021-02-05T06:29:48.257Z",
"metadata": null,
"response": null,
"errors": [
{
"errorCode": "KER-ATH-401",
"message": "Authentication Failed"
}
]
}Possible Error codes and Messages from Datashare URL
DAT-SER-003
File does not exists or File is empty
DAT-SER-006
Data share not found
DAT-SER-006
Data share usage expired
KER-ATH-401
Authentication Failed
KER-ATH-403
Forbidden
partner Id: mpartner-default-adjudication policy Id: mpolicy-default-adjudication
{
"shareableAttributes": [
{
"attributeName": "biometrics",
"group": "CBEFF",
"source": [
{
"attribute": "registration-client/NEW/individualBiometrics",
"filter": [
{
"type": "Iris"
}
]
},
{
"attribute": "CNIE/verification/biometrics",
"filter": [
{
"type": "Finger"
}
]
},
{
"attribute": "CNIE/verification/biometrics",
"filter": [
{
"type": "Face"
}
]
}
],
"encrypted": true,
"format": "extraction"
},
{
"attributeName": "fullName",
"source": [
{
"attribute": "fullName"
}
],
"encrypted": true
},
{
"attributeName": "dateOfBirth",
"source": [
{
"attribute": "dateOfBirth"
}
],
"encrypted": true
},
{
"attributeName": "gender",
"source": [
{
"attribute": "gender"
}
],
"encrypted": true
},
{
"attributeName": "phone",
"source": [
{
"attribute": "phone"
}
],
"encrypted": true
},
{
"attributeName": "email",
"source": [
{
"attribute": "email"
}
],
"encrypted": true
},
{
"attributeName": "addressLine1",
"source": [
{
"attribute": "addressLine1"
}
],
"encrypted": true
},
{
"attributeName": "addressLine2",
"source": [
{
"attribute": "addressLine2"
}
],
"encrypted": true
},
{
"attributeName": "addressLine3",
"source": [
{
"attribute": "addressLine3"
}
],
"encrypted": true
},
{
"attributeName": "region",
"source": [
{
"attribute": "region"
}
],
"encrypted": true
},
{
"attributeName": "province",
"source": [
{
"attribute": "province"
}
],
"encrypted": true
},
{
"attributeName": "city",
"source": [
{
"attribute": "city"
}
],
"encrypted": true
},
{
"attributeName": "postalCode",
"source": [
{
"attribute": "postalCode"
}
],
"encrypted": true
}
],
"dataSharePolicies": {
"typeOfShare": "Data Share",
"validForInMinutes": "30",
"transactionsAllowed": "100000",
"encryptionType": "none",
"shareDomain": "datashare.datashare",
"source": "Packet Manager"
}
}registration.processor.queue.verification.request
registration.processor.queue.verification.request.messageTTL
registration.processor.verification.policy.id
registration.processor.verification.subscriber.id
activemq.message.format
mosip.regproc.data.share.protocol
mosip.regproc.data.share.internal.domain.nameRPR-MVS-004
No Assigned Record Found
RPR-MVS-025
Multiple rids found for a reference id
RPR-MVS-022
TablenotAccessibleException in Manual verification
RPR-VER-002
Verification failed
RPR-VER-004
Resend for verification
RPR-MVS-016
Reg Id should not be null or empty
RPR-MVS-021
Manual verification rejected
MOSIP is built using the below tools and technologies.
This page lists all the technologies used in building MOSIP. Free and open-source software with clear long-term support availability has been chosen. For a deployment, certain choices can be replaced with other free or commercial options.
Operating System
CentOS
7.7
MIT License
Yes
Yes
NA - Part of Azure
Operating System
Ubuntu Server
20.04
Free
No
No
NA
Infrastructure
Cloud - Azure/AWS
NA - Cloud tool
Commercial
Yes
Depends on Deployment Arch.
Depends on Deployment Arch.
Development - Language Runtime
Java SE 11
OpenJDK 11
Oracle Binary Code License
No
Yes
NA
Development - Expression language
mvel2
2.4.7.Final
Development - Scheduling
quartz
2.2.1
Development - File Server
tus-java-client
0.4.3
Development - Internalization
nv-i18n
1.29
Development - Cryptography
TPM
2.0
Development - UI Application framework
JavaFx
OpenJFX 11
GPL v2 + Classpath
No
Yes
NA
Development - Application Framework
Vert.x
3.9.1
Apache License 2.0
No
Yes
NA
Development - Application Framework
Spring
5
Apache License 2.0
No
Yes
NA
Development - Utilities
Apache commons(60+ to be considered)
Latest version
Apache License 2.0
No
Yes
NA
Development - Data Grid
Apache Ignite
2.4.0
Apache License 2.0
No
Yes
NA
Development - Object Mapper
Orika
1.5.2
Apache License 2.0
No
Yes
NA
Development - validator
Hibernate validator
5.4.2
Apache Software License 2.0
No
Yes
NA
Development - Encryption
BouncyCastle
1.59
Adaptation of MIT X11 License
No
Yes
NA
Development - JSON marshal/unmarshal
Jackson
2.9.5
Apache License 2.0
No
Yes
NA
Development - Device Driver
RXTX
RXTX-2-2-20081207
LGPL v 2.1
No
Yes
NA
Development - Unit Testing
Junit
5.x and above
Common Public License - v 1.0
No
No
NA
Development - Unit Testing
Junit
4.x and above
Common Public License - v 1.0
No
No
NA
Development - Log
logback
1.2.3
GNU Lesser GPL Version 2.1
No
Yes
NA
Development - Templating
velocity
1.7
Apache License 2.0
No
Yes
NA
Development - Tools
Open street view
NA - Cloud tool
Open Database License (ODbL)
No
Yes
NA
Development - IDE
Eclipse Oxygen
4.7.3
Eclipse Public License Version 2.0
No
No
NA
Development - Unit Testing
Karma
2.0.x
MIT License
No
No
NA
Development - Unit Testing
Jasmine
2.6.1
MIT License
No
No
NA
Development - API Documentation
Swagger
3.13.2
Apache License 2.0
No
No
NA
Development - Application Server
Tomcat server
8
Apache License 2.0
No
Yes
NA
Development - Orchestration
Apache Camel
2.19.3
Apache License 2.0
No
Yes
NA
Development - WebSub
Ballerina Websub
slbeta2
Apache License 2.0
No
Yes
NA
Development - Database
H2 DB
1.4.197
No
Yes
NA
Development - Database
PostgreSQL
Server: 10
Postgres License BSD 2-clause "Simplified License"
Yes
No
NA
Development - Database
Derby DB
10.13.1.1
Development - Database Modeling tool
PG Data Modeler
0.9.2
Commercial
No
Yes
Nominal
Development - Scanner library
7
Commercial
Development - Code quality
Sonar
7.2
Open Source License
No
No
NA
Development - UI Designs
Pencil Project
3.0.4
GNU Public License version 2
No
No
NA
Development - TPM Java client
TSS.Java
0.3.0
Testing tools
Rest-assured
3.0.0 and above
Apache License 2.0
Testing tools
WireMock or Citrus framework
2.16.0 or respectively
Apache License 2.0
No
No
NA
Testing tools
JMeter
5.3.x
Apache License 2.0
No
No
NA
Testing tools
Burp suite Professional +
9.0.3.7
PortSwigger - Burp suite Professional + / V1.7.33
No
No
NA
Testing tools
TestNG
6.11
Apache License 2.0
No
No
NA
Testing tools
awaitility
4.0.3
Apache License 2.0
No
No
NA
Testing tools
testfx
4.0.16-alpha
EUPL1.1
No
No
NA
Testing tools
extentreports
3.1.5
Apache License 2.0
No
No
NA
Testing tools
selenium-java
3.141.59
Apache License 2.0
No
No
NA
DevOps tools
Jira
6.4 and above
Not Open source
Testing tools
12.x
No
NA
12.0.3
Open Source License
DevOps tools
SonarLint
v3.5
GNU GPL
DevOps tools
GitHub
2.7.x
Commercial - Github
DevOps tools
SonarQube
6.7.3 LTS
GNU GPL
DevOps tools
Maven
3.53.x
Apache License 2.0
DevOps tools
Docker
18.03.x CE
Apache 2.0
DevOps tools
Ansible
2.2
GNU GPL v3.0
DevOps tools
Github actions
NA - Cloud tool
DevOps tools
Travis
NA - Cloud tool
MIT License
DevOps tools
Glowroot
Apache License 2.0
DevOps tools
Prometheus
Apache License 2.0
DevOps tools
Grafana
Apache License 2.0
DevOps tools
Python
3.x
Messaging
ActiveMQ
Apache License 2.0
Messaging
Apache Kafka
Apache License 2.0
Caching
Hazelcast
Apache License 2.0
Object Store
MinIO
GNU AGPL v3
Secure Code Scanning
SonarQube with OWASP plugin will be used
Web Server/HTTP proxy server
Nginx
NA - Cloud tool
IAM
KeyCloak
The following guide outlines some important properties that can be customized for a given installation. Please note that this list is not exhaustive but serves as a checklist for reviewing properties that are likely to differ from the default settings. For a complete list of properties, refer to the files listed below.
Resident Service uses the following configuration files:
application-default.properties
resident-default.properties
resident-ui-share-credential-schema.json
resident-ui-update-demographics-schema.json
resident-ui-personalized-card-schema.jsonid-repository-default.properties
id-authentication-default.properties
mosip-vid-policy.json
registration-default.properties
Please go to the Files changes section and refer to removed and added properties.
Properties used for configuring the database.
mosip.resident.database.hostname=postgres-postgresql.postgres
mosip.resident.database.port=5432
javax.persistence.jdbc.driver=org.postgresql.Driver
javax.persistence.jdbc.url=jdbc:postgresql://${mosip.resident.database.hostname}:${mosip.resident.database.port}/mosip_resident
javax.persistence.jdbc.user=residentuser
javax.persistence.jdbc.password=******resident.appid=resident
resident.clientId=******
resident.secretKey=******
token.request.issuerUrl=${mosip.keycloak.issuerUrl}URL pattern for logging filter. For example, "/callback/*" .Defaults to "/*".
logging.level.root=INFO
logging.level.io.mosip.resident.batch=INFO
logging.level.io.mosip.resident.filter=DEBUG
resident.logging.filter.enabled=false
resident.logging.filter.url.pattern=/*This will print the request details such as URL, headers, and body for debugging purposes. The default is false.
logging.level.io.mosip.resident.config.LoggingInterceptor=DEBUG
resident.rest.template.logging.interceptor.filter.enabled=falseThis will print the repository method calls for debugging purposes. The default is false.
logging.level.io.mosip.resident.aspect.DatabaseLoggingAspect=DEBUG
resident.db.logging.aspect.enabled=falseresident.db.metrics.aspect.enabled=true
resident.rest.template.metrics.interceptor.filter.enabled=truesubscriptions-delay-on-startup_millisecs=120000
re-subscription-interval-in-seconds=43200
resident.websub.request.decorator.filter.enabled=truemosip.ida.partner.type=******
ida.online-verification-partner-id=******
idrepo-dummy-online-verification-partner-id=******
resident.share-credential.partner.type=******
resident.authentication-request.partner.type=******
resident.order-physical-card.partner.type=******hibernate.show_sql=false
hibernate.hbm2ddl.auto=none
hibernate.temp.use_jdbc_metadata_defaults=false
hibernate.jdbc.lob.non_contextual_creation = true
spring.jpa.properties.hibernate.temp.use_jdbc_metadata_defaults=falseThese are the authentication types allowed for a resident and default unlock duration.
auth.types.allowed=otp-email,otp-phone,demo,bio-FINGER,bio-IRIS,bio-FACE
resident.auth-type.default.unlock.duration.seconds=100Templates type codes for authentication types
resident.otp-email.template.property.attribute.list=mosip.otp-email.template.property
resident.otp-phone.template.property.attribute.list=mosip.otp-phone.template.property
resident.demo.template.property.attribute.list=mosip.demo.template.property
resident.bio-FINGER.template.property.attribute.list=mosip.bio-finger.template.property
resident.bio-IRIS.template.property.attribute.list=mosip.bio-iris.template.property
resident.bio-FACE.template.property.attribute.list=mosip.bio-face.template.propertyTemplates type codes for authentication types status
resident.UNLOCKED.template.property.attribute.list=mosip.unlocked.template.property
resident.LOCKED.template.property.attribute.list=mosip.locked.template.propertyBelow are the properties used for validation purpose.
mosip.id.validation.identity.phone=^([6-9]{1})([0-9]{9})$
mosip.id.validation.identity.email=^[\\w-\\+]+(\\.[\\w]+)*@[\\w-]+(\\.[\\w]+)*(\\.[a-zA-Z]{2,})$
resident.grievance-redressal.alt-email.chars.limit=128
resident.grievance-redressal.alt-phone.chars.limit=64
resident.grievance-redressal.comments.chars.limit=1024
resident.share-credential.purpose.chars.limit=1024
mosip.resident.eid.length=16
mosip.resident.eventid.searchtext.length=${mosip.resident.eid.length}
resident.message.allowed.special.char.regex=^[A-Za-z0-9 .,-]+$
resident.purpose.allowed.special.char.regex=^[A-Za-z0-9 .,-]+$
resident.id.allowed.special.char.regex=^[0-9]+$
resident.document.validation.transaction-id.regex=^[0-9]{10}$
resident.document.validation.document-id.regex=^[A-Za-z0-9-]{20,}$
resident.validation.is-numeric.regex=^[0-9]+$
resident.otp.validation.transaction-id.regex=^[0-9]{10}$
resident.validation.event-id.regex=^[0-9]{${mosip.resident.eid.length}}$mosip.security.csrf-enable:false
mosip.security.secure-cookie:falsetoken.request.appid=resident
token.request.clientId=******
token.request.secretKey=******auth.server.admin.allowed.audience=mosip-resident-client,mosip-reg-client,${mosip.iam.module.clientID}registration.processor.identityjson=identity-mapping.jsonProperties used for machine specification and center
resident.update-uin.machine-name-prefix = resident_machine_
resident.update-uin.machine-spec-id = RESIDENT-1
resident.update-uin.machine-zone-code = MOR
resident.center.id=10007
resident.machine.id=10045mosip.iam.adapter.appid=resident
mosip.iam.adapter.clientid=******
mosip.iam.adapter.clientsecret=******Property used to define the endpoints that should not be part of authentication.
mosip.service.end-points=/**/req/otp,/**/proxy/**/*,/**/validate-otp,/**/channel/verification-status,/**/req/credential/**,/**/req/card/*,/**/req/auth-history,/**/rid/check-status,/**/req/auth-lock,/**/req/auth-unlock,/**/req/update-uin,/**/req/print-uin,/**/req/euin,/**/credential/types,/**/req/policy/**,/**/aid/status,/**/individualId/otp,/**/mock/**,/**/callback/**,/**/download-card,/**/download/registration-centers-list/**,/**/download/supporting-documents/**,/**/vid/policy,/**/vid,/vid/**,/**/download/nearestRegistrationcenters/**,/**/authorize/admin/validateToken,/**/logout/user,/**/aid-stage/**mosip.resident.captcha.enable=true
mosip.resident.captcha.id.validate=mosip.resident.captcha.id.validate
mosip.resident.captcha.sitekey=******
mosip.resident.captcha.secretkey=******
mosip.resident.captcha.resourse.url=http://resident-captcha.resident/resident/v1/captcha/validatecaptcha
mosip.resident.captcha.recaptcha.verify.url=https://www.google.com/recaptcha/api/siteverifyThis property is used to define the keys of the properties to be exposed to UI.
resident.ui.propertyKeys=mosip.mandatory-languages,mosip.optional-languages,mosip.utc-datetime-pattern,mosip.iam.adapter.clientid,resident.datetime.pattern,mosip.resident.api.id.otp.request,mosip.resident.api.id.auth,mosip.resident.api.version.otp.request,mosip.resident.api.version.auth,mosip-prereg-host,mosip-prereg-ui-url,auth.types.allowed,resident.view.history.serviceType.filters,resident.view.history.status.filters,resident.auth-type.default.unlock.duration.seconds,mosip.resident.grievance.url,mosip.api.public.host,mosip.resident.captcha.sitekey,mosip.resident.captcha.secretkey,mosip.webui.auto.logout.idle,mosip.webui.auto.logout.ping,mosip.webui.auto.logout.timeout,mosip.resident.download.registration.centre.file.name.convention,mosip.resident.download.supporting.document.file.name.convention,mosip.resident.download.personalized.card.naming.convention,mosip.resident.ack.manage_my_vid.name.convention,mosip.resident.ack.secure_my_id.name.convention,mosip.resident.ack.personalised_card.name.convention,mosip.resident.ack.update_my_data.name.convention,mosip.resident.ack.share_credential.name.convention,mosip.resident.ack.order_physical_card.name.convention,mosip.resident.ack.name.convention,mosip.resident.uin.card.name.convention,mosip.resident.vid.card.name.convention,mosip.resident.download.service.history.file.name.convention,mosip.resident.download.nearest.registration.centre.file.name.convention,auth.internal.id,auth.internal.version,mosip.registration.processor.print.id,mosip.registration.processor.application.version,vid.create.id,mosip.resident.create.vid.version,resident.vid.version,resident.vid.version.new,resident.revokevid.version,resident.revokevid.version.new,resident.vid.id,resident.vid.id.generate,resident.vid.policy.id,resident.vid.get.id,auth.type.status.id,resident.authlock.id,resident.checkstatus.id,resident.checkstatus.version,resident.euin.id,resident.printuin.id,resident.uin.id,resident.rid.id,resident.updateuin.id,resident.authunlock.id,resident.authhistory.id,resident.authLockStatusUpdateV2.id,resident.authLockStatusUpdateV2.version,resident.service.history.id,resident.service.history.version,resident.document.upload.id,resident.document.get.id,resident.document.get.version,resident.document.list.id,resident.document.list.version,resident.service.pin.status.id,resident.service.pin.status.version,resident.service.unpin.status.id,resident.service.unpin.status.version,resident.document.delete.id,resident.document.delete.version,resident.contact.details.update.id,resident.contact.details.send.otp.id,mosip.resident.service.status.check.id,mosip.resident.service.status.check.version,resident.service.unreadnotificationlist.id,resident.service.event.id,resident.service.event.version,resident.identity.info.id,resident.identity.info.version,resident.share.credential.id,resident.share.credential.version,mosip.resident.request.response.version,vid.revoke.id,resident.revokevid.id,mosip.resident.revokevid.id,mosip.resident.grievance.ticket.request.id,mosip.resident.grievance.ticket.request.version,resident.channel.verification.status.id,resident.channel.verification.status.version,resident.event.ack.download.id,resident.event.ack.download.version,resident.download.card.eventid.id ,resident.download.card.eventid.version,mosip.resident.request.vid.card.id,mosip.resident.request.vid.card.version,mosip.credential.request.service.id,mosip.credential.request.service.version,mosip.resident.checkstatus.individualid.id,mosip.resident.checkstatus.individualid.version,mosip.resident.download.personalized.card.id,mosip.resident.transliteration.transliterate.id,resident.ui.properties.id,resident.ui.properties.version,resident.nearby.centers.distance.meters,resident.ui.notification.update.interval.seconds,mosip.kernel.otp.expiry-time,resident.grievance-redressal.alt-email.chars.limit,resident.grievance-redressal.alt-phone.chars.limit,resident.grievance-redressal.comments.chars.limit,resident.share-credential.purpose.chars.limit,mosip.resident.eventid.searchtext.length,mosip.kernel.uin.length,mosip.kernel.vid.length,mosip.kernel.rid.length,mosip.resident.eid.length,mosip.kernel.otp.default-length,resident.message.allowed.special.char.regex,resident.purpose.allowed.special.char.regex,resident.id.allowed.special.char.regex,resident.version.new,mosip.resident.identity.auth.internal.id,resident.validation.event-id.regex,resident.document.validation.transaction-id.regex,resident.document.validation.document-id.regex,resident.validation.is-numeric.regex,resident.otp.validation.transaction-id.regex,,mosip.resident.captcha.enable,resident.download.reg.centers.list.id,resident.download.nearest.reg.centers.id,resident.download.supporting.documents.id,resident.send.card.id,resident.pinned.eventid.id,resident.unpinned.eventid.id,resident.auth.proxy.partners.id,resident.events.eventid.id,resident.notification.id,resident.profile.id,resident.notification.click.id,mosip.credential.store.id,resident.vids.id,mosip.resident.zoom,mosip.resident.maxZoom,mosip.resident.minZoomauth.allowed.urls=https://${mosip.resident.host}/,https://${mosip.resident.host}/resident-ui/,https://${mosip.resident.host}/resident-ui/**When enabling MOSIP eSignet comment Mock Keycloak config, vise versa.
mosip.iam.module.clientID=******
mosip.iam.module.clientsecret=
mosip.iam.base.url=https://${mosip.esignet.host}/v1/esignet
mosip.iam.authorization_endpoint=https://${mosip.esignet.host}/authorize
mosip.iam.token_endpoint=${mosip.iam.base.url}/oauth/v2/token
mosip.iam.userinfo_endpoint=${mosip.iam.base.url}/oidc/userinfo
mosip.iam.certs_endpoint=${mosip.iam.base.url}/oauth/.well-known/jwks.json
auth.server.admin.issuer.uri=${mosip.iam.base.url}
auth.server.admin.issuer.domain.validate=true
auth.server.admin.oidc.userinfo.url=${mosip.iam.userinfo_endpoint}
mosip.iam.module.token.endpoint.private-key-jwt.auth.enabled=true
mosip.iam.module.token.endpoint.private-key-jwt.expiry.seconds=7200
mosip.resident.oidc.userinfo.jwt.signed=trueThis property will directly apply the certs URL without the need for constructing the path from the issuer URL. This is useful to keep a different certs URL for integrating with MOSIP IDP for offline token validation.
auth.server.admin.oidc.certs.url=${mosip.iam.certs_endpoint}
mosip.iam.logout.offline=true
auth.server.admin.validate.url=
mosip.resident.oidc.userinfo.jwt.verify.enabled=falsemosip.iam.module.redirecturi=${mosip.api.internal.url}/resident/v1/login-redirect/
mosip.iam.module.login_flow.name=authorization_code
mosip.iam.module.login_flow.scope=openid profile Manage-Identity-Data Manage-VID Manage-Authentication Manage-Service-Requests Manage-Credentials
mosip.iam.module.login_flow.claims={"userinfo":{"name":{"essential":true},"picture":{"essential":true},"email":{"essential":true},"phone_number":{"essential":true},"individual_id":{"essential":true}}}
mosip.iam.module.login_flow.response_type=code
mosip.iam.module.admin_realm_id=mosipUsed in open-id-connect based login with UIN/VID in MOSIP-IDP
mosip.resident.identity.claim.individual-id=individual_id
mosip.resident.identity.claim.ida-token=ida_tokenUsed for login purposes
mosip.scope.resident.getinputattributevalues=Manage-Identity-Data
mosip.scope.resident.patchrevokevid=Manage-VID
mosip.scope.resident.postgeneratevid=Manage-VID
mosip.scope.resident.getvids=Manage-VID
mosip.scope.resident.getAuthTransactions=Manage-Service-Requests
mosip.scope.resident.postAuthTypeUnlock=Manage-Authentication
mosip.scope.resident.postAuthTypeStatus=Manage-Authentication
mosip.scope.resident.getAuthLockStatus=Manage-Authentication
mosip.scope.resident.patchUpdateUin=Manage-Identity-Data
mosip.scope.resident.getServiceAuthHistoryRoles=Manage-Service-Requests
mosip.scope.resident.postSendPhysicalCard=Manage-Credentials
mosip.scope.resident.getUnreadServiceList=Manage-Service-Requests
mosip.scope.resident.getNotificationCount=
mosip.scope.resident.getNotificationClick=Manage-Service-Requests
mosip.scope.resident.getupdatedttimes=Manage-Service-Requests
mosip.scope.resident.postRequestDownloadPersonalizedCard=Manage-Credentials
mosip.scope.resident.postRequestShareCredWithPartner=Manage-Credentials
mosip.scope.resident.postUnPinStatus=Manage-Service-Requests
mosip.scope.resident.postPinStatus=Manage-Service-Requests
mosip.scope.resident.getDownloadCard=Manage-Credentials
mosip.scope.resident.postPersonalizedCard=Manage-Credentials
mosip.scope.resident.getOrderRedirect=Manage-CredentialsProperties used to define application and reference id.
APPLICATION_Id=RESIDENT
PARTNER_REFERENCE_Id=mpartner-default-resident
mosip.resident.keymanager.application-name=RESIDENT
mosip.resident.keymanager.reference-id=resident_document
mosip.datashare.application.id=PARTNER
mosip.datashare.reference.id=mparter-default-euin
mosip.resident.oidc.keymanager.reference.id=IDP_USER_INFO
mosip.resident.sign.pdf.application.id=KERNEL
mosip.resident.sign.pdf.reference.id=SIGNTo configure the 'Object Store Configuration', update the 'Object Store URL' and other properties as below:
object.store.s3.url=
mosip.resident.object.store.account-name=resident
mosip.resident.object.store.bucket-name=resident
mosip.resident.object.store.adapter-name=s3Adapter
object.store.s3.use.account.as.bucketname=true
object.store.s3.accesskey=******
object.store.s3.secretkey=******
object.store.s3.url=http://minio.minio:9000
object.store.s3.region=${s3.region}
object.store.s3.readlimit=10000000Property used whether to enable virus scanner flag
mosip.resident.virus-scanner.enabled=trueProperty used to get the vid policy json
mosip.resident.vid-policy-url=${config.server.file.storage.uri}mosip-vid-policy.jsonProperty used to get the UI schema json
resident-ui-schema-file-name-prefix=resident-ui
resident-ui-schema-file-url=${config.server.file.storage.uri}${resident-ui-schema-file-name-prefix}
resident-ui-schema-file-source-prefix=url:${resident-ui-schema-file-url}Property used to get the identity mapping json
identity-mapping-file-name=identity-mapping.json
identity-mapping-file-url=${config.server.file.storage.uri}${identity-mapping-file-name}
identity-mapping-file-source=url:${identity-mapping-file-url}This property is used to get the data format from MVEL file
resident-data-format-mvel-file-name=credentialdata.mvel
resident-data-format-mvel-file-url=${config.server.file.storage.uri}${resident-data-format-mvel-file-name}
resident-data-format-mvel-file-source=url:${resident-data-format-mvel-file-url}Below websub properties used for authentication type status event
resident.websub.authtype-status.secret=******
resident.websub.authtype-status.topic=AUTH_TYPE_STATUS_UPDATE_ACK
resident.websub.callback.authtype-status.relative.url=${server.servlet.context-path}/callback/authTypeCallback
resident.websub.callback.authtype-status.url=${mosip.api.internal.url}${resident.websub.callback.authtype-status.relative.url}Below websub properties used for authentication transaction status event
resident.websub.authTransaction-status.secret=******
resident.websub.authTransaction-status.topic=AUTHENTICATION_TRANSACTION_STATUS
resident.websub.callback.authTransaction-status.relative.url=${server.servlet.context-path}/callback/authTransaction
resident.websub.callback.authTransaction-status.url=${mosip.api.internal.url}${resident.websub.callback.authTransaction-status.relative.url}Below websub properties used for credential status event
resident.websub.credential-status.secret=******
resident.websub.credential-status.topic=CREDENTIAL_STATUS_UPDATE
resident.websub.callback.credential-status.relative.url=${server.servlet.context-path}/callback/credentialStatusUpdate
resident.websub.callback.credential-status.url=${mosip.api.internal.url}${resident.websub.callback.credential-status.relative.url}Below websub properties used for regproc complete workflow event
resident.websub.regproc.workflow.complete.secret=*****
mosip.regproc.workflow.complete.topic=REGISTRATION_PROCESSOR_WORKFLOW_COMPLETED_EVENT
resident.websub.callback.regproc.workflow.complete.relative.url=${server.servlet.context-path}/callback/regprocworkflow
resident.websub.callback.regproc.workflow.complete.url=${mosip.api.internal.url}${resident.websub.callback.regproc.workflow.complete.relative.url}mosip.kernel.tokenid.uin.salt=******
mosip.kernel.tokenid.partnercode.salt=******Properties used to get the data format from MVEL file.
resident.email.mask.function=maskEmail
resident.phone.mask.function=maskPhone
resident.data.mask.function=convertToMaskDatamosip.resident.update.service.status.job.enabled=false
mosip.resident.update.service.status.job.initial-delay=60000
#Interval for checking the credential status for async requests. Note, this is done as a fallback though credential status update is hanlded in resident service via websub notification.
mosip.resident.update.service.status.job.interval.millisecs=600000resident.template.email.subject.request-received.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-request-received-email-subject
resident.template.email.subject.success.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-success-email-subject
resident.template.email.subject.failure.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-failure-email-subject
resident.template.email.subject.request-received.ORDER_PHYSICAL_CARD=order-a-physical-card-request-received-email-subject
resident.template.email.subject.success.ORDER_PHYSICAL_CARD=order-a-physical-card-success-email-subject
resident.template.email.subject.failure.ORDER_PHYSICAL_CARD=order-a-physical-card-failure-email-subject
resident.template.email.subject.request-received.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-request-received-email-subject
resident.template.email.subject.success.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-success-email-subject
resident.template.email.subject.failure.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-failure-email-subject
resident.template.email.subject.request-received.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-request-received-email-subject
resident.template.email.subject.success.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-success-email-subject
resident.template.email.subject.failure.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-failure-email-subject
resident.template.email.subject.request-received.UPDATE_MY_UIN=update-demo-data-request-received-email-subject
resident.template.email.subject.success.UPDATE_MY_UIN=update-demo-data-success-email-subject
resident.template.email.subject.failure.UPDATE_MY_UIN=update-demo-data-failure-email-subject
resident.template.email.subject.regproc-success.UPDATE_MY_UIN=update-demo-data-regproc-success-email-subject
resident.template.email.subject.regproc-failure.UPDATE_MY_UIN=update-demo-data-regproc-failure-email-subject
resident.template.email.subject.cancelled.UPDATE_MY_UIN=update-demo-data-discarded-email-subject
resident.template.email.subject.request-received.GENERATE_VID=gen-or-revoke-vid-request-received-email-subject
resident.template.email.subject.success.GENERATE_VID=gen-or-revoke-vid-success-email-subject
resident.template.email.subject.failure.GENERATE_VID=gen-or-revoke-vid-failure-email-subject
resident.template.email.subject.request-received.REVOKE_VID=gen-or-revoke-vid-request-received-email-subject
resident.template.email.subject.success.REVOKE_VID=gen-or-revoke-vid-success-email-subject
resident.template.email.subject.failure.REVOKE_VID=gen-or-revoke-vid-failure-email-subject
resident.template.email.subject.request-received.VID_CARD_DOWNLOAD=vid-card-download-request-received-email-subject
resident.template.email.subject.success.VID_CARD_DOWNLOAD=vid-card-download-success-email-subject
resident.template.email.subject.failure.VID_CARD_DOWNLOAD=vid-card-download-failure-email-subject
resident.template.email.subject.request-received.GET_MY_ID=get-my-uin-card-request-received-email-subject
resident.template.email.subject.success.GET_MY_ID=get-my-uin-card-success-email-subject
resident.template.email.subject.failure.GET_MY_ID=get-my-uin-card-failure-email-subject
resident.template.email.subject.request-received.VALIDATE_OTP=verify-my-phone-email-request-received-email-subject
resident.template.email.subject.success.VALIDATE_OTP=verify-my-phone-email-success-email-subject
resident.template.email.subject.failure.VALIDATE_OTP=verify-my-phone-email-failure-email-subject
resident.template.email.subject.success.SEND_OTP=receive-otp-mail-subjectresident.template.email.content.request-received.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-request-received-email-content
resident.template.email.content.success.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-success-email-content
resident.template.email.content.failure.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-failure-email-content
resident.template.email.content.request-received.ORDER_PHYSICAL_CARD=order-a-physical-card-request-received-email-content
resident.template.email.content.success.ORDER_PHYSICAL_CARD=order-a-physical-card-success-email-content
resident.template.email.content.failure.ORDER_PHYSICAL_CARD=order-a-physical-card-failure-email-content
resident.template.email.content.request-received.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-request-received-email-content
resident.template.email.content.success.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-success-email-content
resident.template.email.content.failure.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-failure-email-content
resident.template.email.content.request-received.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-request-received-email-content
resident.template.email.content.success.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-success-email-content
resident.template.email.content.failure.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-failure-email-content
resident.template.email.content.request-received.UPDATE_MY_UIN=update-demo-data-request-received-email-content
resident.template.email.content.success.UPDATE_MY_UIN=update-demo-data-success-email-content
resident.template.email.content.failure.UPDATE_MY_UIN=update-demo-data-failure-email-content
resident.template.email.content.regproc-success.UPDATE_MY_UIN=update-demo-data-regproc-success-email-content
resident.template.email.content.regproc-failure.UPDATE_MY_UIN=update-demo-data-regproc-failure-email-content
resident.template.email.content.cancelled.UPDATE_MY_UIN=update-demo-data-discarded-email-content
resident.template.email.content.request-received.GENERATE_VID=gen-or-revoke-vid-request-received-email-content
resident.template.email.content.success.GENERATE_VID=gen-or-revoke-vid-success-email-content
resident.template.email.content.failure.GENERATE_VID=gen-or-revoke-vid-failure-email-content
resident.template.email.content.request-received.REVOKE_VID=gen-or-revoke-vid-request-received-email-content
resident.template.email.content.success.REVOKE_VID=gen-or-revoke-vid-success-email-content
resident.template.email.content.failure.REVOKE_VID=gen-or-revoke-vid-failure-email-content
resident.template.email.content.request-received.VID_CARD_DOWNLOAD=vid-card-download-request-received-email-content
resident.template.email.content.success.VID_CARD_DOWNLOAD=vid-card-download-success-email-content
resident.template.email.content.failure.VID_CARD_DOWNLOAD=vid-card-download-failure-email-content
resident.template.email.content.request-received.GET_MY_ID=get-my-uin-card-request-received-email-content
resident.template.email.content.success.GET_MY_ID=get-my-uin-card-success-email-content
resident.template.email.content.failure.GET_MY_ID=get-my-uin-card-failure-email-content
resident.template.email.content.request-received.VALIDATE_OTP=verify-my-phone-email-request-received-email-content
resident.template.email.content.success.VALIDATE_OTP=verify-my-phone-email-success-email-content
resident.template.email.content.failure.VALIDATE_OTP=verify-my-phone-email-failure-email-content
resident.template.email.content.success.SEND_OTP=receive-otp-mail-contentresident.template.sms.request-received.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-request-received_SMS
resident.template.sms.success.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-success_SMS
resident.template.sms.failure.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-failure_SMS
resident.template.sms.request-received.ORDER_PHYSICAL_CARD=order-a-physical-card-request-received_SMS
resident.template.sms.success.ORDER_PHYSICAL_CARD=order-a-physical-card-success_SMS
resident.template.sms.failure.ORDER_PHYSICAL_CARD=order-a-physical-card-failure_SMS
resident.template.sms.request-received.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-request-received_SMS
resident.template.sms.success.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-success_SMS
resident.template.sms.failure.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-failure_SMS
resident.template.sms.request-received.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-request-received_SMS
resident.template.sms.success.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-success_SMS
resident.template.sms.failure.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-failure_SMS
resident.template.sms.request-received.UPDATE_MY_UIN=update-demo-data-request-received_SMS
resident.template.sms.success.UPDATE_MY_UIN=update-demo-data-success_SMS
resident.template.sms.failure.UPDATE_MY_UIN=update-demo-data-failure_SMS
resident.template.sms.regproc-success.UPDATE_MY_UIN=update-demo-data-regproc-success_SMS
resident.template.sms.regproc-failure.UPDATE_MY_UIN=update-demo-data-regproc-failure_SMS
resident.template.sms.cancelled.UPDATE_MY_UIN=update-demo-data-discarded-SMS
resident.template.sms.request-received.GENERATE_VID=gen-or-revoke-vid-request-received_SMS
resident.template.sms.success.GENERATE_VID=gen-or-revoke-vid-success_SMS
resident.template.sms.failure.GENERATE_VID=gen-or-revoke-vid-failure_SMS
resident.template.sms.request-received.REVOKE_VID=gen-or-revoke-vid-request-received_SMS
resident.template.sms.success.REVOKE_VID=gen-or-revoke-vid-success_SMS
resident.template.sms.failure.REVOKE_VID=gen-or-revoke-vid-failure_SMS
resident.template.sms.request-received.VID_CARD_DOWNLOAD=vid-card-download-request-received_SMS
resident.template.sms.success.VID_CARD_DOWNLOAD=vid-card-download-success_SMS
resident.template.sms.failure.VID_CARD_DOWNLOAD=vid-card-download-failure_SMS
resident.template.sms.request-received.GET_MY_ID=get-my-uin-card-request-received_SMS
resident.template.sms.success.GET_MY_ID=get-my-uin-card-success_SMS
resident.template.sms.failure.GET_MY_ID=get-my-uin-card-failure_SMS
resident.template.sms.request-received.VALIDATE_OTP=verify-my-phone-email-request-received_SMS
resident.template.sms.success.VALIDATE_OTP=verify-my-phone-email-success_SMS
resident.template.sms.failure.VALIDATE_OTP=verify-my-phone-email-failure_SMS
resident.template.sms.success.SEND_OTP=receive-otpresident.template.purpose.success.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-positive-purpose
resident.template.purpose.success.ORDER_PHYSICAL_CARD=order-a-physical-card-positive purpose
resident.template.purpose.success.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-positive-purpose
resident.template.purpose.success.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-positive-purpose
resident.template.purpose.success.UPDATE_MY_UIN=update-demo-data-positive-purpose
resident.template.purpose.success.GENERATE_VID=gen-or-revoke-vid-positive-purpose
resident.template.purpose.success.REVOKE_VID=gen-or-revoke-vid-positive-purpose
resident.template.purpose.success.GET_MY_ID=get-my-uin-card-positive-purpose
resident.template.purpose.success.VALIDATE_OTP=verify-my-phone-email-positive-purpose
resident.template.purpose.success.VID_CARD_DOWNLOAD=vid-card-download-positive-purposeresident.template.purpose.failure.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-negative-purpose
resident.template.purpose.failure.ORDER_PHYSICAL_CARD=order-a-physical-card-negative purpose
resident.template.purpose.failure.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-negative-purpose
resident.template.purpose.failure.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-negative-purpose
resident.template.purpose.failure.UPDATE_MY_UIN=update-demo-data-negative-purpose
resident.template.purpose.failure.GENERATE_VID=gen-or-revoke-vid-negative-purpose
resident.template.purpose.failure.REVOKE_VID=gen-or-revoke-vid-negative-purpose
resident.template.purpose.failure.GET_MY_ID=get-my-uin-card-negative-purpose
resident.template.purpose.failure.VALIDATE_OTP=verify-my-phone-email-negative-purpose
resident.template.purpose.failure.VID_CARD_DOWNLOAD=vid-card-download-negative-purpose
resident.template.purpose.failure.AUTHENTICATION_REQUEST=authentication-request-negative-purposeresident.template.purpose.cancelled.UPDATE_MY_UIN=update-demo-data-cancelled-purposeresident.template.purpose.regproc-success.UPDATE_MY_UIN=update-demo-data-regproc-success-purposeresident.template.summary.success.DOWNLOAD_PERSONALIZED_CARD=cust-and-down-my-card-success-summary
resident.template.summary.success.ORDER_PHYSICAL_CARD=order-a-physical-card-success-summary
resident.template.summary.success.SHARE_CRED_WITH_PARTNER=share-cred-with-partner-success-summary
resident.template.summary.success.AUTH_TYPE_LOCK_UNLOCK=lock-unlock-auth-success-summary
resident.template.summary.success.UPDATE_MY_UIN=update-demo-data-success-summary
resident.template.summary.success.GENERATE_VID=gen-or-revoke-vid-success-summary
resident.template.summary.success.REVOKE_VID=gen-or-revoke-vid-success-summary
resident.template.summary.success.GET_MY_ID=get-my-uin-card-success-summary
resident.template.summary.success.VALIDATE_OTP=verify-my-phone-email-success-summary
resident.template.summary.success.VID_CARD_DOWNLOAD=vid-card-download-positive-summary
resident.template.summary.success.AUTHENTICATION_REQUEST=authentication-request-positive-summaryresident.template.summary.cancelled.UPDATE_MY_UIN=update-demo-data-cancelled-summaryresident.template.summary.regproc-success.UPDATE_MY_UIN=update-demo-data-regproc-success-summaryresident.template.ack.share-cred-with-partner=acknowledgement-share-cred-with-partner
resident.template.ack.manage-my-vid=acknowledgement-manage-my-vid
resident.template.ack.order-a-physical-card=acknowledgement-order-a-physical-card
resident.template.ack.download-a-personalized-card=acknowledgement-download-a-personalized-card
resident.template.ack.update-demographic-data=acknowledgement-update-demographic-data
resident.template.ack.verify-email-id-or-phone-number=acknowledgement-verify-email-id-or-phone-number
resident.template.ack.secure-my-id=acknowledgement-secure-my-id
resident.template.ack.authentication.request=acknowledgment-authentication-request
resident.template.ack.get.my.id=acknowledgment-get-my-id
resident.template.ack.vid.card.download=acknowledgment-vid-card-downloadresident.template.support-docs-list=supporting-docs-list
mosip.resident.service.history.template.type.code=service-history-type
resident.template.registration.centers.list=registration-centers-list
mosip.resident.vid.card.template.property=vid-card-typeresident.template.date.pattern=dd-MM-yyyy
resident.template.time.pattern=HH:mm:ss
resident.ui.track-service-request-url=https://${mosip.resident.host}/#/uinservices/trackservicerequest?eid=resident.view.history.serviceType.filters=ALL,AUTHENTICATION_REQUEST,SERVICE_REQUEST,DATA_UPDATE_REQUEST,ID_MANAGEMENT_REQUEST,DATA_SHARE_REQUEST
resident.view.history.status.filters=ALL,SUCCESS,IN_PROGRESS,FAILED,CANCELEDresident.service-history.download.max.count=100
resident.registration-centers.download.max.count=100resident.nearby.centers.distance.meters=2000resident.notifications.default.page.size=100
resident.view-history.default.page.size=10auth.validate.id-token=true
idToken=id_token
auth.token.header=Authorization
mosip.resident.access_token.auth_mode.claim-name=acr
mosip.resident.oidc.id_token.ida_token.claim-name=sub
mosip.resident.oidc.auth_token.expiry.claim-name=exp
mosip.resident.oidc.userinfo.encryption.enabled=false
mosip.client.assertion.reference.id=
mosip.include.payload=true
mosip.include.certificate=true
mosip.include.cert.hash=falsemosip.resident.service.uincard.lowerleftx=73
mosip.resident.service.uincard.lowerlefty=100
mosip.resident.service.uincard.upperrightx=300
mosip.resident.service.uincard.upperrighty=300
mosip.resident.service.uincard.signature.reason="Digitally Signed"mosip.resident.download.registration.centre.file.name.convention=Registration_centers_{timestamp}
mosip.resident.download.supporting.document.file.name.convention=Supporting_documents_{timestamp}
mosip.resident.download.personalized.card.naming.convention=Personalised_card_{eventId}_{timestamp}
mosip.resident.ack.manage_my_vid.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.secure_my_id.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.personalised_card.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.update_my_data.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.share_credential.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.order_physical_card.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.ack.name.convention=Ack_{featureName}_{eventId}_{timestamp}
mosip.resident.uin.card.name.convention=UIN_{eventId}_{timestamp}
mosip.resident.vid.card.name.convention=VID_{eventId}_{timestamp}
mosip.resident.download.service.history.file.name.convention=View_history_{timestamp}
mosip.resident.download.nearest.registration.centre.file.name.convention=Registration_centers_{timestamp}
mosip.resident.download.card.naming.convention=Get_my_UIN_{timestamp}mosip.resident.request.credential.credentialType=vercred
mosip.resident.request.credential.credentialType=euin
mosip.resident.request.credential.isEncrypt=true
mosip.resident.request.credential.encryption.key=******
mosip.digital.card.credential.type=PDFCard
mosip.credential.issuer=******mosip.resident.name.token.claim-name=name
mosip.resident.photo.token.claim-photo=picture
mosip.resident.individual.id.claim.name=individual_id
mosip.resident.email.token.claim-email=email
mosip.resident.phone.token.claim-phone=phone_numberotpChannel.email=email
otpChannel.mobile=phone
mosip.idrepo.vid.reactive-status=ACTIVE
resident.dateofbirth.pattern=yyyy/MM/dd
mosip.resident.photo.attribute.name=photo
mosip.resident.order.card.payment.enabled=true
resident.update.preferred.language.by.name=true
resident.documents.category=individualBiometrics
mosip.resident.schema.attribute-name=attributeName
mosip.resident.applicant.name.property=applicantName
mosip.resident.authentication.mode.property=authenticationMode
resident.attribute.names.without.documents.required=preferredLanguage,email,phone
resident.additional.identity.attribute.to.fetch=UIN,email,phone,dateOfBirth,fullName,photoConfigure Time limit for OTP Flooding scenario (in minutes).
otp.request.flooding.duration=1
otp.request.flooding.max-count=10mosip.max.file.upload.size.in.bytes=2306867
mosip.allowed.extension=pdf,jpeg,png,jpgresident.success.packet-status-code.list=PROCESSED,SUCCESS,UIN_GENERATED
resident.in-progress.packet-status-code.list=PROCESSING,REREGISTER,RESEND,RECEIVED,UPLOAD_PENDING,AWAITING_INFORMATION,REPROCESS
resident.failure.packet-status-code.list=REJECTED,FAILED,REPROCESS_FAILEDresident.REQUEST_RECEIVED.packet-transaction-type-code.list=PACKET_RECEIVER,VIRUS_SCAN,SECUREZONE_NOTIFICATION,UPLOAD_PACKET,VALIDATE_PACKET,PACKET_CLASSIFICATION
resident.VALIDATION_STAGE.packet-transaction-type-code.list=CMD_VALIDATION,OPERATOR_VALIDATION,QUALITY_CLASSIFIER,SUPERVISOR_VALIDATION,INTRODUCER_VALIDATION,BIOMETRIC_AUTHENTICATION,EXTERNAL_INTEGRATION
resident.VERIFICATION_STAGE.packet-transaction-type-code.list=DEMOGRAPHIC_VERIFICATION,MANUAL_ADJUDICATION,VERIFICATION,BIOGRAPHIC_VERIFICATION
resident.UIN_GENERATION_STAGE.packet-transaction-type-code.list=UIN_GENERATOR,BIOMETRIC_EXTRACTION,NOTIFICATION,FINALIZATION,PACKET_REPROCESS
resident.CARD_READY_TO_DOWNLOAD.packet-transaction-type-code.list=PRINT_SERVICE,PRINT_POSTAL_SERVICE,PRINTsequence-order=Request received, Validation stage, Verification stage, Uin generation stage, Card ready to downloadresident.request.success.status.list.AUTHENTICATION_REQUEST=AUTHENTICATION_SUCCESSFUL,Y
resident.request.failed.status.list.AUTHENTICATION_REQUEST=AUTHENTICATION_FAILED,N
resident.request.cancelled.status.list.AUTHENTICATION_REQUEST=
resident.request.new.status.list.DOWNLOAD_PERSONALIZED_CARD=NEW
resident.batchjob.process.success.status.list.DOWNLOAD_PERSONALIZED_CARD=CARD_DOWNLOADED
resident.request.failed.status.list.DOWNLOAD_PERSONALIZED_CARD=FAILED
resident.request.cancelled.status.list.DOWNLOAD_PERSONALIZED_CARD=
resident.request.new.status.list.GET_MY_ID=NEW
resident.request.in-progress.status.list.GET_MY_ID=OTP_REQUESTED
resident.request.success.status.list.GET_MY_ID=CARD_DOWNLOADED,OTP_VERIFIED
resident.request.failed.status.list.GET_MY_ID=FAILED
resident.request.cancelled.status.list.GET_MY_ID=
resident.request.new.status.list.BOOK_AN_APPOINTMENT=
resident.request.success.status.list.BOOK_AN_APPOINTMENT=
resident.request.failed.status.list.BOOK_AN_APPOINTMENT=
resident.request.cancelled.status.list.BOOK_AN_APPOINTMENT=
resident.request.new.status.list.GENERATE_VID=NEW
resident.request.success.status.list.GENERATE_VID=VID_GENERATED
resident.request.failed.status.list.GENERATE_VID=FAILED
resident.request.cancelled.status.list.GENERATE_VID=
resident.request.new.status.list.REVOKE_VID=NEW
resident.request.success.status.list.REVOKE_VID=VID_REVOKED
resident.request.failed.status.list.REVOKE_VID=FAILED
resident.request.cancelled.status.list.REVOKE_VID=
resident.request.new.status.list.SEND_OTP=
resident.request.success.status.list.SEND_OTP=
resident.request.failed.status.list.SEND_OTP=
resident.request.cancelled.status.list.SEND_OTP=
resident.request.new.status.list.VALIDATE_OTP=OTP_REQUESTED
resident.request.success.status.list.VALIDATE_OTP=OTP_VERIFIED
resident.request.failed.status.list.VALIDATE_OTP=OTP_VERIFICATION_FAILED
resident.request.cancelled.status.list.VALIDATE_OTP=
resident.request.new.status.list.DEFAULT=
resident.request.success.status.list.DEFAULT=
resident.request.failed.status.list.DEFAULT=
resident.request.cancelled.status.list.DEFAULT=resident.async.request.types=VID_CARD_DOWNLOAD,ORDER_PHYSICAL_CARD,SHARE_CRED_WITH_PARTNER,UPDATE_MY_UINresident.request.new.status.list.SHARE_CRED_WITH_PARTNER=NEW
resident.request.in-progress.status.list.SHARE_CRED_WITH_PARTNER=ISSUED
resident.request.success.status.list.SHARE_CRED_WITH_PARTNER=RECEIVED,DATA_SHARED_SUCCESSFULLY,STORED
resident.request.failed.status.list.SHARE_CRED_WITH_PARTNER=FAILED
resident.request.notification.status.list.SHARE_CRED_WITH_PARTNER=FAILED,RECEIVED,DATA_SHARED_SUCCESSFULLY,STORED
resident.request.new.status.list.ORDER_PHYSICAL_CARD=NEW
resident.request.in-progress.status.list.ORDER_PHYSICAL_CARD=PAYMENT_CONFIRMED,ISSUED,PRINTING,IN_TRANSIT
resident.request.success.status.list.ORDER_PHYSICAL_CARD=CARD_DELIVERED
resident.request.failed.status.list.ORDER_PHYSICAL_CARD=FAILED,PAYMENT_FAILED
resident.request.notification.status.list.ORDER_PHYSICAL_CARD=PAYMENT_CONFIRMED,ISSUED,PRINTING,IN_TRANSIT,CARD_DELIVERED,FAILED,PAYMENT_FAILED,CARD_DELIVERED
resident.request.new.status.list.UPDATE_MY_UIN=NEW
resident.request.in-progress.status.list.UPDATE_MY_UIN=PROCESSING,PAUSED,RESUMABLE,REPROCESS,PAUSED_FOR_ADDITIONAL_INFO
resident.request.success.status.list.UPDATE_MY_UIN=PROCESSED,DATA_UPDATED,STORED,CARD_READY_TO_DOWNLOAD,CARD_DOWNLOADED
resident.request.failed.status.list.UPDATE_MY_UIN=FAILED,REJECTED,REPROCESS_FAILED
resident.request.notification.status.list.UPDATE_MY_UIN=PROCESSED,DATA_UPDATED,STORED,CARD_READY_TO_DOWNLOAD,CARD_DOWNLOADED,FAILED,REJECTED,REPROCESS_FAILED
resident.request.new.status.list.AUTH_TYPE_LOCK_UNLOCK=NEW
resident.request.in-progress.status.list.AUTH_TYPE_LOCK_UNLOCK=
resident.request.success.status.list.AUTH_TYPE_LOCK_UNLOCK=COMPLETED
resident.request.failed.status.list.AUTH_TYPE_LOCK_UNLOCK=FAILED
resident.request.notification.status.list.AUTH_TYPE_LOCK_UNLOCK=COMPLETED,FAILED
resident.request.new.status.list.VID_CARD_DOWNLOAD=NEW
resident.request.in-progress.status.list.VID_CARD_DOWNLOAD=ISSUED
resident.request.success.status.list.VID_CARD_DOWNLOAD=STORED,CARD_READY_TO_DOWNLOAD,CARD_DOWNLOADED
resident.request.failed.status.list.VID_CARD_DOWNLOAD=FAILED
resident.request.notification.status.list.VID_CARD_DOWNLOAD=STORED,CARD_READY_TO_DOWNLOAD,CARD_DOWNLOADED,FAILEDDefine property name in below format- resident.<attribute name>.template.property.attribute.list
resident.PHONE.template.property.attribute.list=mosip.phone.template.property
resident.EMAIL.template.property.attribute.list=mosip.email.template.property
resident.GENERATE_VID.template.property.attribute.list=mosip.generated.template.property
resident.REVOKE_VID.template.property.attribute.list=mosip.revoked.template.propertyresident.event.status.SUCCESS.template.property=mosip.event.status.success.template
resident.event.status.FAILED.template.property=mosip.event.status.failed.template
resident.event.status.IN_PROGRESS.template.property=mosip.event.status.inprogress.template
resident.event.status.CANCELED.template.property=mosip.event.status.cancelled.templateDefine property name in below format- resident.event.type.<eventType>.template.property
resident.event.type.AUTHENTICATION_REQUEST.template.property=mosip.event.type.AUTHENTICATION_REQUEST
resident.event.type.SHARE_CRED_WITH_PARTNER.template.property=mosip.event.type.SHARE_CRED_WITH_PARTNER
resident.event.type.DOWNLOAD_PERSONALIZED_CARD.template.property=mosip.event.type.DOWNLOAD_PERSONALIZED_CARD
resident.event.type.ORDER_PHYSICAL_CARD.template.property=mosip.event.type.ORDER_PHYSICAL_CARD
resident.event.type.GET_MY_ID.template.property=mosip.event.type.GET_MY_ID
resident.event.type.UPDATE_MY_UIN.template.property=mosip.event.type.UPDATE_MY_UIN
resident.event.type.GENERATE_VID.template.property=mosip.event.type.GENERATE_VID
resident.event.type.REVOKE_VID.template.property=mosip.event.type.REVOKE_VID
resident.event.type.AUTH_TYPE_LOCK_UNLOCK.template.property=mosip.event.type.AUTH_TYPE_LOCK_UNLOCK
resident.event.type.VID_CARD_DOWNLOAD.template.property=mosip.event.type.VID_CARD_DOWNLOAD
resident.event.type.SEND_OTP.template.property=mosip.event.type.SEND_OTP
resident.event.type.VALIDATE_OTP.template.property=mosip.event.type.VALIDATE_OTP
resident.event.type.DEFAULT.template.property=mosip.event.type.DEFAULTDefine property name in below format- resident.service-type.<serviceType>.template.property
resident.service-type.AUTHENTICATION_REQUEST.template.property=mosip.service.type.AUTHENTICATION_REQUEST
resident.service-type.SERVICE_REQUEST.template.property=mosip.service.type.SERVICE_REQUEST
resident.service-type.DATA_UPDATE_REQUEST.template.property=mosip.service.type.DATA_UPDATE_REQUEST
resident.service-type.ID_MANAGEMENT_REQUEST.template.property=mosip.service.type.ID_MANAGEMENT_REQUEST
resident.service-type.DATA_SHARE_REQUEST.template.property=mosip.service.type.DATA_SHARE_REQUEST
resident.service-type.ASYNC.template.property=mosip.service.type.ASYNCDefine property name in below format- resident.id-auth.request-type.<authTypeCode>.<statusCode>.descr
resident.id-auth.request-type.OTP-REQUEST.SUCCESS.descr=mosip.ida.auth-request.OTP-REQUEST.Y.descr
resident.id-auth.request-type.OTP-AUTH.SUCCESS.descr=mosip.ida.auth-request.OTP-AUTH.Y.descr
resident.id-auth.request-type.DEMO-AUTH.SUCCESS.descr=mosip.ida.auth-request.DEMO-AUTH.Y.descr
resident.id-auth.request-type.FINGERPRINT-AUTH.SUCCESS.descr=mosip.ida.auth-request.FINGERPRINT-AUTH.Y.descr
resident.id-auth.request-type.IRIS-AUTH.SUCCESS.descr=mosip.ida.auth-request.IRIS-AUTH.Y.descr
resident.id-auth.request-type.FACE-AUTH.SUCCESS.descr=mosip.ida.auth-request.FACE-AUTH.Y.descr
resident.id-auth.request-type.STATIC-PIN-AUTH.SUCCESS.descr=mosip.ida.auth-request.STATIC-PIN-AUTH.Y.descr
resident.id-auth.request-type.STATIC-PIN-STORAGE.SUCCESS.descr=mosip.ida.auth-request.STATIC-PIN-STORAGE.Y.descr
resident.id-auth.request-type.EKYC-AUTH.SUCCESS.descr=mosip.ida.auth-request.EKYC-AUTH.Y.descr
resident.id-auth.request-type.KYC-AUTH.SUCCESS.descr=mosip.ida.auth-request.KYC-AUTH.Y.descr
resident.id-auth.request-type.KYC-EXCHANGE.SUCCESS.descr=mosip.ida.auth-request.KYC-EXCHANGE.Y.descr
resident.id-auth.request-type.IDENTITY-KEY-BINDING.SUCCESS.descr=mosip.ida.auth-request.IDENTITY-KEY-BINDING.Y.descr
resident.id-auth.request-type.TOKEN-REQUEST.SUCCESS.descr=mosip.ida.auth-request.TOKEN-REQUEST.Y.descr
resident.id-auth.request-type.TOKEN-AUTH.SUCCESS.descr=mosip.ida.auth-request.TOKEN-AUTH.Y.descr
resident.id-auth.request-type.UNKNOWN.SUCCESS.descr=mosip.ida.auth-request.UNKNOWN.Y.descr
resident.id-auth.request-type.OTP-REQUEST.FAILED.descr=mosip.ida.auth-request.OTP-REQUEST.N.descr
resident.id-auth.request-type.OTP-AUTH.FAILED.descr=mosip.ida.auth-request.OTP-AUTH.N.descr
resident.id-auth.request-type.DEMO-AUTH.FAILED.descr=mosip.ida.auth-request.DEMO-AUTH.N.descr
resident.id-auth.request-type.FINGERPRINT-AUTH.FAILED.descr=mosip.ida.auth-request.FINGERPRINT-AUTH.N.descr
resident.id-auth.request-type.IRIS-AUTH.FAILED.descr=mosip.ida.auth-request.IRIS-AUTH.N.descr
resident.id-auth.request-type.FACE-AUTH.FAILED.descr=mosip.ida.auth-request.FACE-AUTH.N.descr
resident.id-auth.request-type.STATIC-PIN-AUTH.FAILED.descr=mosip.ida.auth-request.STATIC-PIN-AUTH.N.descr
resident.id-auth.request-type.STATIC-PIN-STORAGE.FAILED.descr=mosip.ida.auth-request.STATIC-PIN-STORAGE.N.descr
resident.id-auth.request-type.EKYC-AUTH.FAILED.descr=mosip.ida.auth-request.EKYC-AUTH.N.descr
resident.id-auth.request-type.KYC-AUTH.FAILED.descr=mosip.ida.auth-request.KYC-AUTH.N.descr
resident.id-auth.request-type.KYC-EXCHANGE.FAILED.descr=mosip.ida.auth-request.KYC-EXCHANGE.N.descr
resident.id-auth.request-type.IDENTITY-KEY-BINDING.FAILED.descr=mosip.ida.auth-request.IDENTITY-KEY-BINDING.N.descr
resident.id-auth.request-type.TOKEN-REQUEST.FAILED.descr=mosip.ida.auth-request.TOKEN-REQUEST.N.descr
resident.id-auth.request-type.TOKEN-AUTH.FAILED.descr=mosip.ida.auth-request.TOKEN-AUTH.N.descr
resident.id-auth.request-type.UNKNOWN.FAILED.descr=mosip.ida.auth-request.UNKNOWN.N.descrDefine property name in below format- resident.auth-type-code.<authTypeCode>.code
resident.auth-type-code.OTP-REQUEST.code=mosip.auth-type-code.OTP-REQUEST
resident.auth-type-code.OTP-AUTH.code=mosip.auth-type-code.OTP-AUTH
resident.auth-type-code.DEMO-AUTH.code=mosip.auth-type-code.DEMO-AUTH
resident.auth-type-code.FINGERPRINT-AUTH.code=mosip.auth-type-code.FINGERPRINT-AUTH
resident.auth-type-code.IRIS-AUTH.code=mosip.auth-type-code.IRIS-AUTH
resident.auth-type-code.FACE-AUTH.code=mosip.auth-type-code.FACE-AUTH
resident.auth-type-code.STATIC-PIN-AUTH.code=mosip.auth-type-code.STATIC-PIN-AUTH
resident.auth-type-code.STATIC-PIN-STORAGE.code=mosip.auth-type-code.STATIC-PIN-STORAGE
resident.auth-type-code.EKYC-AUTH.code=mosip.auth-type-code.EKYC-AUTH
resident.auth-type-code.KYC-AUTH.code=mosip.auth-type-code.KYC-AUTH
resident.auth-type-code.KYC-EXCHANGE.code=mosip.auth-type-code.KYC-EXCHANGE
resident.auth-type-code.IDENTITY-KEY-BINDING.code=mosip.auth-type-code.IDENTITY-KEY-BINDING
resident.auth-type-code.TOKEN-REQUEST.code=mosip.auth-type-code.TOKEN-REQUEST
resident.auth-type-code.TOKEN-AUTH.code=mosip.auth-type-code.TOKEN-AUTH
resident.auth-type-code.PWD.code=mosip.auth-type-code.PWD
resident.auth-type-code.PIN.code=mosip.auth-type-code.PIN
resident.auth-type-code.OTP.code=mosip.auth-type-code.OTP
resident.auth-type-code.Wallet.code=mosip.auth-type-code.Wallet
resident.auth-type-code.L1-bio-device.code=mosip.auth-type-code.L1-bio-deviceBelow property will retrieve VID when requested. Default is false so, UIN will be retrieved. Endpoints using below property- /individualId/otp, /aid/status.
resident.flag.use-vid-only=trueCommenting or removing this property will disable reference validator.
mosip.kernel.idobjectvalidator.referenceValidator=io.mosip.kernel.idobjectvalidator.impl.IdObjectReferenceValidatorFor validating request time as per before & after time limit (in seconds) in contact-details/update API.
resident.future.time.limit=60
resident.past.time.limit=60The java.time.format.FormatStyle enum to use for date time formatting based on locale. Allowed values with examples are:
FULL ('Tuesday, April 12, 1952 AD' or '3:30:42pm PST')
LONG('January 12, 1952')
MEDIUM ('Jan 12, 1952')
SHORT ('12.13.52' or '3:30pm')
Current value is MEDUIM. For more details refer to the enum.
resident.date.time.formmatting.style=MEDIUM
resident.date.time.replace.special.chars={" ": "_", "," : "", ":" : "."}resident.cache.expiry.time.millisec.templateCache=86400000
resident.cache.expiry.time.millisec.partnerCache=86400000
resident.cache.expiry.time.millisec.getValidDocumentByLangCode=86400000
resident.cache.expiry.time.millisec.getLocationHierarchyLevelByLangCode=86400000
resident.cache.expiry.time.millisec.getImmediateChildrenByLocCodeAndLangCode=86400000
resident.cache.expiry.time.millisec.getLocationDetailsByLocCodeAndLangCode=86400000
resident.cache.expiry.time.millisec.getCoordinateSpecificRegistrationCenters=86400000
resident.cache.expiry.time.millisec.getApplicantValidDocument=86400000
resident.cache.expiry.time.millisec.getRegistrationCentersByHierarchyLevel=86400000
resident.cache.expiry.time.millisec.getRegistrationCenterByHierarchyLevelAndTextPaginated=86400000
resident.cache.expiry.time.millisec.getRegistrationCenterWorkingDays=86400000
resident.cache.expiry.time.millisec.getLatestIdSchema=86400000
resident.cache.expiry.time.millisec.getGenderCodeByGenderTypeAndLangCode=86400000
resident.cache.expiry.time.millisec.getDocumentTypesByDocumentCategoryAndLangCode=86400000
resident.cache.expiry.time.millisec.getDynamicFieldBasedOnLangCodeAndFieldName=86400000
resident.cache.expiry.time.millisec.getCenterDetails=86400000
resident.cache.expiry.time.millisec.getImmediateChildrenByLocCode=86400000
resident.cache.expiry.time.millisec.getLocationHierarchyLevels=86400000
resident.cache.expiry.time.millisec.getAllDynamicFieldByName=86400000
resident.cache.expiry.time.millisec.getNameValueFromIdentityMapping=86400000Usage: resident.attribute.separator.<attribute>=<separator string>
resident.attribute.separator.fullAddress=, Async thread for audit calls. Limit the number of async threads created in Resident services. This count is divided into 4 thread groups configured in 'io.mosip.resident.config.Config' class.
mosip.resident.async-core-pool-size=100
mosip.resident.async-max-pool-size=100This property is used in all downloaded PDF files.
mosip.pdf.header.logo.url=https://mosip.io/images/mosipn-logo.pngThese properties are used in reg-center feature for map zoom in & out.
mosip.resident.zoom=14
mosip.resident.maxZoom=18
mosip.resident.minZoom=5Transliteration work around property since eng to fra directly is not supported in icu4j.This can be added for any other unsupported language also.
For example, resident-transliteration-workaround-for-<fromLanguageCode>-<toLanguageCode> = fromLanguageCode-intermediateLanguageCode-toLanguageCode.
For this, intermediate language code transliteration should work in both ways.
resident-transliteration-workaround-for-eng-fra=eng-hin,hin-fra
resident-transliteration-workaround-for-eng-spa=eng-hin,hin-spaThis is a policy url to fetch delimeter to download card after updating uin.
mosip.resident.reg-processer-credential-partner-policy-url=${config.server.file.storage.uri}registration-processor-credential-partners.jsonmosip.resident.api.id.otp.request=mosip.identity.otp.internal
mosip.resident.api.id.auth=mosip.identity.auth.internal
auth.internal.id=mosip.identity.auth.internal
mosip.registration.processor.print.id=mosip.registration.print
vid.create.id=mosip.vid.create
resident.vid.id=mosip.resident.vid
resident.vid.id.generate=mosip.resident.vid.generate
resident.vid.policy.id=mosip.resident.vid.policy
resident.vid.get.id=mosip.resident.vid.get
auth.type.status.id=mosip.identity.authtype.status.update
resident.authlock.id=mosip.resident.authlock
resident.checkstatus.id=mosip.resident.checkstatus
resident.euin.id=mosip.resident.euin
resident.printuin.id=mosip.resident.printuin
resident.uin.id=mosip.resident.uin
resident.rid.id=mosip.resident.rid
resident.updateuin.id=mosip.resident.updateuin
resident.authunlock.id=mosip.resident.authunlock
resident.authhistory.id=mosip.resident.authhistory
resident.authLockStatusUpdateV2.id=mosip.resident.auth.lock.unlock
resident.service.history.id=mosip.service.history.get
resident.document.upload.id=mosip.resident.document.upload
resident.document.get.id=mosip.resident.document.get
resident.document.list.id=mosip.resident.document.list
resident.service.pin.status.id=mosip.resident.pin.status
resident.service.unpin.status.id=mosip.resident.unpin.status
resident.document.delete.id=mosip.resident.document.delete
resident.contact.details.update.id=mosip.resident.contact.details.update.id
resident.contact.details.send.otp.id=mosip.resident.contact.details.send.otp.id
mosip.resident.service.status.check.id=mosip.registration.external.status
resident.service.unreadnotificationlist.id=mosip.resident.service.history.unread
resident.service.event.id=mosip.resident.event.status
resident.identity.info.id=mosip.resident.identity.info
resident.share.credential.id=mosip.resident.share.credential
vid.revoke.id=mosip.vid.update
resident.revokevid.id=mosip.resident.vidstatus
mosip.resident.revokevid.id=mosip.resident.vid.revoke
mosip.resident.grievance.ticket.request.id=mosip.resident.grievance.ticket.request
resident.channel.verification.status.id=mosip.resident.channel.verification.status
resident.event.ack.download.id=mosip.resident.event.ack.download
resident.download.card.eventid.id =mosip.resident.download.card.eventid
mosip.resident.request.vid.card.id=mosip.resident.request.vid.card
mosip.credential.request.service.id=mosip.credential.request.service.id
mosip.resident.checkstatus.individualid.id=mosip.resident.check-stage-status
mosip.resident.download.personalized.card.id=mosip.resident.download.personalized.card
mosip.resident.transliteration.transliterate.id=mosip.resident.transliteration.transliterate
resident.ui.properties.id=resident.ui.properties
mosip.resident.identity.auth.internal.id=mosip.identity.auth.internal
mosip.resident.user.profile.id=mosip.resident.profile
resident.download.reg.centers.list.id=mosip.resident.download.reg.centers.list
resident.download.nearest.reg.centers.id=mosip.resident.download.nearest.reg.centers
resident.download.supporting.documents.id=mosip.resident.download.supporting.documents
resident.send.card.id=mosip.resident.send.card
resident.pinned.eventid.id=mosip.resident.pinned.eventid
resident.unpinned.eventid.id=mosip.resident.unpinned.eventid
resident.auth.proxy.partners.id=mosip.resident.auth.proxy.partners
resident.events.eventid.id=mosip.resident.events.eventid
resident.notification.id=mosip.resident.notification.get
resident.profile.id=mosip.resident.profile.get
resident.notification.click.id=mosip.resident.notification.click
mosip.credential.store.id=mosip.credential.store
resident.vids.id=mosip.resident.vids.get
mosip.resident.download.uin.card=mosip.resident.download.uin.card
mosip.registration.processor.registration.sync.id=mosip.registration.sync
id.repo.update=mosip.id.update
mosip.resident.get.pending.drafts=mosip.resident.get.pending.drafts
mosip.resident.discard.pending.drafts=mosip.resident.discard.pending.draftsmosip.resident.api.version.otp.request=1.0
mosip.resident.api.version.auth=1.0
auth.internal.version=1.0
mosip.registration.processor.application.version=1.0
mosip.resident.create.vid.version=v1
resident.vid.version=v1
resident.vid.version.new=1.0
resident.revokevid.version=v1
resident.revokevid.version.new=1.0
resident.version.new=1.0
resident.checkstatus.version=v1
resident.authLockStatusUpdateV2.version=1.0
resident.service.history.version=1.0
resident.document.get.version=1.0
resident.document.list.version=1.0
resident.service.pin.status.version=v1
resident.service.unpin.status.version=v1
resident.document.delete.version=1.0
mosip.resident.service.status.check.version=1.0
resident.service.event.version=1.0
resident.identity.info.version=1.0
resident.share.credential.version=1.0
mosip.resident.request.response.version=1.0
mosip.resident.grievance.ticket.request.version=1.0
resident.channel.verification.status.version=1.0
resident.event.ack.download.version=1.0
resident.download.card.eventid.version=1.0
mosip.resident.request.vid.card.version=1.0
mosip.credential.request.service.version=1.0
mosip.resident.checkstatus.individualid.version=1.0
resident.ui.properties.version=1.0
mosip.resident.get.pending.drafts.version=1.0
mosip.resident.discard.pending.drafts.version=1.0IDA_INTERNAL=${mosip.ida.internal.url}/idauthentication/v1/internal
INTERNALAUTH=${IDA_INTERNAL}/auth
INTERNALAUTHTRANSACTIONS=${IDA_INTERNAL}/authTransactions
KERNELENCRYPTIONSERVICE=${IDA_INTERNAL}/getCertificate
OTP_GEN_URL=${IDA_INTERNAL}/otp
KERNELAUTHMANAGER=${mosip.kernel.authmanager.url}/v1/authmanager/authenticate/clientidsecretkeyCREDENTIAL_STATUS_URL=${mosip.idrepo.credrequest.generator.url}/v1/credentialrequest/get/
CREDENTIAL_REQ_URL=${mosip.idrepo.credrequest.generator.url}/v1/credentialrequest/requestgenerator
CREDENTIAL_CANCELREQ_URL=${mosip.idrepo.credrequest.generator.url}/v1/credentialrequest/cancel/
CREDENTIAL_TYPES_URL=${mosip.idrepo.credential.service.url}/v1/credentialservice/typesIDREPO_IDENTITY=${mosip.idrepo.identity.url}/idrepository/v1/identity
IDREPOSITORY=${IDREPO_IDENTITY}/
IDREPOGETIDBYUIN=${IDREPO_IDENTITY}/idvid
IDREPOGETIDBYRID=${IDREPO_IDENTITY}/idvid
IDREPO_IDENTITY_URL=${IDREPO_IDENTITY}/idvid/{id}
GET_RID_BY_INDIVIDUAL_ID=${IDREPO_IDENTITY}/rid/{individualId}
IDREPO_IDENTITY_UPDATE_COUNT=${IDREPO_IDENTITY}/{individualId}/update-counts
AUTHTYPESTATUSUPDATE=${IDREPO_IDENTITY}/authtypes/status
IDREPO_IDENTITY_GET_DRAFT_UIN=${IDREPO_IDENTITY}/draft/uin/{UIN}
IDREPO_IDENTITY_DISCARD_DRAFT=${IDREPO_IDENTITY}/draft/discard/IDREPO_VID=${mosip.idrepo.vid.url}/idrepository/v1/vid
CREATEVID=${IDREPO_VID}
GETUINBYVID=${IDREPO_VID}
IDAUTHCREATEVID=${IDREPO_VID}
IDAUTHREVOKEVID=${IDREPO_VID}
RETRIEVE_VIDS=${IDREPO_VID}/uin/KEYMANAGER=${mosip.kernel.keymanager.url}/v1/keymanager
ENCRYPTURL=${KEYMANAGER}/encrypt
DECRYPT_API_URL=${KEYMANAGER}/decrypt
mosip.resident.keymanager.encrypt-uri=${KEYMANAGER}/encrypt
mosip.resident.keymanager.decrypt-uri=${KEYMANAGER}/decrypt
PACKETSIGNPUBLICKEY=${KEYMANAGER}/tpmsigning/publickey
mosip.keymanager.jwt.sign.end.point=${KEYMANAGER}/jwtSign
PDFSIGN=${KEYMANAGER}/pdf/signMASTER=${mosip.kernel.masterdata.url}/v1/masterdata
TEMPLATES=${MASTER}/templates
MACHINEDETAILS=${MASTER}/machines
MACHINESEARCH=${MASTER}/machines/search
MACHINECREATE=${MASTER}/machines
CENTERDETAILS=${MASTER}/registrationcenters
VALID_DOCUMENT_BY_LANGCODE_URL=${MASTER}/validdocuments/{langCode}
LOCATION_HIERARCHY_LEVEL_BY_LANGCODE_URL=${MASTER}/locationHierarchyLevels/{langcode}
LOCATION_HIERARCHY=${MASTER}/locationHierarchyLevels
IMMEDIATE_CHILDREN_BY_LOCATIONCODE_AND_LANGCODE_URL=${MASTER}/locations/immediatechildren/{locationcode}/{langcode}
LOCATION_INFO_BY_LOCCODE_AND_LANGCODE_URL=${MASTER}/locations/info/{locationcode}/{langcode}
IMMEDIATE_CHILDREN_BY_LOCATION_CODE=${MASTER}/locations/immediatechildren
REGISTRATION_CENTER_FOR_LOCATION_CODE_URL=${MASTER}/registrationcenters/{langcode}/{hierarchylevel}/names
REGISTRATION_CENTER_BY_LOCATION_TYPE_AND_SEARCH_TEXT_PAGINATED_URL=${MASTER}/registrationcenters/page/{langcode}/{hierarchylevel}/{name}
COORDINATE_SPECIFIC_REGISTRATION_CENTERS_URL=${MASTER}/getcoordinatespecificregistrationcenters/{langcode}/{longitude}/{latitude}/{proximitydistance}
APPLICANT_VALID_DOCUMENT_URL=${MASTER}/applicanttype/{applicantId}/languages
WORKING_DAYS_BY_REGISTRATION_ID=${MASTER}/workingdays/{registrationCenterID}/{langCode}
LATEST_ID_SCHEMA_URL =${MASTER}/idschema/latest
TEMPLATES_BY_LANGCODE_AND_TEMPLATETYPECODE_URL=${MASTER}/templates/{langcode}/{templatetypecode}
DYNAMIC_FIELD_BASED_ON_LANG_CODE_AND_FIELD_NAME=${MASTER}/dynamicfields/{fieldName}/{langcode}
DYNAMIC_FIELD_BASED_ON_FIELD_NAME=${MASTER}/dynamicfields/{fieldName}
DOCUMENT_TYPE_BY_DOCUMENT_CATEGORY_AND_LANG_CODE=${MASTER}/documenttypes/{documentcategorycode}/{langcode}SMSNOTIFIER=${mosip.kernel.notification.url}/v1/notifier/sms/send
EMAILNOTIFIER=${mosip.kernel.notification.url}/v1/notifier/email/send
[email protected]
resident.notification.message=Notification has been sent to the provided contact detail(s)PMS_PARTNER_MANAGER=${mosip.pms.partnermanager.url}/v1/partnermanager
POLICY_REQ_URL=${PMS_PARTNER_MANAGER}/partners/{partnerId}/credentialtype/{credentialType}/policies
PARTNER_API_URL=${PMS_PARTNER_MANAGER}/partners
PARTNER_DETAILS_NEW_URL=${PMS_PARTNER_MANAGER}/partners/v2
mosip.pms.pmp.partner.rest.uri=${PMS_PARTNER_MANAGER}/partners?partnerType=${mosip.ida.partner.type}REGPROCPRINT=http://regproc-group7.regproc/registrationprocessor/v1/print/uincard
SYNCSERVICE=${mosip.regproc.status.service.url}/registrationprocessor/v1/registrationstatus/sync
PACKETRECEIVER=${mosip.packet.receiver.url}/registrationprocessor/v1/packetreceiver/registrationpackets
GET_RID_STATUS=${mosip.regproc.transaction.service.url}/registrationprocessor/v1/registrationtransaction/search/{rid}
REGISTRATIONSTATUSSEARCH=${mosip.regproc.status.service.url}/registrationprocessor/v1/registrationstatus/externalstatus/searchmosip.service-context=${server.servlet.context-path}
RESIDENT_SERVICE=${mosip.resident.url}${mosip.service-context}
RESIDENT_REQ_CREDENTIAL_URL=${RESIDENT_SERVICE}/req/credential/status/
GET_ORDER_STATUS_URL=${RESIDENT_SERVICE}/mock/print-partner/check-order-status
mosip.resident.download-card.url=${mosip.api.public.url}${mosip.service-context}/download-card/event/{eventId}
mosip.resident.grievance.url=${mosip.api.public.url}${mosip.service-context}/mock/external/grievance/redressel?name={name}&emailId={email}&phoneNo={phone}&eventId={eventId}MIDSCHEMAURL=${mosip.kernel.syncdata.url}/v1/syncdata/latestidschema
DIGITAL_CARD_STATUS_URL=${mosip.digitalcard.service.url}/v1/digitalcard/
RIDGENERATION=${mosip.kernel.ridgenerator.url}/v1/ridgenerator/generate/rid
otp-generate.rest.uri=${mosip.kernel.otpmanager.url}/v1/otpmanager/otp/generate
mosip.resident.service.mock.pdf.url=https://uidai.gov.in/images/New_eAadhaar1.pdf
mosip.kernel.masterdata.audit-url=${mosip.kernel.auditmanager.url}/v1/auditmanager/auditsBelow config is used to get identity mapping and get remaining update count for the Identity Attributes .
This is used in Resident in Update UIN feature to show remaining update count for the Identity Attribute.
{
"identity": {
"IDSchemaVersion": {
"value": "IDSchemaVersion"
},
"selectedHandles" : {
"value" : "selectedHandles"
},
"name": {
"value": "fullName"
},
"gender": {
"value": "gender"
},
"dob": {
"value": "dateOfBirth"
},
"age": {
"value": "age"
},
"introducerRID": {
"value": "introducerRID"
},
"introducerUIN": {
"value": "introducerUIN"
},
"introducerVID": {
"value": "introducerVID"
},
"introducerName": {
"value": "introducerName"
},
"phone": {
"value": "phone"
},
"phoneNumber": {
"value": "phone"
},
"email": {
"value": "email"
},
"emailId": {
"value": "email"
},
"uin": {
"value": "UIN"
},
"vid": {
"value": "VID"
},
"individualBiometrics": {
"value": "individualBiometrics"
},
"introducerBiometrics": {
"value": "introducerBiometrics"
},
"individualAuthBiometrics": {
"value": "individualAuthBiometrics"
},
"officerBiometricFileName": {
"value": "officerBiometricFileName"
},
"supervisorBiometricFileName": {
"value": "supervisorBiometricFileName"
},
"residenceStatus": {
"value": "residenceStatus"
},
"preferredLanguage": {
"value": "preferredLang"
},
"locationHierarchyForProfiling": {
"value": "zone,postalCode"
},
"addressLine1": {
"value": "addressLine1"
},
"addressLine2": {
"value": "addressLine2"
},
"addressLine3": {
"value": "addressLine3"
},
"location1": {
"value": "city"
},
"location2": {
"value": "region"
},
"location3": {
"value": "province"
},
"postalCode": {
"value": "postalCode"
},
"location4": {
"value": "zone"
},
"fullAddress": {
"value": "addressLine1,addressLine2,addressLine3,city,region,province,postalCode"
},
"bestTwoFingers": {
"value": "bestTwoFingers"
},
"birthdate": {
"value": "dateOfBirth"
},
"picture": {
"value": "face"
},
"phone_number": {
"value": "phone"
},
"address": {
"value": "addressLine1,addressLine2,addressLine3,city,region,province,postalCode"
},
"individual_id": {
"value": "individual_id"
},
"attributes": {
"value": "fln,ad1,ad2,ad3,cit,reg,pro,poc,cph,em,ph,gen,dob"
},
"street_address": {
"value": "addressLine1,addressLine2,addressLine3"
},
"locality": {
"value": "city"
},
"region": {
"value": "region"
},
"postal_code": {
"value": "postalCode"
},
"country": {
"value": "province"
},
"password": {
"value": "password"
}
},
"metaInfo": {
"value": "metaInfo"
},
"audits": {
"value": "audits"
},
"documents": {
"poa": {
"value": "proofOfAddress"
},
"poi": {
"value": "proofOfIdentity"
},
"por": {
"value": "proofOfRelationship"
},
"pob": {
"value": "proofOfDateOfBirth"
},
"poe": {
"value": "proofOfException"
}
},
"attributeUpdateCountLimit": {
"fullName": 2,
"gender": 4,
"dateOfBirth": 3
}
}This file contains Mvel method definitions for masking attributes, getting passwords, and formatting attributes.
This is used in Resident for downloading PDF cards and for masking attributes in the share credential feature and personalize card feature.